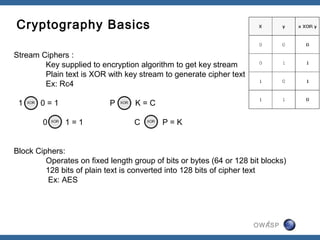
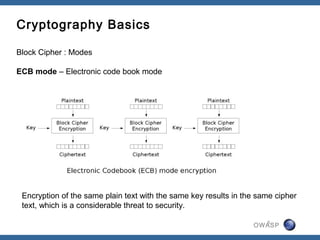
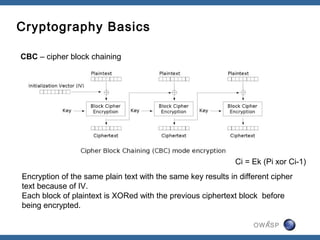
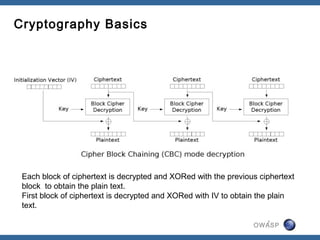
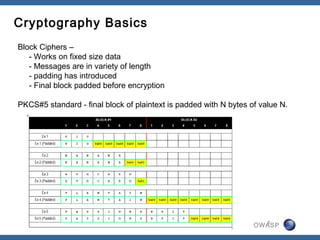
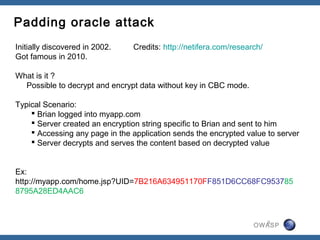
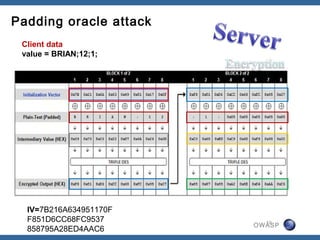
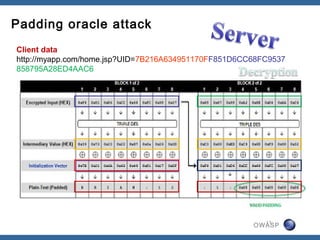
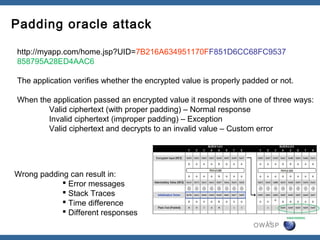
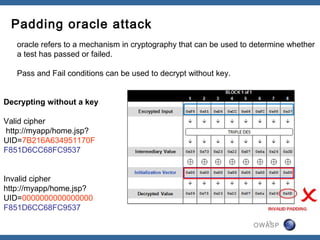
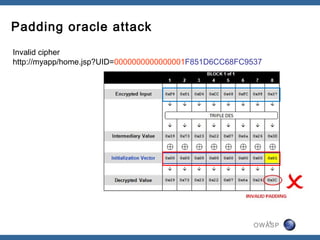
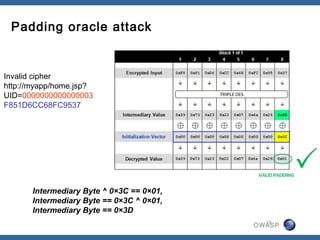
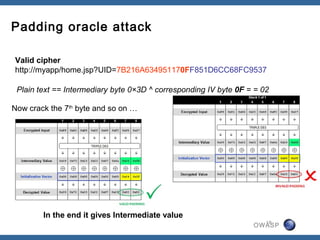
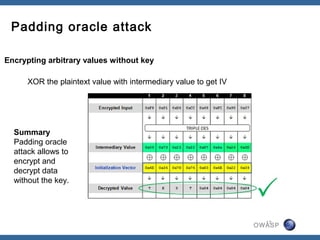
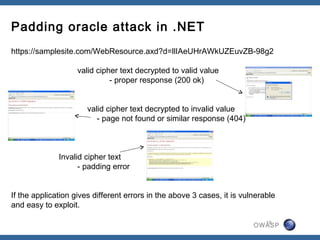
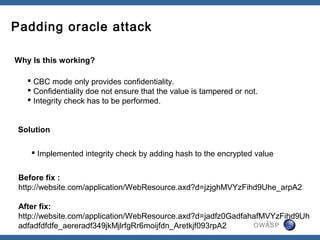
The document discusses padding oracle attacks, which allow decrypting and encrypting data without the encryption key. Padding oracle attacks exploit vulnerabilities in cryptosystems that use padding and are vulnerable if the application provides different error responses for valid and invalid ciphertexts. The attack works by making queries to the "oracle" to determine if padding is valid or not and using this information to gradually decrypt ciphertext blocks to obtain the plaintext. The document provides examples of padding oracle attacks on .NET applications and recommends implementing integrity checks to prevent such attacks.