Peer to peer
•Download as PPTX, PDF•
7 likes•9,151 views
The document compares peer-to-peer and client-server networks. In peer-to-peer networks, all computers share equal responsibility for processing data, while in client-server networks certain devices serve data and others act as clients. Peer-to-peer networks are commonly used for home networks and allow easy sharing of files and printers between devices. However, peer-to-peer networks can slow performance and lack centralized backup and security. Client-server networks have more advanced security, centralized data storage, and mature technologies, but if the server crashes all connected devices cannot access resources.
Report
Share
Report
Share
Recommended
Peer To Peer Networking

An introduction to Peer to Peer Networking. Includes different P2P Architectures, advantages and applications.
Types of server

it is all about types of server. And in this file defines all the types of servers and detail of all type. And after this you will be able to know about all server types and details of these servers.
Introduction to computer network

A computer network is defined as the interconnection of two or more computers. It is done to enable the computers to communicate and share available resources.
Components of computer network
Network benefits
Disadvantages of computer network
Classification by their geographical area
Network classification by their component role
Types of servers
Recommended
Peer To Peer Networking

An introduction to Peer to Peer Networking. Includes different P2P Architectures, advantages and applications.
Types of server

it is all about types of server. And in this file defines all the types of servers and detail of all type. And after this you will be able to know about all server types and details of these servers.
Introduction to computer network

A computer network is defined as the interconnection of two or more computers. It is done to enable the computers to communicate and share available resources.
Components of computer network
Network benefits
Disadvantages of computer network
Classification by their geographical area
Network classification by their component role
Types of servers
An introduction to networking

Introduction to networking. Types of the network. LAN, WAN, MAN Internet, Intranet differences.
Networking Devices

This presentation provides a brief knowledge about various networking devices and there respective illustrations
System and network administration network services

System and network administration network services
Remote desktop connection

With Remote Desktop Connection, you can connect to a computer running Windows from another computer running Windows that's connected to the same network or to the Internet. For example, you can use all of your work computer's programs, files, and network resources from your home computer, and it's just like you're sitting in front of your computer at work.
To connect to a remote computer, that computer must be turned on, it must have a network connection, Remote Desktop must be enabled, you must have network access to the remote computer (this could be through the Internet), and you must have permission to connect. For permission to connect, you must be on the list of users. Before you start a connection, it's a good idea to look up the name of the computer you're connecting to and to make sure Remote Desktop connections are allowed through its firewall.
To find the Remote Desktop Connection shortcut, click the Start button Start button, click All Programs, and then click Accessories. To quickly open Remote Desktop Connection, click the Start button Start button, type mstsc in the search box, and then press Enter.
Redirecting a device on your computer makes it available for use in a Remote Desktop session. If a Remote Desktop Connection dialog box appears after you click Connect and enter your credentials, you can redirect local devices and resources, such as your local drives or Clipboard. Click Details, and then select the check box for each item you want to redirect.
Ports and protocols

This document contains the ports and description of the protocols that are used in TCP/UDP.
Computer Networking fundamentals 

#network #types of network
COMPUTER NETWORKING FUNDAMENTALS
SLIDE PPT CONSIST OF
definition,its components,advantages,Disadvantages,switching techniques,network architectures, and Types of Networks.
If you are interested in computer networking and more topics related to computers.
Must watch my youtube channel TECHISEASY
Common Network Services

The slides contains a detail material about the services of networks(Common) in Data Communication
Domain Name System ppt

The Domain Name System (DNS) is basically a large database which resides on various computers
Computer Networking - Its Advantages & Disadvantages

It will help you to learn about computer network, how it works and what are its merits and demerits.
Peer-to-Peer Systems

Peer-to-Peer (P2P) has become a buzzword and file-sharing applications like Kazaa are very popular and account for a lot of Internet traffic nowadays. The emphasis of my talk will be on the evolution of P2P file-sharing and the technology behind the scenes. I also try to give examples how P2P can be used for other applications like Skype.
From the Un-Distinguished Lecture Series (http://ws.cs.ubc.ca/~udls/). The talk was given Feb. 16, 2007.
More Related Content
What's hot
An introduction to networking

Introduction to networking. Types of the network. LAN, WAN, MAN Internet, Intranet differences.
Networking Devices

This presentation provides a brief knowledge about various networking devices and there respective illustrations
System and network administration network services

