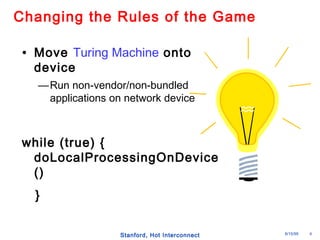
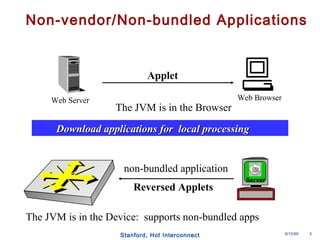
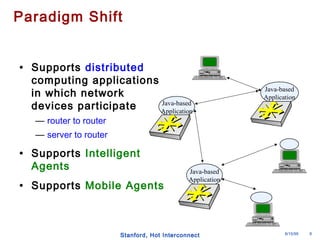
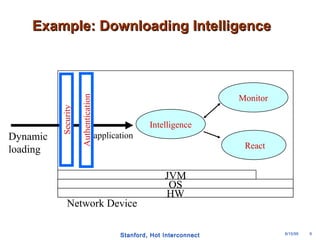
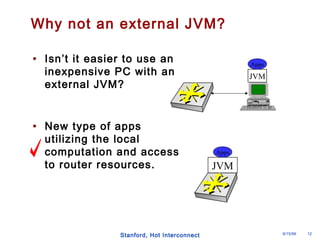
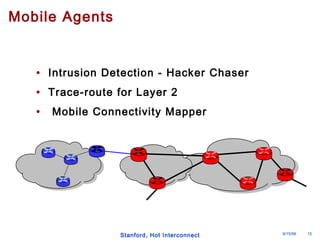
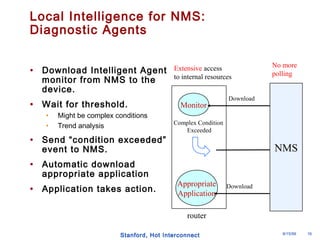
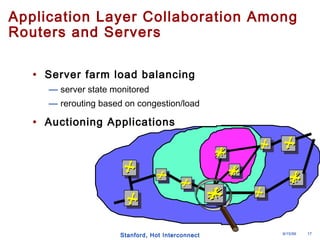
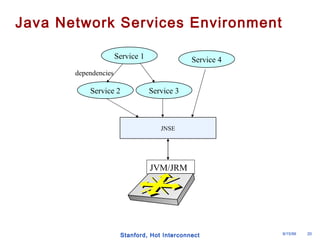
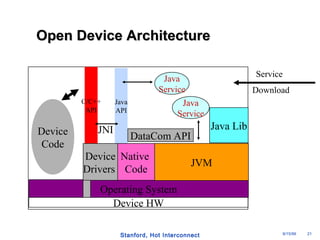
The document discusses an open programmable architecture for Java-enabled network devices, highlighting its ability to support non-vendor applications and allow local computation on devices. It emphasizes the paradigm shift towards dynamic agents and secure, intelligent applications that can react autonomously to network conditions. The architecture promises to enhance collaboration among network devices while ensuring a stable and secure environment for executing Java applications.