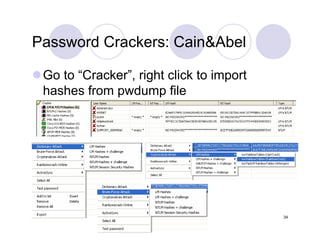
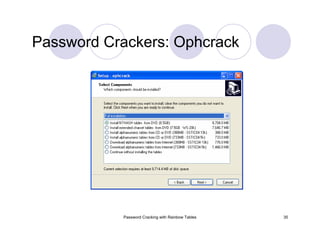
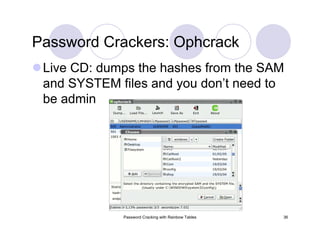
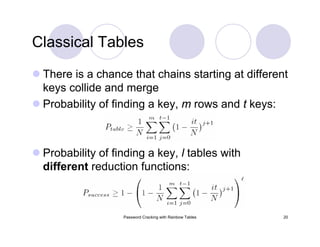
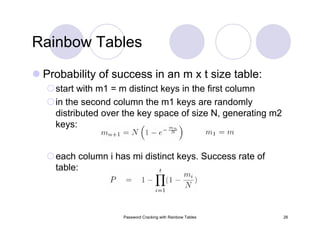
The document provides an overview of password cracking techniques, specifically focusing on rainbow tables and their advantages over classical methods. It discusses password storage, hashing algorithms, and the effectiveness of various attack strategies, stressing the importance of secure password practices. Additionally, it outlines the limitations of rainbow tables and offers suggestions for improving password security.




![Password Cracking with Rainbow Tables 9
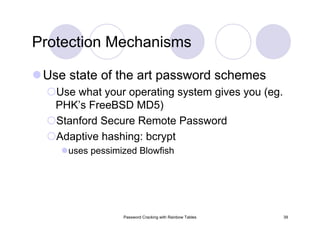
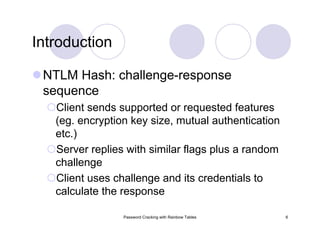
Secure Passwords
Password Strength
bit-strength
[a-z][A-Z][0-9] and symbols = 95 variations per
character = log(95) ~ 6.6b
8 character password x 6.6b = 53b
cracking 72b key using current equipment is
estimated to take about 1,453 years
no digital computer is capable of breaking 128b or
256b encryption
NIST recommends 80b for most secure passwords ~
12 character random password from 95 character
domain](https://image.slidesharecdn.com/passwordcracking-161230172553/85/Password-Cracking-with-Rainbow-Tables-9-320.jpg)


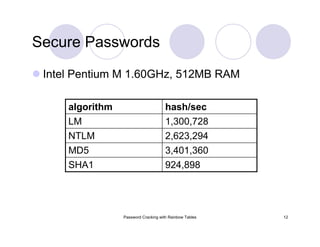
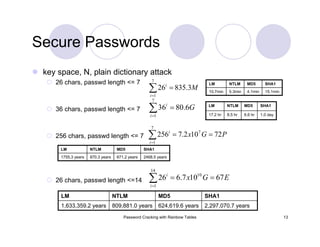





![Password Cracking with Rainbow Tables 29
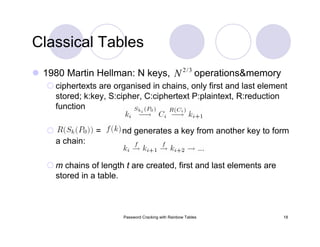
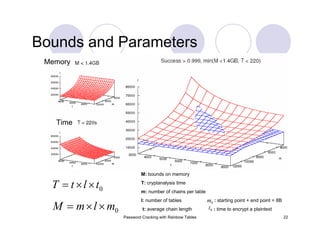
Rainbow Tables: Parameter Optimization
0.9990success probability
610 MBtable size
8353082582keyspace
[ABCDEFGHIJKLMNOPQRSTUVWXYZ]charset
0.9904success probability
3 GBtable size
80603140212keyspace
[ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789]charset
0.99909success probability
24 GBtable size
915358891407 (2^39.7)keyspace
[ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+= ]charset
0.999success probability
64 GBtable size
7555858447479 (2^42.8)keyspace
[ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|:;"'<>,.?/ ]charset
Last table would take 41.3 years to generate on my laptop.](https://image.slidesharecdn.com/passwordcracking-161230172553/85/Password-Cracking-with-Rainbow-Tables-29-320.jpg)
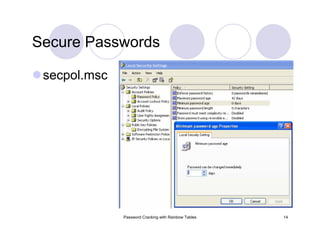
![Password Cracking with Rainbow Tables 30
Rainbow Tables: Parameter Optimization
2100
len_chain
0:4
table index
8000000,
40000000
71alpha[numeric]lm
num_chainslen_maxlen_mincharsethash](https://image.slidesharecdn.com/passwordcracking-161230172553/85/Password-Cracking-with-Rainbow-Tables-30-320.jpg)