System and network administration network services
Remote desktop connection

With Remote Desktop Connection, you can connect to a computer running Windows from another computer running Windows that's connected to the same network or to the Internet. For example, you can use all of your work computer's programs, files, and network resources from your home computer, and it's just like you're sitting in front of your computer at work.
To connect to a remote computer, that computer must be turned on, it must have a network connection, Remote Desktop must be enabled, you must have network access to the remote computer (this could be through the Internet), and you must have permission to connect. For permission to connect, you must be on the list of users. Before you start a connection, it's a good idea to look up the name of the computer you're connecting to and to make sure Remote Desktop connections are allowed through its firewall.
To find the Remote Desktop Connection shortcut, click the Start button Start button, click All Programs, and then click Accessories. To quickly open Remote Desktop Connection, click the Start button Start button, type mstsc in the search box, and then press Enter.
Redirecting a device on your computer makes it available for use in a Remote Desktop session. If a Remote Desktop Connection dialog box appears after you click Connect and enter your credentials, you can redirect local devices and resources, such as your local drives or Clipboard. Click Details, and then select the check box for each item you want to redirect.
Ports and protocols

This document contains the ports and description of the protocols that are used in TCP/UDP.
Computer Networking fundamentals 

#network #types of network
COMPUTER NETWORKING FUNDAMENTALS
SLIDE PPT CONSIST OF
definition,its components,advantages,Disadvantages,switching techniques,network architectures, and Types of Networks.
If you are interested in computer networking and more topics related to computers.
Must watch my youtube channel TECHISEASY
Common Network Services

The slides contains a detail material about the services of networks(Common) in Data Communication
Domain Name System ppt

The Domain Name System (DNS) is basically a large database which resides on various computers
Computer Networking - Its Advantages & Disadvantages

It will help you to learn about computer network, how it works and what are its merits and demerits.
What's hot (20)
System and network administration network services

System and network administration network services
Computer Networking - Its Advantages & Disadvantages

Computer Networking - Its Advantages & Disadvantages
Viewers also liked
Peer-to-Peer Systems

Peer-to-Peer (P2P) has become a buzzword and file-sharing applications like Kazaa are very popular and account for a lot of Internet traffic nowadays. The emphasis of my talk will be on the evolution of P2P file-sharing and the technology behind the scenes. I also try to give examples how P2P can be used for other applications like Skype.
From the Un-Distinguished Lecture Series (http://ws.cs.ubc.ca/~udls/). The talk was given Feb. 16, 2007.
CLOUDSEC LONDON 2016 - Puneet Kukreja - Enabling Cloud Security - 

Cloud and IoT is now in mainstream adoption phase, often being referred to as the fourth revolution. The presentation will share experiences from early adopters and focus on challenges that vendors will not share when selling cloud enablement services.
Citcism on Peer to peer networking

This document contains the critcism and suggestion on a research paper in hybrid peer to peer networking
AWS Adoption in FSI

Today Financial Services Industry organisations are using AWS to both develop new sources of customer value as well as reinventing their core. In this session we will provide insights into the successful adoption patterns and trends that have emerged. We will also discuss how organisations in the FSI space have successfully navigated the people and processes challenges that initially inhibited enterprise wide adoption. Finally, through our experience in helping enterprises navigate this change, AWS has developed the Cloud Adoption Framework (CAF) to assist with planning, creating, managing and supporting the shift. We will spend time taking you through this framework to assess where you are on your Cloud journey and tangible takeaways that will help you accelerate.
Peer to peer Networks 

What is P2P networks, history, architecture, advantages and weaknesses, Legal issues, Security and Privacy issues, Economic issues, Applications of use and Future developments (April, 2010).
BaaS-platforms and open APIs in fintech l bank-as-a-service.com

What is bank-as-a-service? And why it is so necessary for Asia-Pacific region? Download as pdf in English, Chinese, Korean and Japanese on www.bank-as-a-service.com. Read more on http://www.forbes.com/sites/vladislavsolodkiy/2016/08/03/what-asian-banks-can-learn-from-amazon-about-working-for-fintech/
Client server architecture

Understanding client server architecture(two-tier and three-tier) with fat and thin clients
Viewers also liked (15)
CLOUDSEC LONDON 2016 - Puneet Kukreja - Enabling Cloud Security - 

CLOUDSEC LONDON 2016 - Puneet Kukreja - Enabling Cloud Security -
Networking peer-to-peer-powerpoint-presentation4410 (1)

Networking peer-to-peer-powerpoint-presentation4410 (1)
BaaS-platforms and open APIs in fintech l bank-as-a-service.com

BaaS-platforms and open APIs in fintech l bank-as-a-service.com
Similar to Peer to peer
Advantages-and-Disadvantages-of-P2P-Network-Client-Server-Network.pdf

