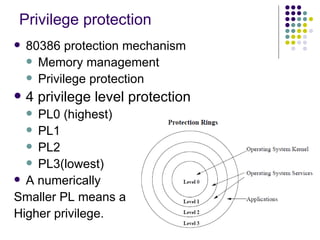
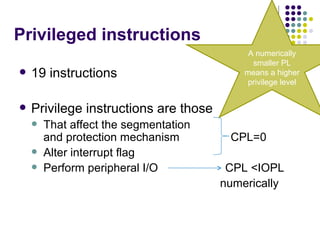
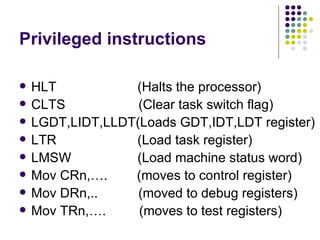
The document discusses privilege levels and segmentation protection in Intel 80386 processors. It describes four privilege levels (PL0 highest to PL3 lowest) and how privilege levels determine what instructions and data a program can access. Programs can only reference data with an equal or higher privilege level and transfer control to code with the same privilege level. Segment descriptors in the Global Descriptor Table and Local Descriptor Tables define privilege levels and other properties of segments.