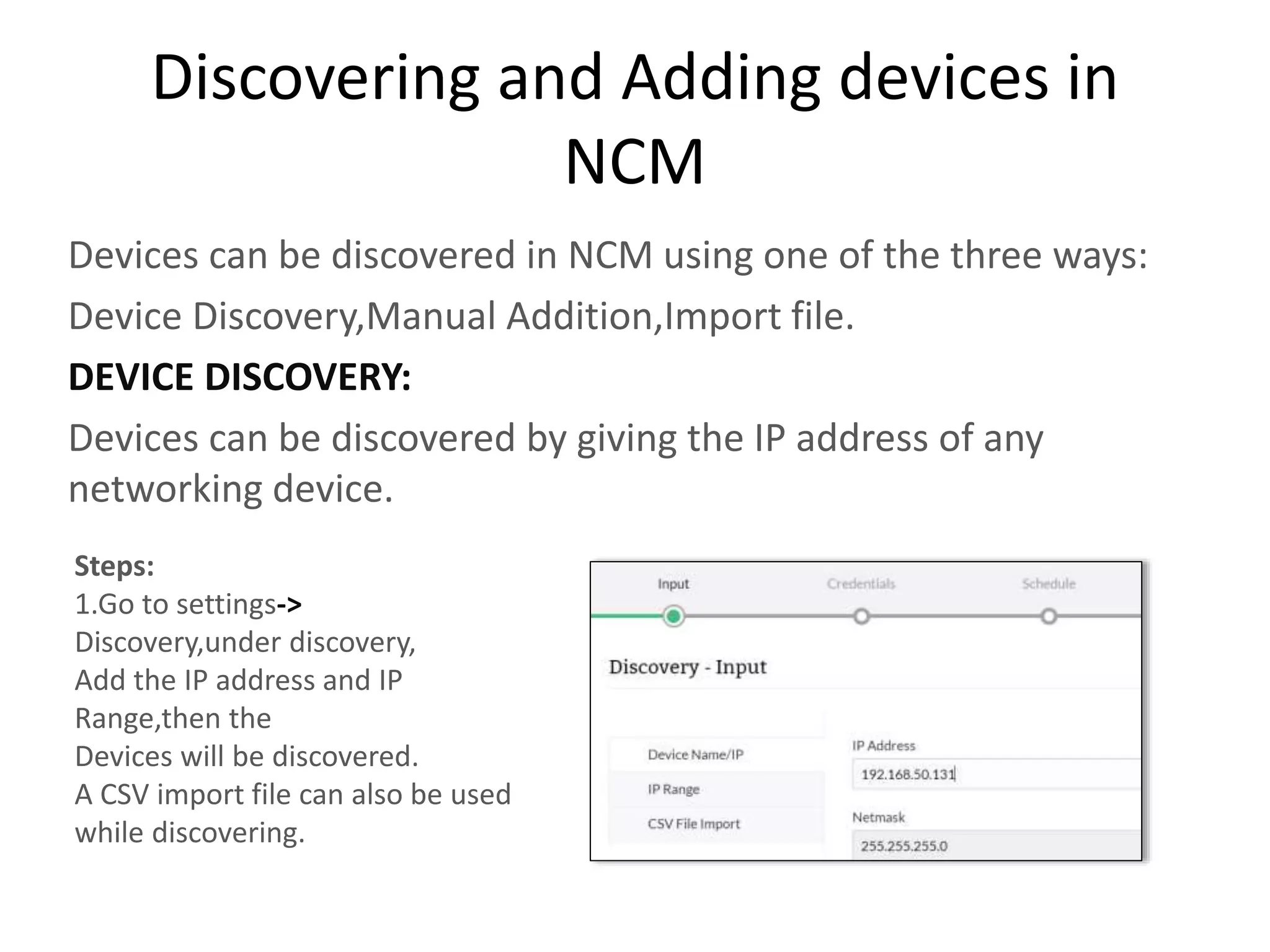
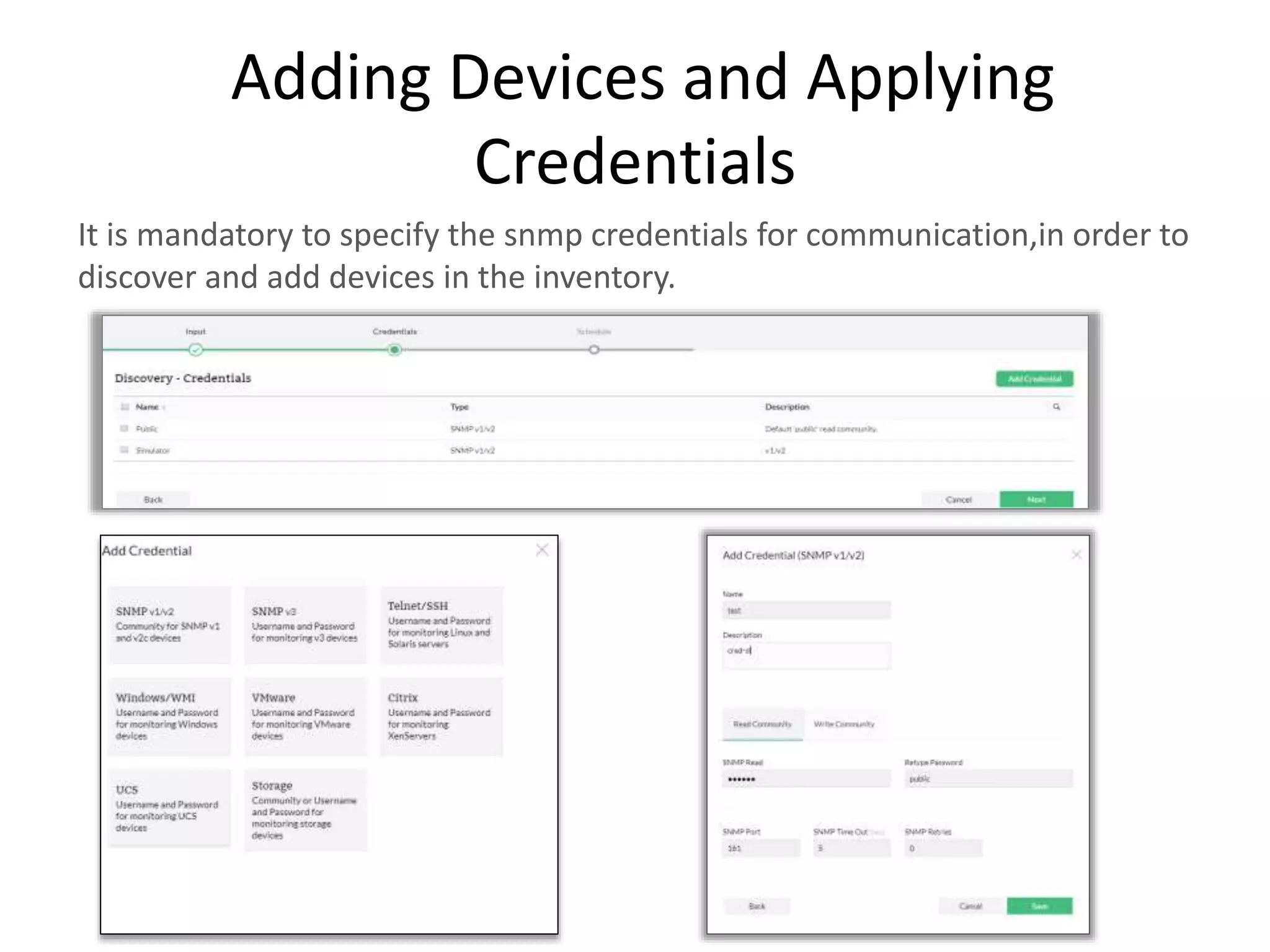
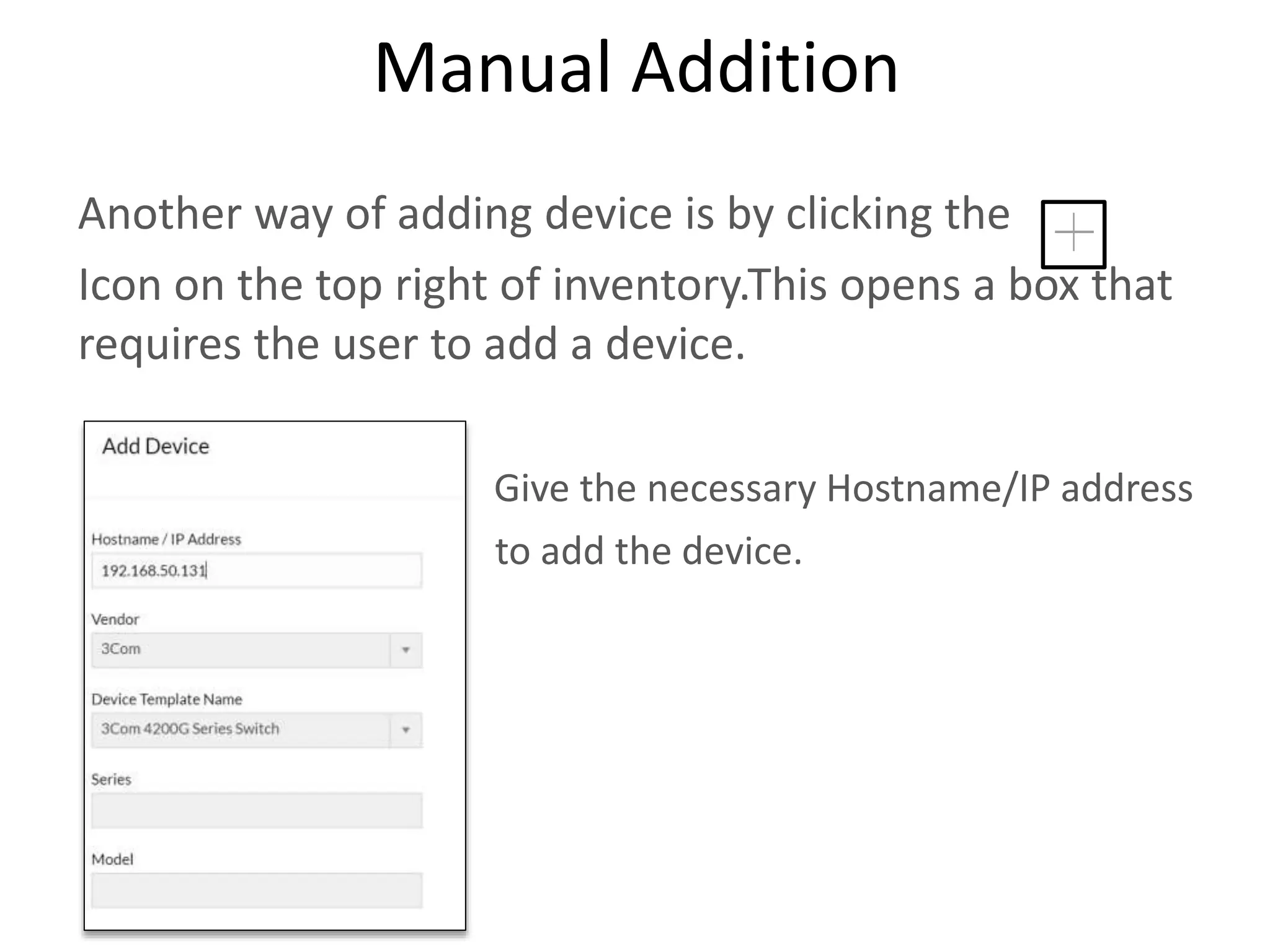