Advantages-and-Disadvantages-of-P2P-Network-Client-Server-Network
Running head SERVERS1Running head SERVERS1.docx

Running head: SERVERS 1
Running head: SERVERS 1
Debbie Utter
Colorado Technical University
Unit 3 IP
Introduction to Operating Systems and Client/Servers Environment
IT140-1503B-01
Dr. Stephan Reynolds
September 11, 2015
Peer-to-peer networks and client-server networks are both distinct networking architectures, each model being suitable for different types of organizations. The main difference between these two architectures is that in Client-server networks, there is a dedicated central computer (known as a server) and the other reliable computers (clients) dependent on the server’s resources. On the other hand, in a peer-to-peer network, each computer can act as the server and client to the others. In simpler terms, if each computer in the network can fully carry out its functions independently, then it is in a peer-to-peer network. If one computer is the go-to computer for services such as file storage or the one given the capability to grant or deny access of services to the other computers, then those computers are in a client-server network.
Peer-to-peer and client-server networks can both be differentiated using the various aspects as follows:
(a) Performance
A peer-to-peer network is only suitable for as much as 10 computers, past which performance problems will arise. An organization with more than 10 computers is best suited for a client-server network. This is because of the presence of a server that does most of the management and control duties. Also, an issue with one computer won’t necessarily interfere with the network since it’s not required to share its computing power.
(b) Cost
Client-server networks are basically more expensive than peer-to-peer networks, both in installation and maintenance. The server in client-server networks needs to have great computing power, and therefore you need have dedicated software to manage the network. An example of this software that does this job excellently is the Windows Server. Such programs are complicated to run, and so more costs may arise due to the need to have experts that fix any arising problems.
(c) Security
Client-server networks are more secure than peer-to-peer networks. The server has a function in it that can grant or reject a user’s access request to the network. This feature is important as it helps keep unwanted users, malware or malicious bots out of the network. However, it is important to note that as the more computers join the client-server network, security management becomes increasingly difficult.
(d)Geographical area
A peer-to-peer network is suitable when it is being set up in homes or small organizations. But for bigger organizations, such as hospitals, a client-server is ideal due to the need for technical functions in the organization.
Depending on the above factors, a client-server network would work best in Health Care HQ.
As earlier mentioned, Windows Server is one of the most efficient operating systems that manages client-server ne.
Networking course khurram shahzad

Watch IT course, how to make network at school or office,
Khurram Shahzad Goraya
Similar to Peer to peer (20)
Advantages-and-Disadvantages-of-P2P-Network-Client-Server-Network.pdf

Advantages-and-Disadvantages-of-P2P-Network-Client-Server-Network.pdf
Recently uploaded
Operation Blue Star - Saka Neela Tara

Operation “Blue Star” is the only event in the history of Independent India where the state went into war with its own people. Even after about 40 years it is not clear if it was culmination of states anger over people of the region, a political game of power or start of dictatorial chapter in the democratic setup.
The people of Punjab felt alienated from main stream due to denial of their just demands during a long democratic struggle since independence. As it happen all over the word, it led to militant struggle with great loss of lives of military, police and civilian personnel. Killing of Indira Gandhi and massacre of innocent Sikhs in Delhi and other India cities was also associated with this movement.
Honest Reviews of Tim Han LMA Course Program.pptx

Personal development courses are widely available today, with each one promising life-changing outcomes. Tim Han’s Life Mastery Achievers (LMA) Course has drawn a lot of interest. In addition to offering my frank assessment of Success Insider’s LMA Course, this piece examines the course’s effects via a variety of Tim Han LMA course reviews and Success Insider comments.
The French Revolution Class 9 Study Material pdf free download

The French Revolution, which began in 1789, was a period of radical social and political upheaval in France. It marked the decline of absolute monarchies, the rise of secular and democratic republics, and the eventual rise of Napoleon Bonaparte. This revolutionary period is crucial in understanding the transition from feudalism to modernity in Europe.
For more information, visit-www.vavaclasses.com
Model Attribute Check Company Auto Property

In Odoo, the multi-company feature allows you to manage multiple companies within a single Odoo database instance. Each company can have its own configurations while still sharing common resources such as products, customers, and suppliers.
How to Make a Field invisible in Odoo 17

It is possible to hide or invisible some fields in odoo. Commonly using “invisible” attribute in the field definition to invisible the fields. This slide will show how to make a field invisible in odoo 17.
CACJapan - GROUP Presentation 1- Wk 4.pdf

Macroeconomics- Movie Location
This will be used as part of your Personal Professional Portfolio once graded.
Objective:
Prepare a presentation or a paper using research, basic comparative analysis, data organization and application of economic information. You will make an informed assessment of an economic climate outside of the United States to accomplish an entertainment industry objective.
"Protectable subject matters, Protection in biotechnology, Protection of othe...

