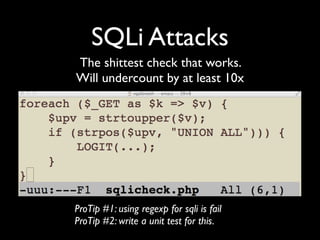
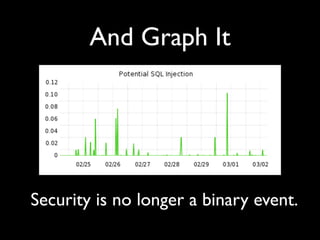
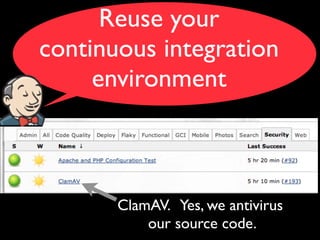
DevOpsSec applies DevOps principles like decentralization, shared resources, and transparency to security. It focuses on reducing the mean time to detect (MTTD) security issues and mean time to resolve (MTTR) them. Automating security testing and integrating it into continuous integration helps detect attacks and issues earlier. Treating security operations like other services improves culture.