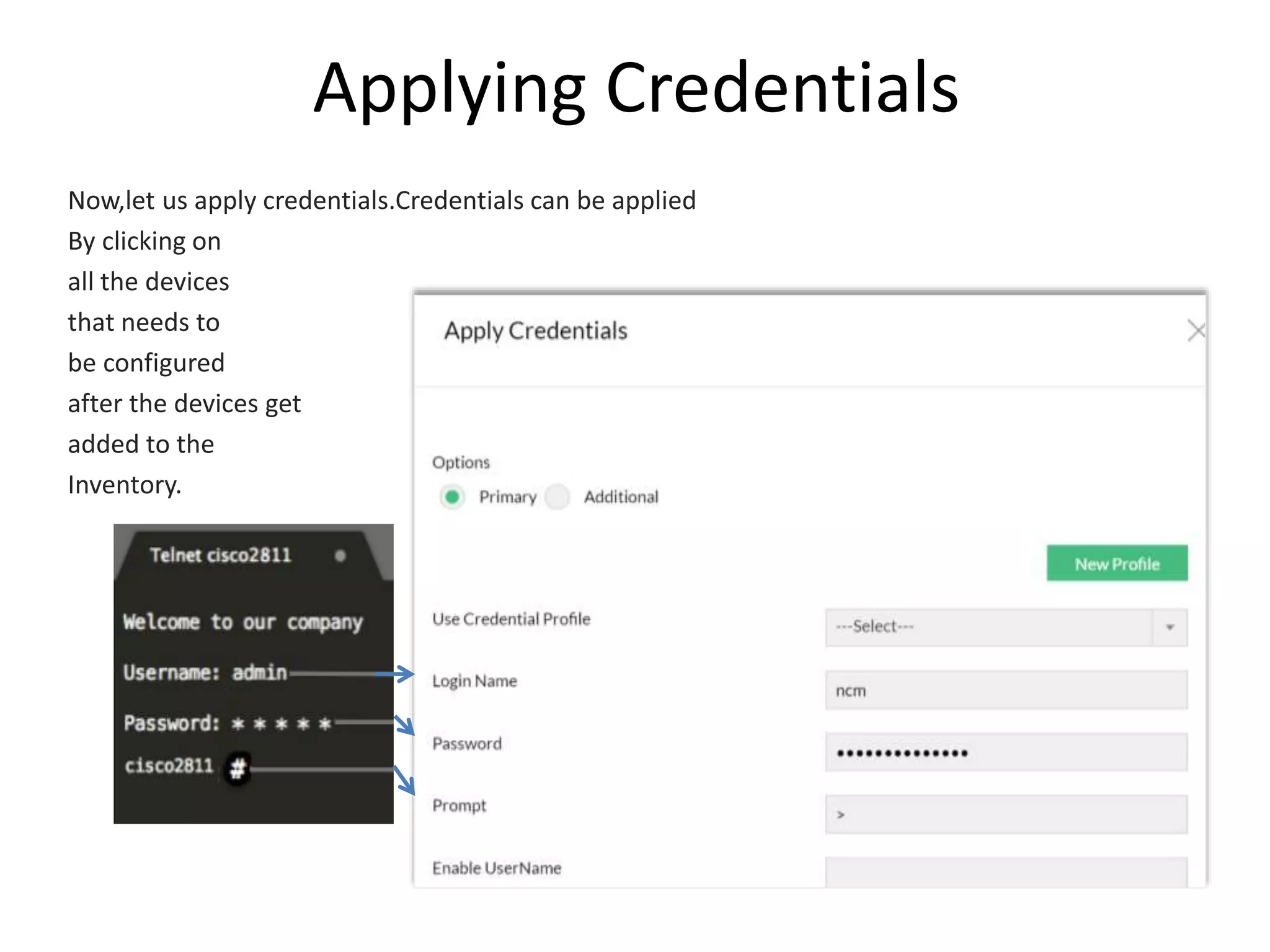
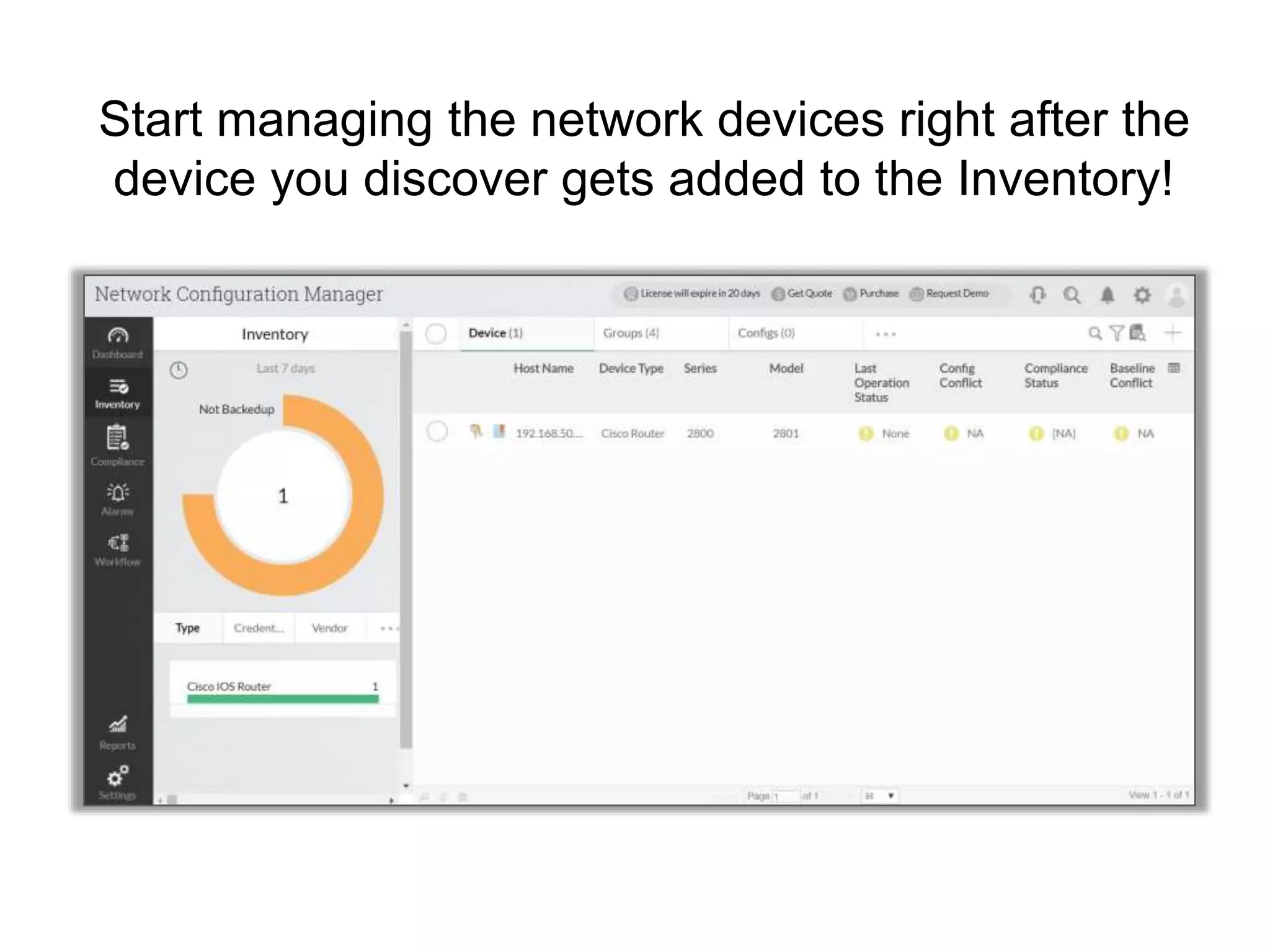
