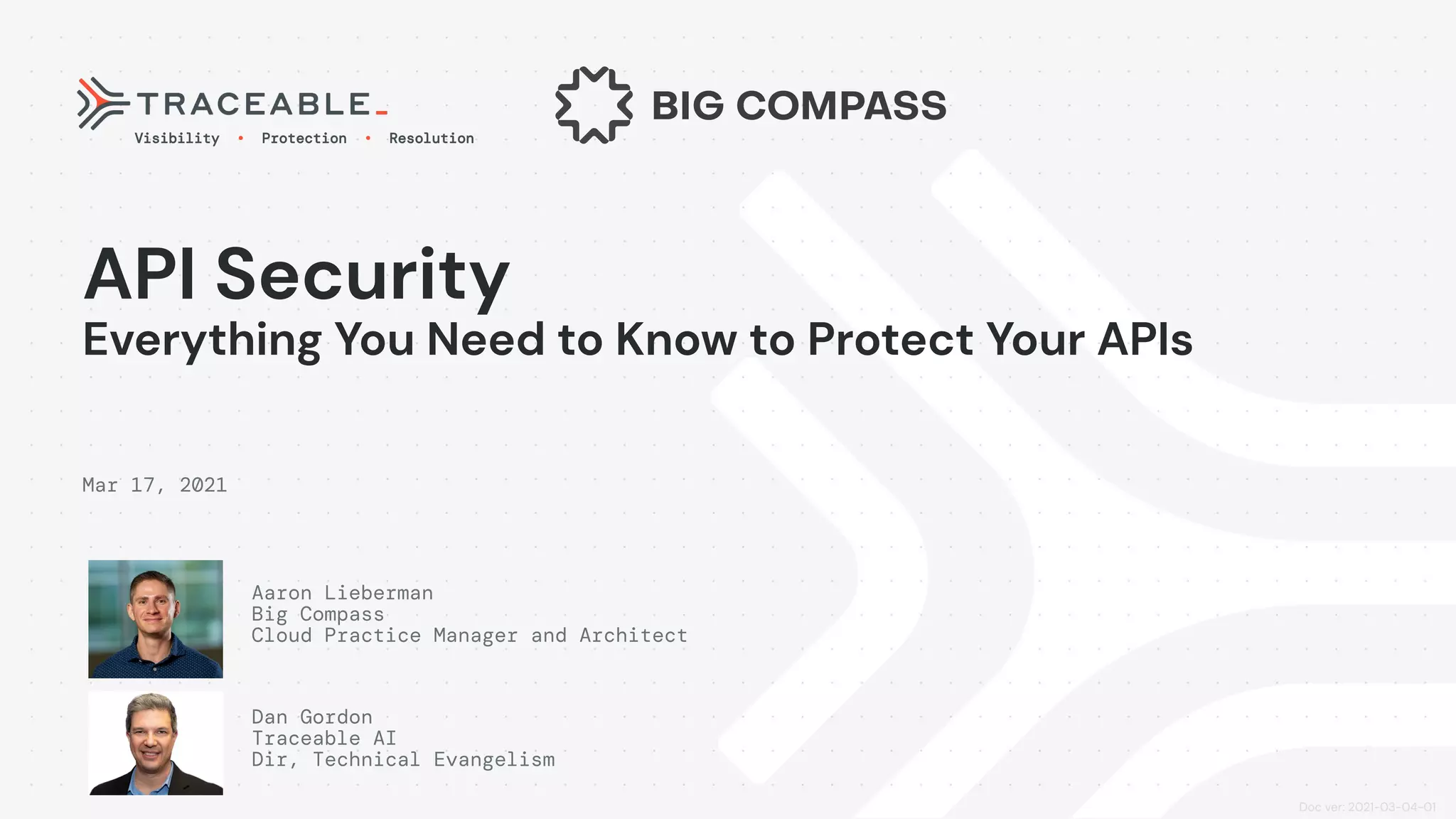
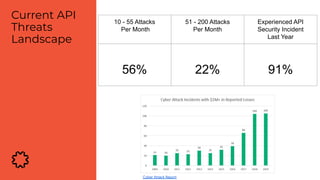
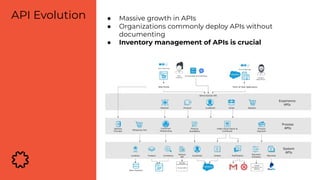
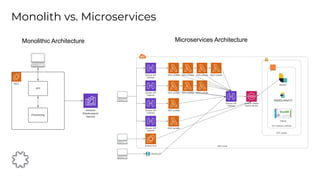
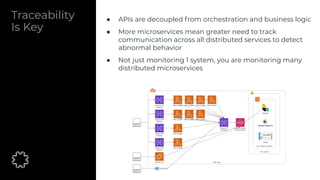
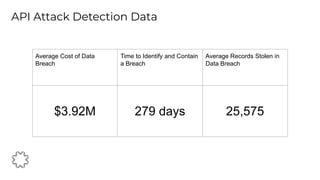
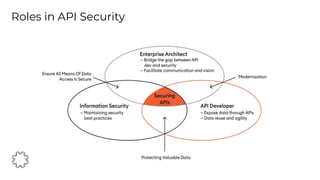
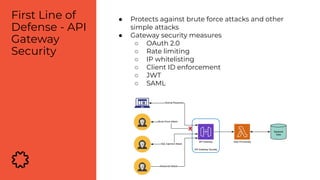
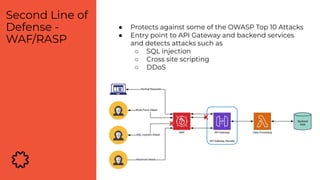
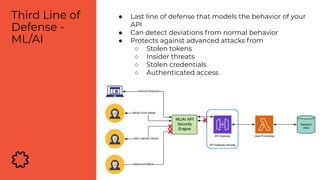
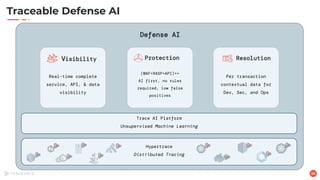
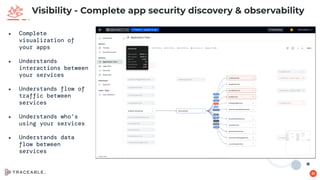
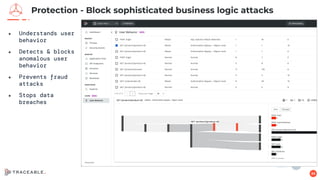
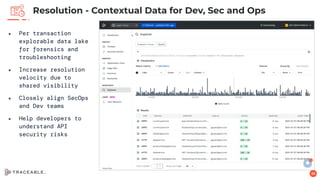
The document discusses the critical aspects of API security, covering topics such as the growing API landscape, the challenges in protecting APIs, and the importance of visibility and inventory management. It highlights advanced attacks on APIs and proposes a layered security approach involving various defenses like API gateways, WAF/RASP, and AI-based solutions for enhanced protection and anomaly detection. The agenda also references a practical guide on API security and emphasizes the importance of collaborative roles in safeguarding APIs.