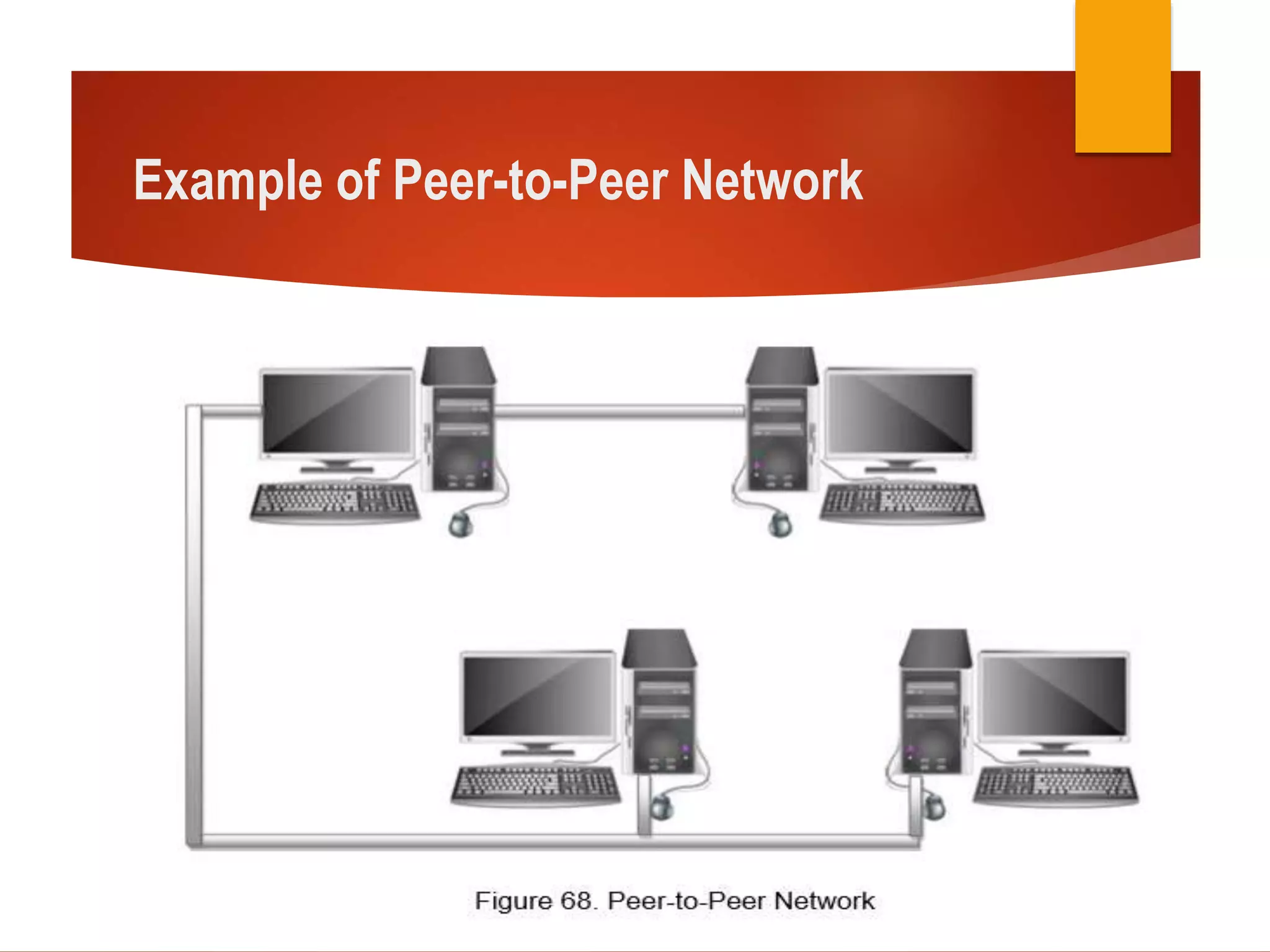
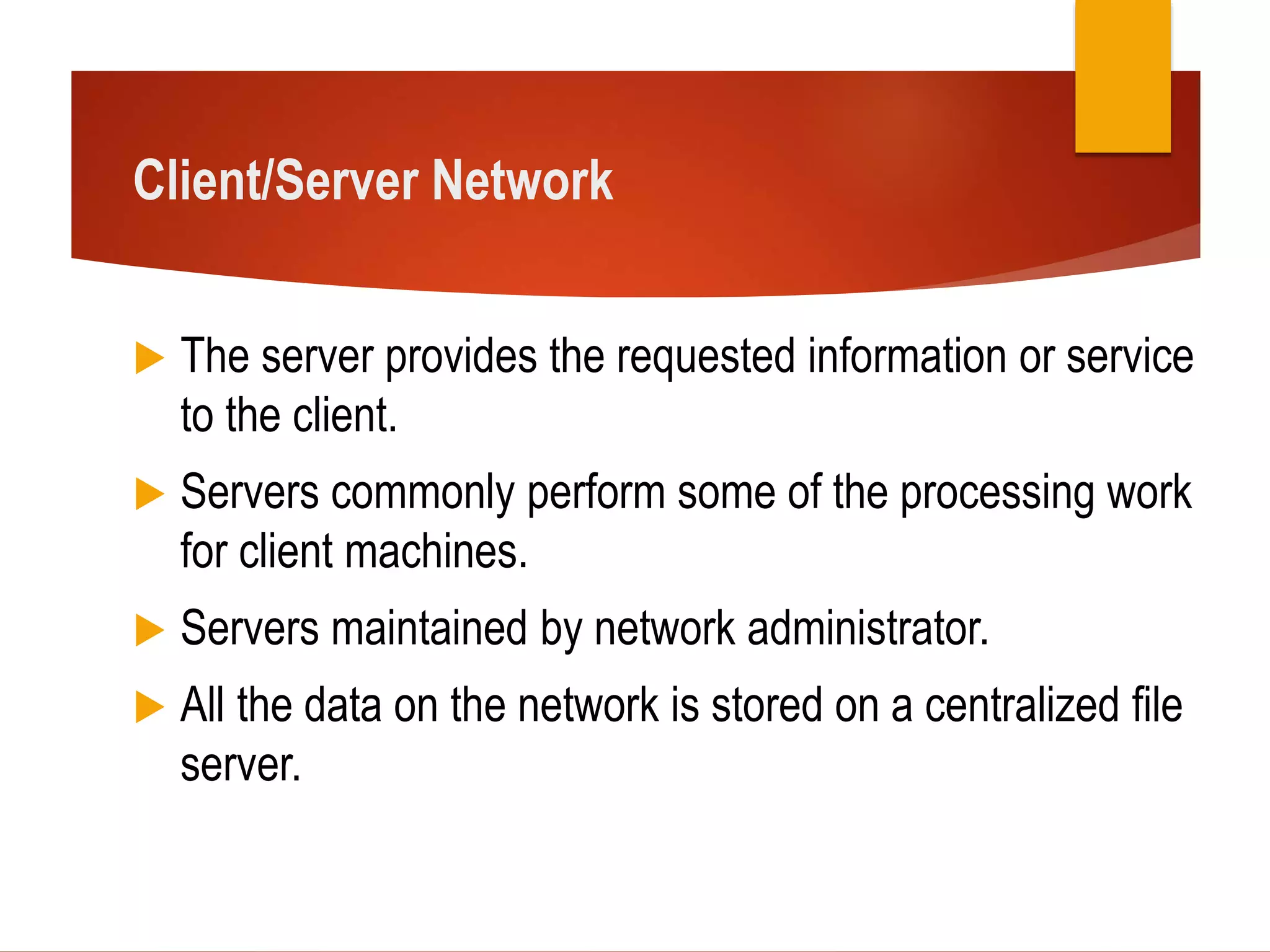
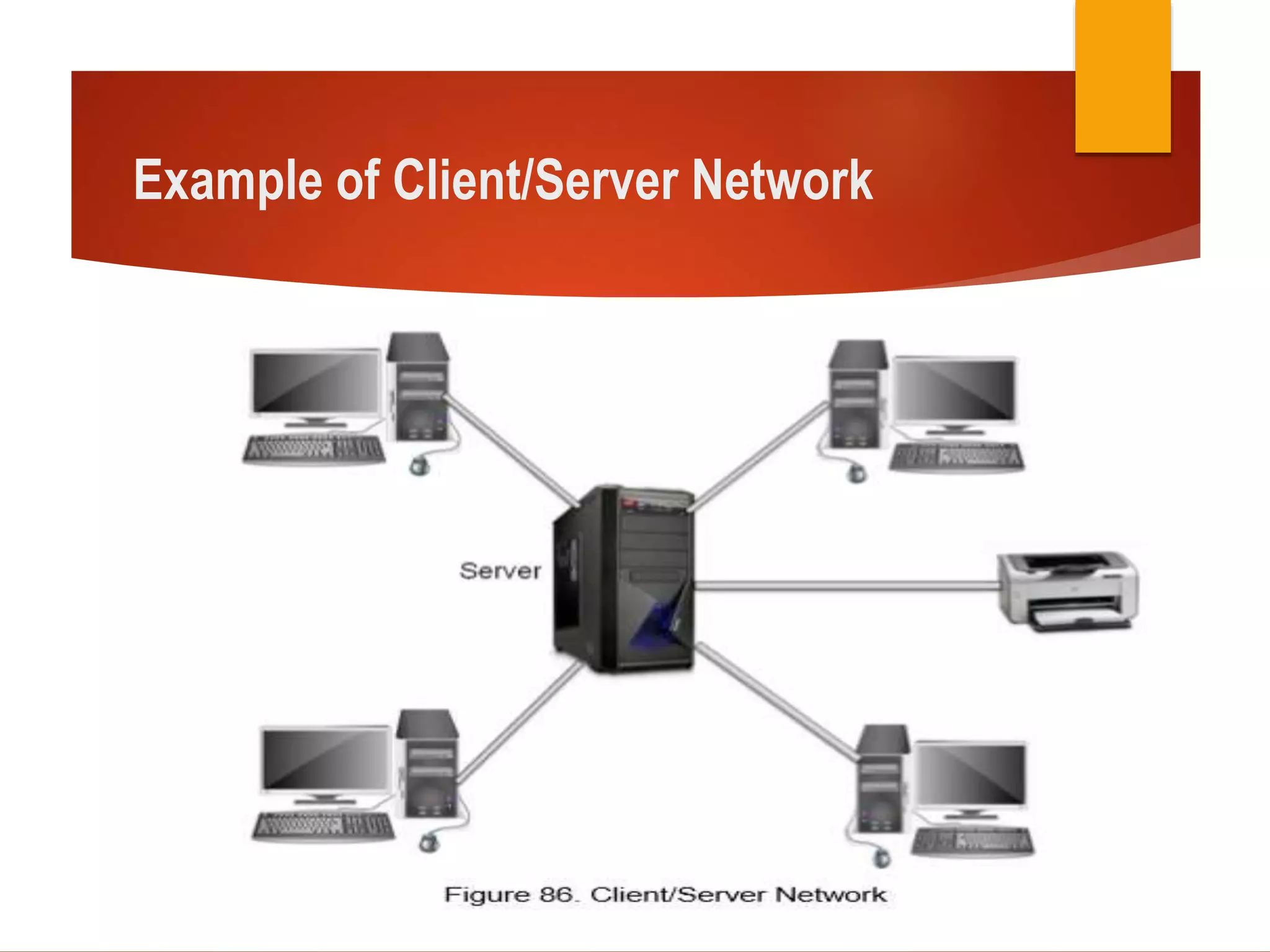
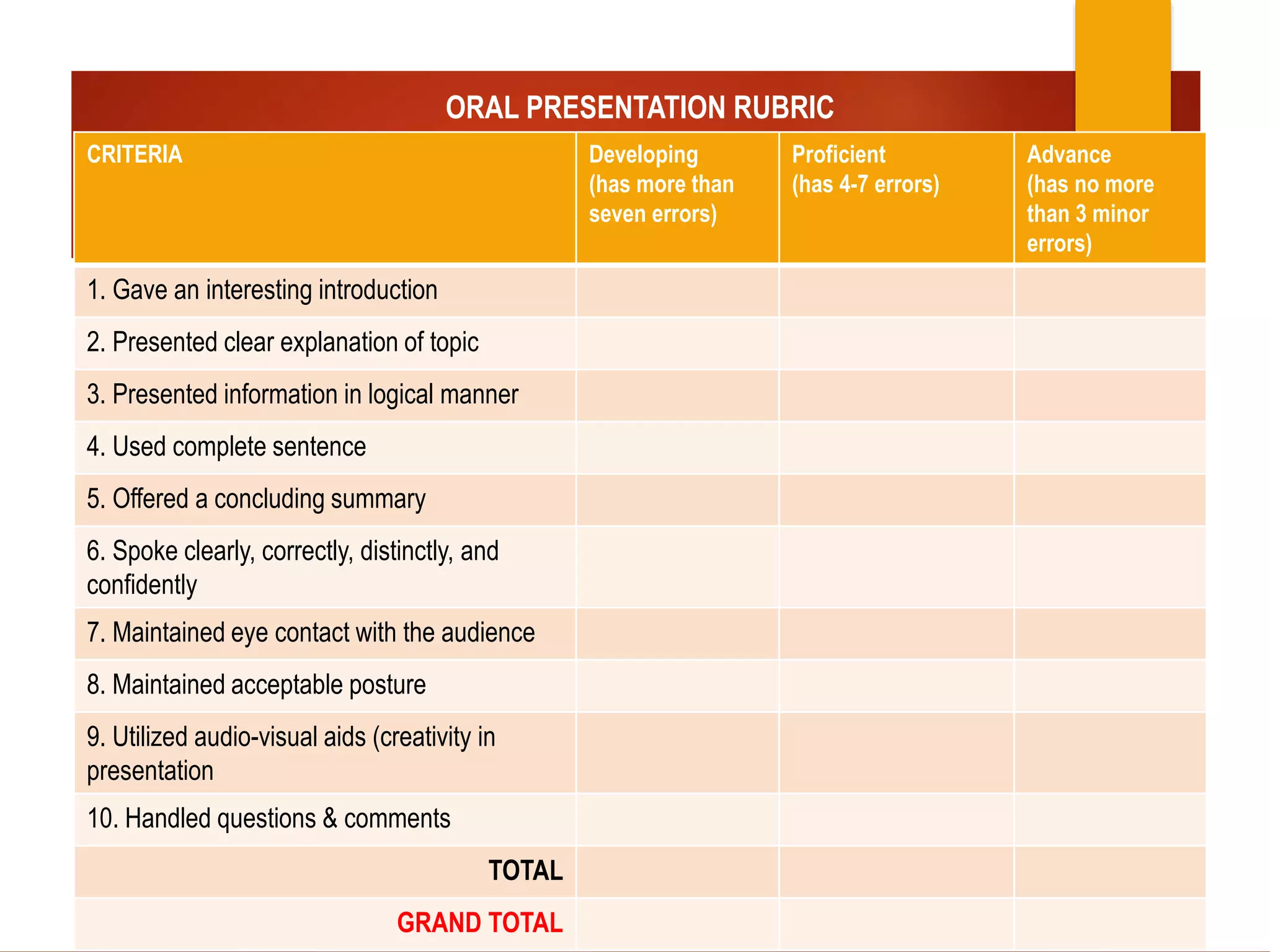
This document provides information about peer-to-peer and client/server networks. A peer-to-peer network connects devices directly without additional networking devices between them. The devices have equivalent capabilities and responsibilities, and there is no central control. This allows users to share files with others on the network. A client/server network has a server that provides information and services to client machines. All data is stored centrally on a file server, and access is controlled by usernames and passwords. The document instructs students to research and present on the advantages and disadvantages of each type of network. It provides rubrics to evaluate their research and oral presentation skills.