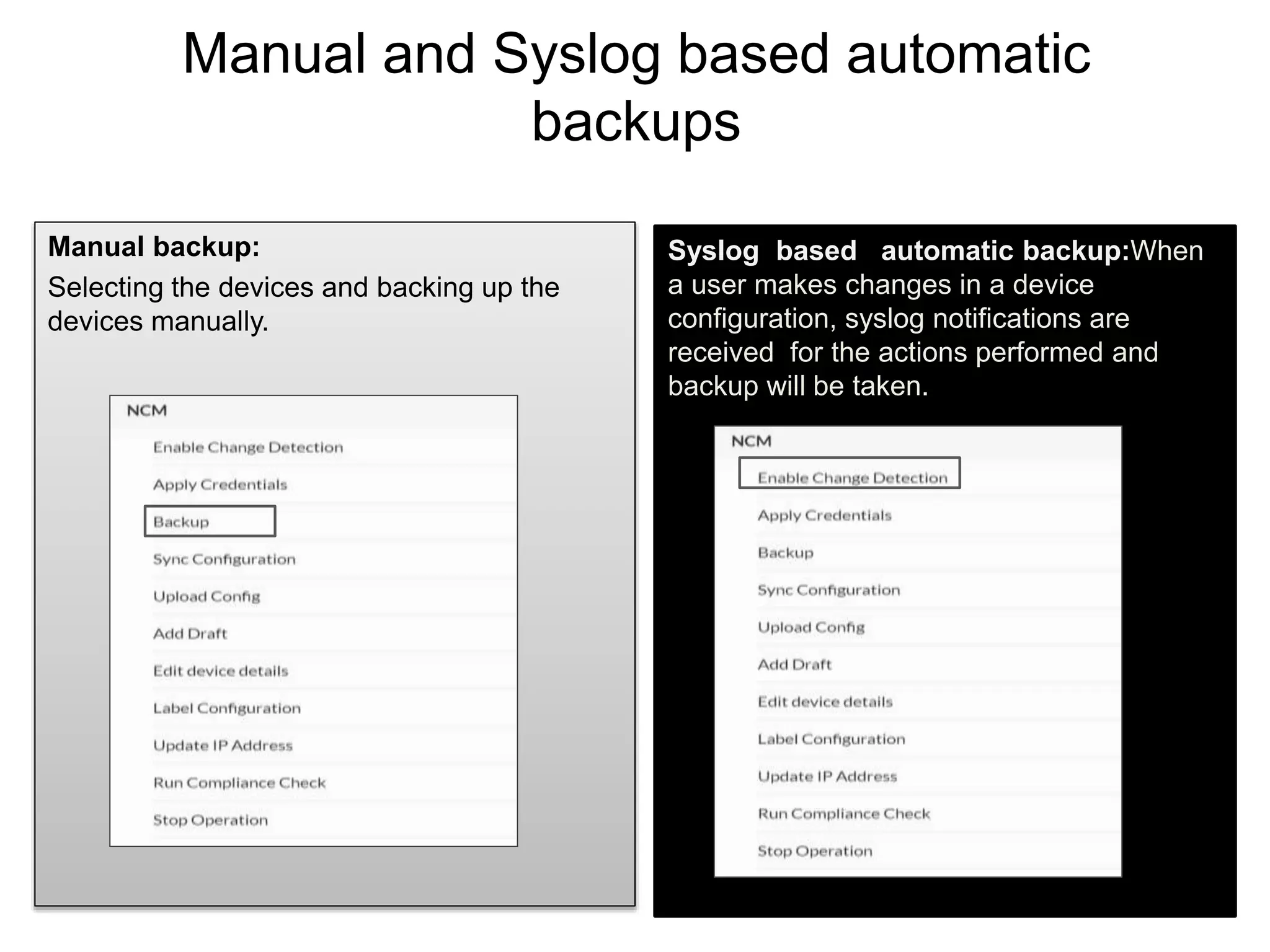
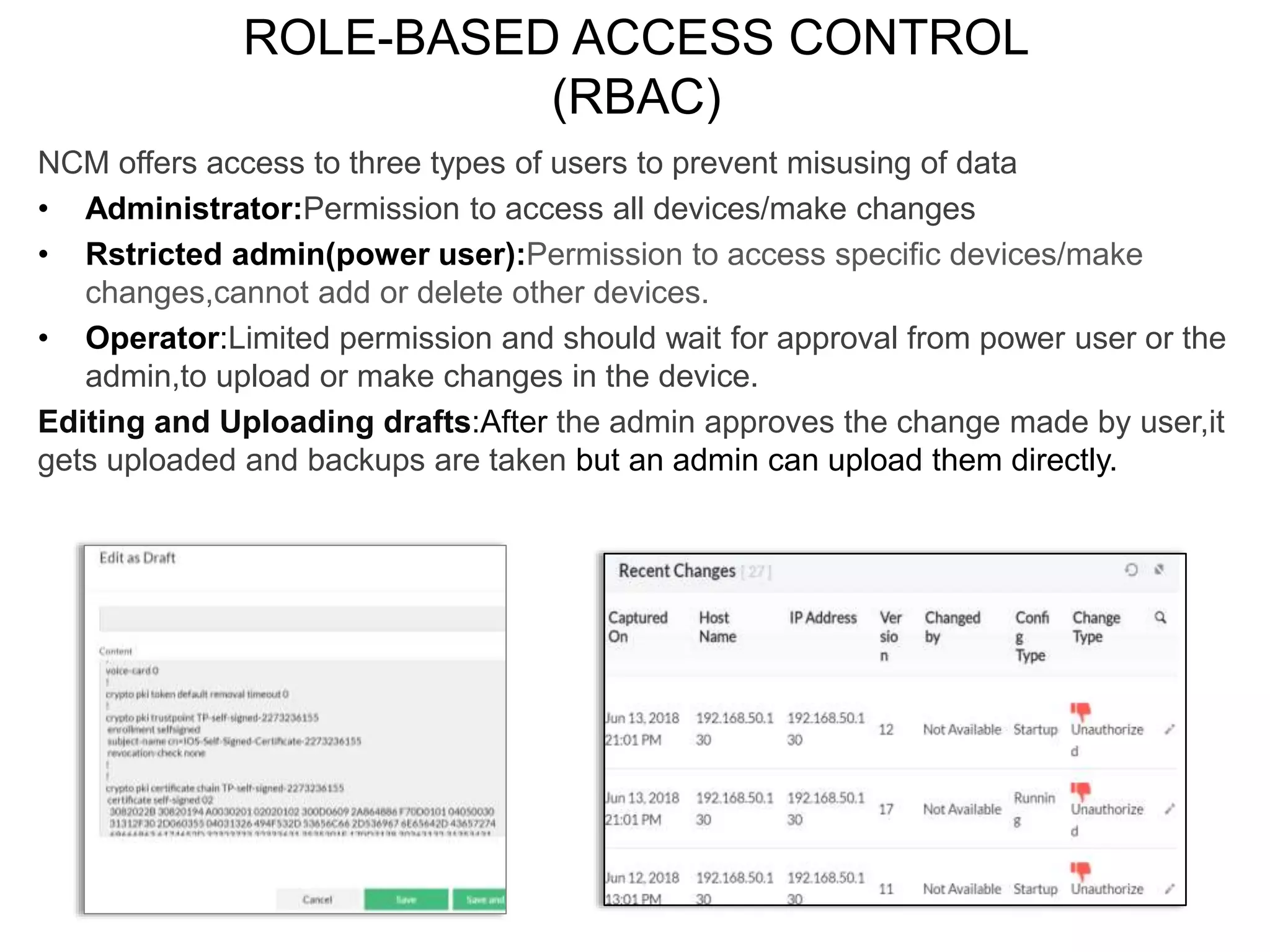
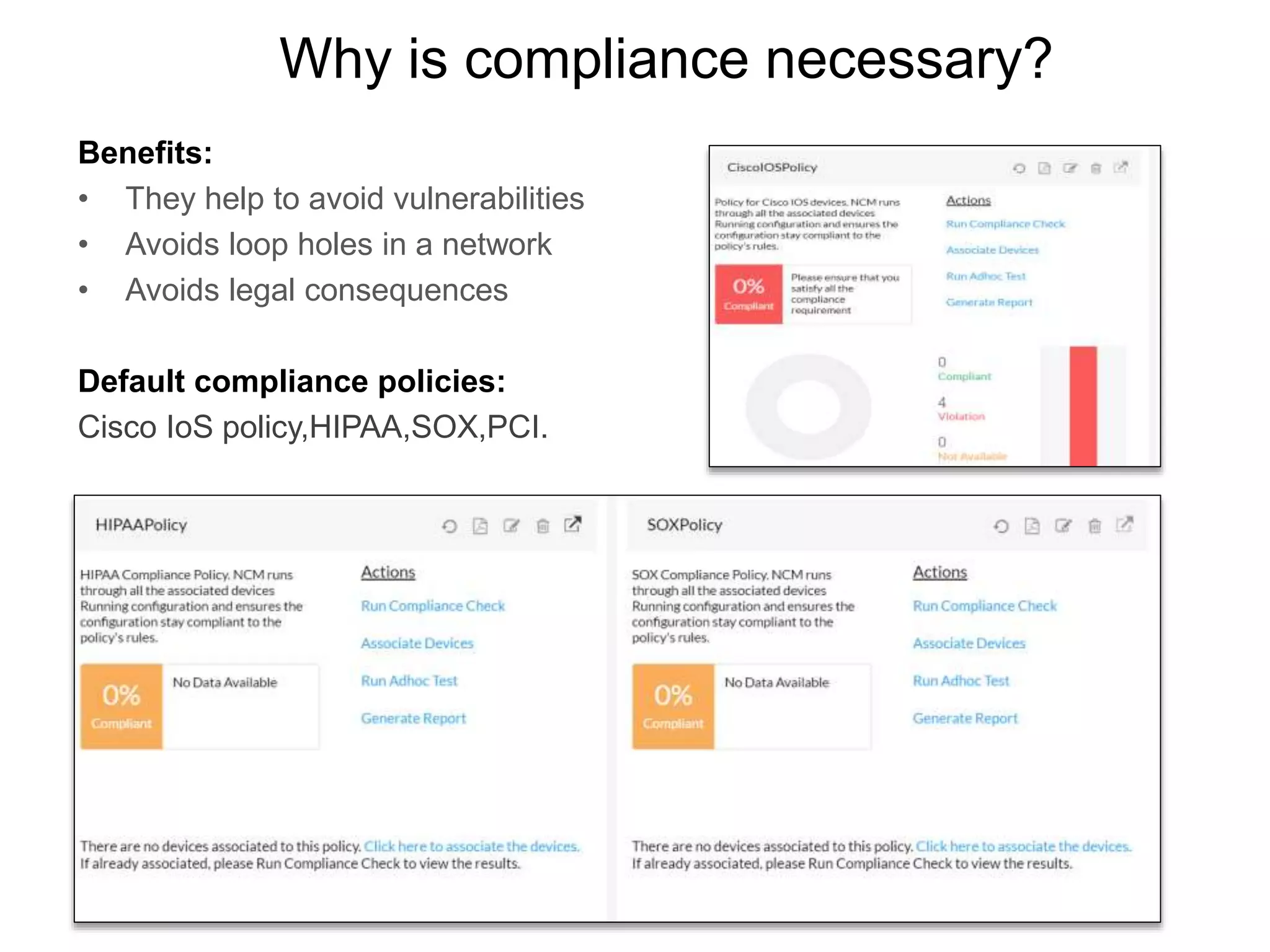
