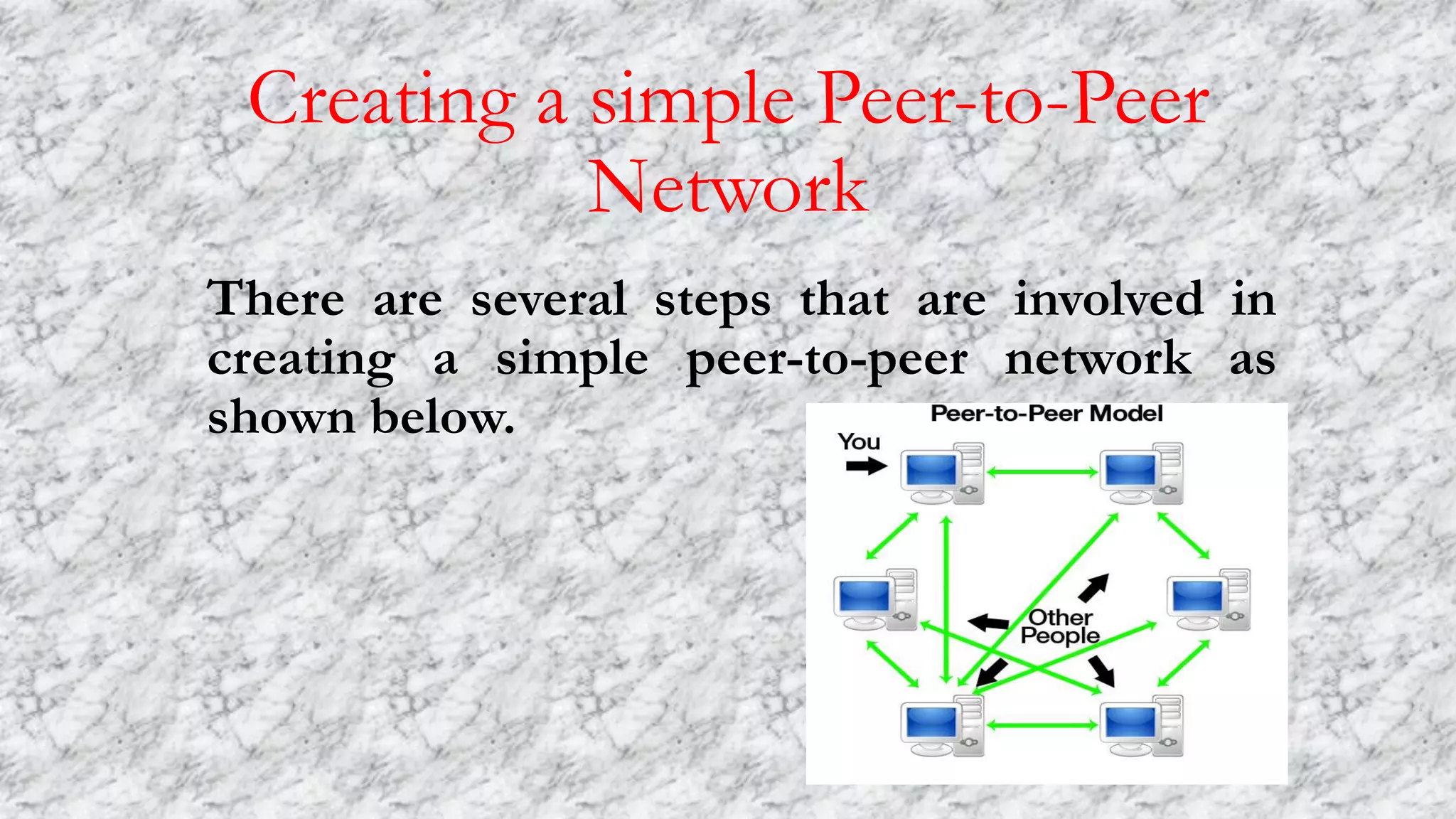
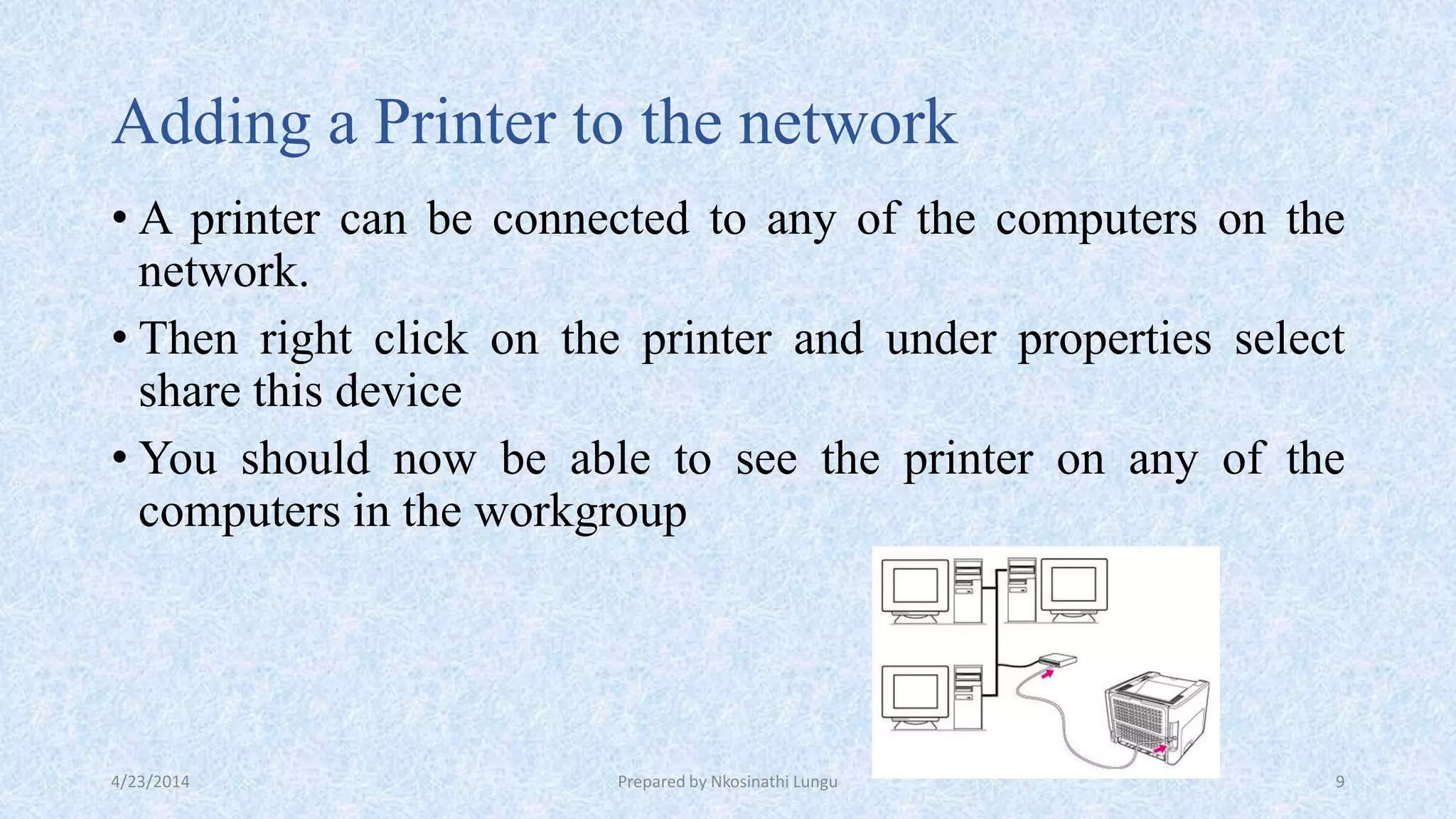
A peer-to-peer network connects computers of equal capacity without a central server, allowing the computers to share resources directly. Creating a simple peer-to-peer network involves installing network cards, connecting the computers to a switch with straight-through cables, assigning IP addresses, creating a workgroup to share files and resources, and adding a printer that can be accessed by any computer on the network. Peer-to-peer networks are well-suited for home or small business use due to their low cost and reliability through distributed data storage across multiple computers.