Protectable subject matters, Protection in biotechnology, Protection of other biological materials, Ownership and period of protection
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptxMohd Adib Abd Muin, Senior Lecturer at Universiti Utara Malaysia
This slide is prepared for master's students (MIFB & MIBS) UUM. May it be useful to all.How libraries can support authors with open access requirements for UKRI fund...

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
Thesis Statement for students diagnonsed withADHD.ppt

Presentation required for the master in Education.
Unit 8 - Information and Communication Technology (Paper I).pdf

This slides describes the basic concepts of ICT, basics of Email, Emerging Technology and Digital Initiatives in Education. This presentations aligns with the UGC Paper I syllabus.
Home assignment II on Spectroscopy 2024 Answers.pdf

Answers to Home assignment on UV-Visible spectroscopy: Calculation of wavelength of UV-Visible absorption
A Survey of Techniques for Maximizing LLM Performance.pptx

A Survey of Techniques for Maximizing LLM Performance
Best Digital Marketing Institute In NOIDA

Safalta Digital marketing institute in Noida, provide complete applications that encompass a huge range of virtual advertising and marketing additives, which includes search engine optimization, virtual communication advertising, pay-per-click on marketing, content material advertising, internet analytics, and greater. These university courses are designed for students who possess a comprehensive understanding of virtual marketing strategies and attributes.Safalta Digital Marketing Institute in Noida is a first choice for young individuals or students who are looking to start their careers in the field of digital advertising. The institute gives specialized courses designed and certification.
for beginners, providing thorough training in areas such as SEO, digital communication marketing, and PPC training in Noida. After finishing the program, students receive the certifications recognised by top different universitie, setting a strong foundation for a successful career in digital marketing.
Chapter -12, Antibiotics (One Page Notes).pdf

This is a notes for the D.Pharm students and related to the antibiotic drugs.
Biological Screening of Herbal Drugs in detailed.

Biological screening of herbal drugs: Introduction and Need for
Phyto-Pharmacological Screening, New Strategies for evaluating
Natural Products, In vitro evaluation techniques for Antioxidants, Antimicrobial and Anticancer drugs. In vivo evaluation techniques
for Anti-inflammatory, Antiulcer, Anticancer, Wound healing, Antidiabetic, Hepatoprotective, Cardio protective, Diuretics and
Antifertility, Toxicity studies as per OECD guidelines
June 3, 2024 Anti-Semitism Letter Sent to MIT President Kornbluth and MIT Cor...

Letter from the Congress of the United States regarding Anti-Semitism sent June 3rd to MIT President Sally Kornbluth, MIT Corp Chair, Mark Gorenberg
Dear Dr. Kornbluth and Mr. Gorenberg,
The US House of Representatives is deeply concerned by ongoing and pervasive acts of antisemitic
harassment and intimidation at the Massachusetts Institute of Technology (MIT). Failing to act decisively to ensure a safe learning environment for all students would be a grave dereliction of your responsibilities as President of MIT and Chair of the MIT Corporation.
This Congress will not stand idly by and allow an environment hostile to Jewish students to persist. The House believes that your institution is in violation of Title VI of the Civil Rights Act, and the inability or
unwillingness to rectify this violation through action requires accountability.
Postsecondary education is a unique opportunity for students to learn and have their ideas and beliefs challenged. However, universities receiving hundreds of millions of federal funds annually have denied
students that opportunity and have been hijacked to become venues for the promotion of terrorism, antisemitic harassment and intimidation, unlawful encampments, and in some cases, assaults and riots.
The House of Representatives will not countenance the use of federal funds to indoctrinate students into hateful, antisemitic, anti-American supporters of terrorism. Investigations into campus antisemitism by the Committee on Education and the Workforce and the Committee on Ways and Means have been expanded into a Congress-wide probe across all relevant jurisdictions to address this national crisis. The undersigned Committees will conduct oversight into the use of federal funds at MIT and its learning environment under authorities granted to each Committee.
• The Committee on Education and the Workforce has been investigating your institution since December 7, 2023. The Committee has broad jurisdiction over postsecondary education, including its compliance with Title VI of the Civil Rights Act, campus safety concerns over disruptions to the learning environment, and the awarding of federal student aid under the Higher Education Act.
• The Committee on Oversight and Accountability is investigating the sources of funding and other support flowing to groups espousing pro-Hamas propaganda and engaged in antisemitic harassment and intimidation of students. The Committee on Oversight and Accountability is the principal oversight committee of the US House of Representatives and has broad authority to investigate “any matter” at “any time” under House Rule X.
• The Committee on Ways and Means has been investigating several universities since November 15, 2023, when the Committee held a hearing entitled From Ivory Towers to Dark Corners: Investigating the Nexus Between Antisemitism, Tax-Exempt Universities, and Terror Financing. The Committee followed the hearing with letters to those institutions on January 10, 202
Recently uploaded (20)
The French Revolution Class 9 Study Material pdf free download

The French Revolution Class 9 Study Material pdf free download
"Protectable subject matters, Protection in biotechnology, Protection of othe...