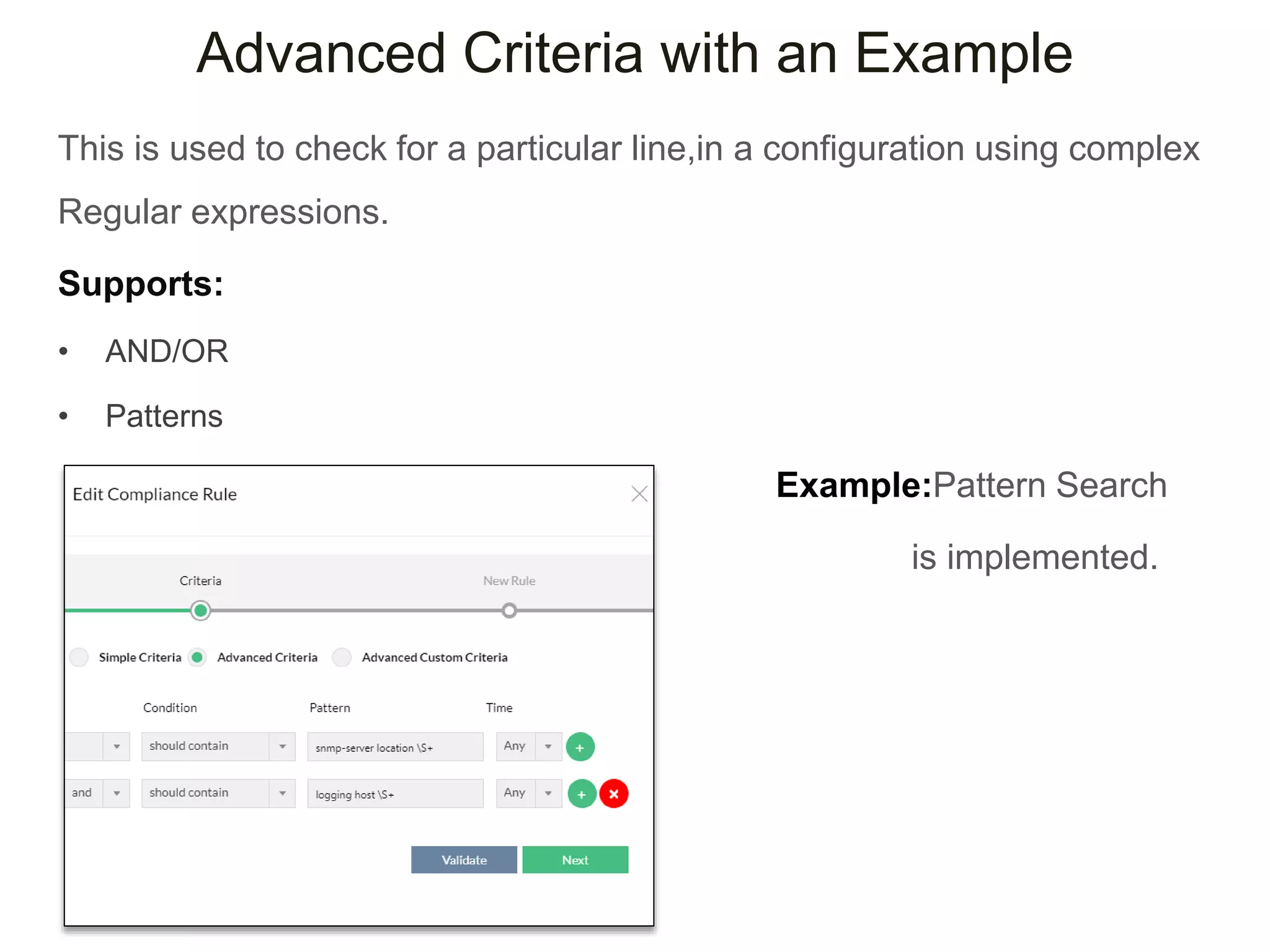
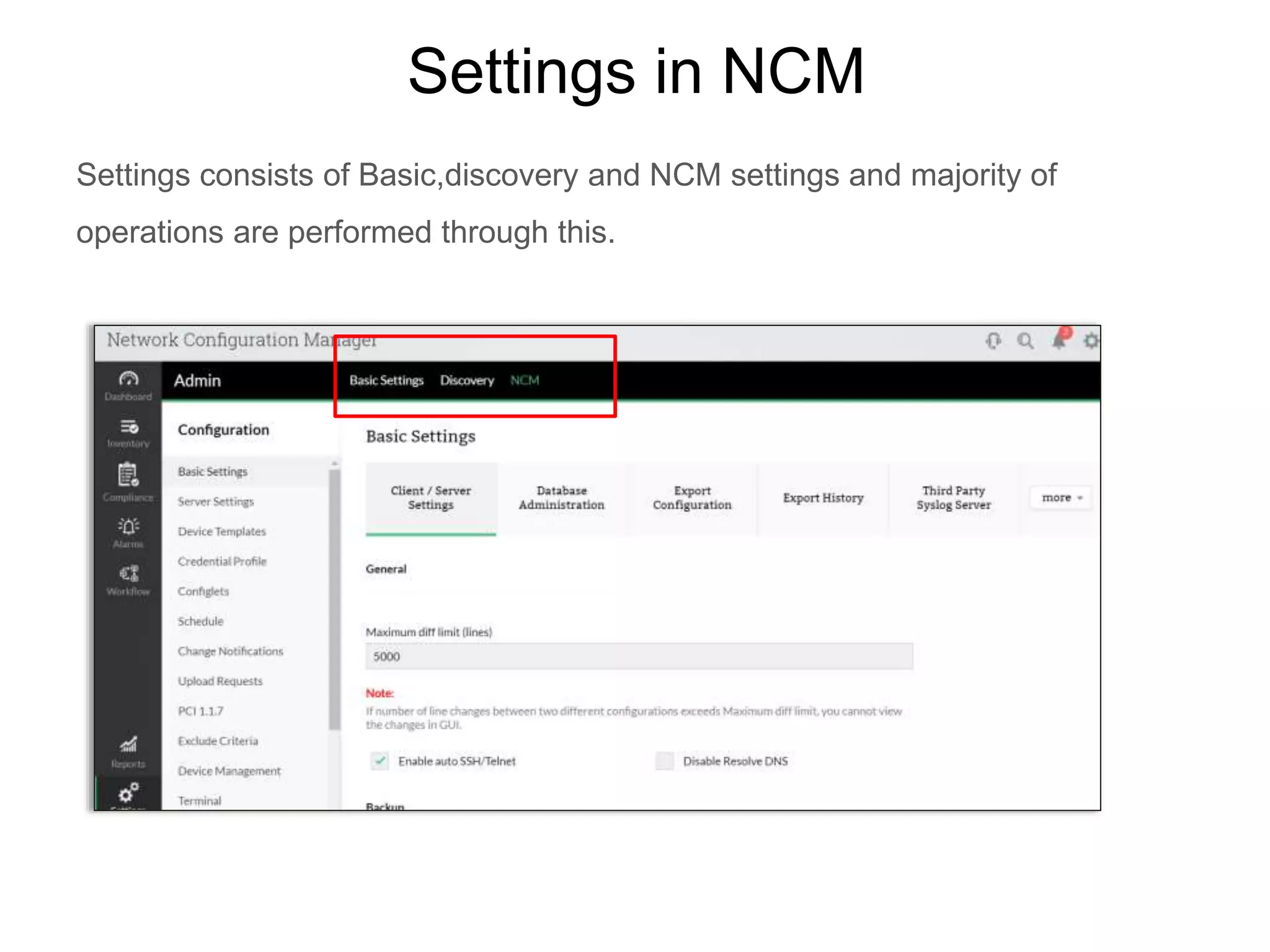
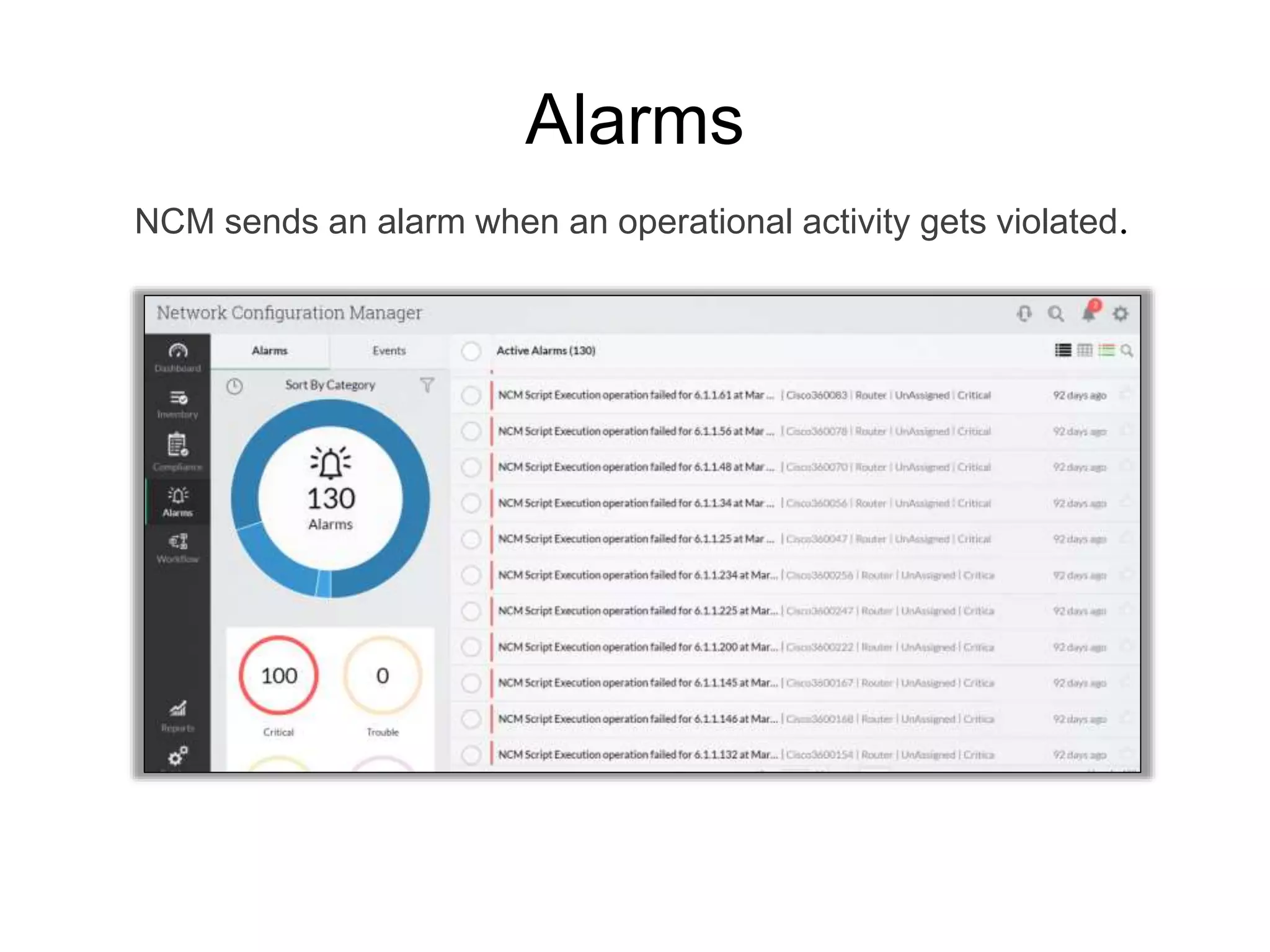
NCM is a network configuration management tool that allows users to discover devices, backup configurations, detect configuration changes, compare configurations, manage compliance policies, and generate detailed reports. It offers benefits such as being user friendly, easy to install and use, affordable pricing, and 24/7 technical support. NCM provides a complete solution for network configuration management.