"Protectable subject matters, Protection in biotechnology, Protection of othe...
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptx
How libraries can support authors with open access requirements for UKRI fund...

How libraries can support authors with open access requirements for UKRI fund...
Thesis Statement for students diagnonsed withADHD.ppt

Thesis Statement for students diagnonsed withADHD.ppt
Unit 8 - Information and Communication Technology (Paper I).pdf

Unit 8 - Information and Communication Technology (Paper I).pdf
Home assignment II on Spectroscopy 2024 Answers.pdf

Home assignment II on Spectroscopy 2024 Answers.pdf
A Survey of Techniques for Maximizing LLM Performance.pptx

A Survey of Techniques for Maximizing LLM Performance.pptx
June 3, 2024 Anti-Semitism Letter Sent to MIT President Kornbluth and MIT Cor...

June 3, 2024 Anti-Semitism Letter Sent to MIT President Kornbluth and MIT Cor...
Peer to peer
- 1. Peer to peer network And Client- server
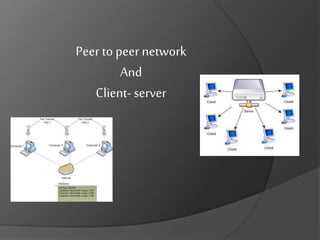
- 2. PEER TO PEER Peer to peer is an approach to computer networking where all computers share equivalent responsibility for processing data. Peer-to-peer networking (also known simply as peer networking) differs from client-server networking, where certain devices have responsibility for providing or "serving" data and other devices consume or otherwise act as "clients" of those servers
- 4. Characteristics of a Peer Network Peer to peer networking is common on small local area networks (LANs), particularly home networks. Both wired and wireless home networks can be configured as peer to peer environments
- 5. Benefits of a Peer to Peer Network You can configure computers in peer to peer workgroups to allow sharing of files, printers and other resources across all of the devices. Peer networks allow data to be shared easily in both directions, whether for downloads to your computer or uploads from your computer.
- 6. Advantages of peer to peer network 1) It is easy to install and so is the configuration of computers on this network, 2) All the resources and contents are shared by all the peers, unlike server-client where Server shares all the contents and resources. 3) P2P is more reliable as central dependency is eliminated. Failure of one peer doesn’t affect the functioning of other peers. In case of Client –Server network, if server goes down whole network gets affected. 4) There is no need for full-time System Administrator. Every user is the administrator of his machine. User can control their shared resources. 5) The over-all cost of building and maintaining this type of network is comparatively very less.
- 7. Disadvantages of peer to peer network Because each computer might be being accessed by others it can slow down the performance for the user Files and folders cannot be centrally backed up Security is not good and you can set passwords for files that you don’t want people to access but apart from that the security is pretty poor.
- 8. Client - server The term client-server refers to a popular model for computer networking that utilizes client and server devices each designed for specific purposes. The client-server model can be used on the Internet as well as local area networks (LANs). Examples of client- server systems on the Internet include Web browsers and Web servers, FTP clients and servers, and the DNS.
- 9. Characteristics of a client - server Sends requests to the server It expects and receives responses from the server.
- 10. Benefits Of Client Server All data are centralized on a single server, simplifying security checks and updates data and software. The technology supporting the client - server are more mature than others. A level administration server, customers have little importance in this model, they have less need to be administered
- 12. List of clients
- 13. Advantages of client- server A client server enables the roles and responsibilities of a computing system. This means that it can update all the computers connected to it. An example of this would be software updates or hardware updates. The security is a lot more advanced than a peer to peer network. You can have passwords to your won profile so that no one can access everything when they want. And the level off access range in different organizations Many mature client-server technologies are already available which were designed to ensure security, 'friendliness' of the user interface, and ease of use
- 14. Disadvantages of client- server When the server goes down or crashes. All the computers connected to it become unavailable to use More expensive than a peer to peer network. You have to pay for start up cost When you expand the server it starts to slow down due to the Bit rate per second.
