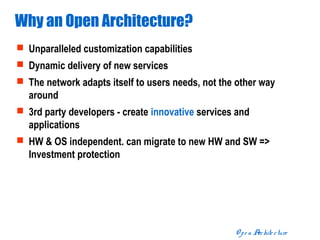
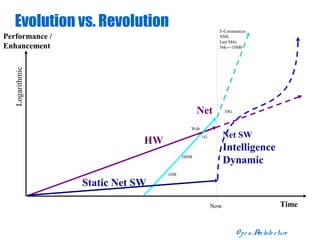
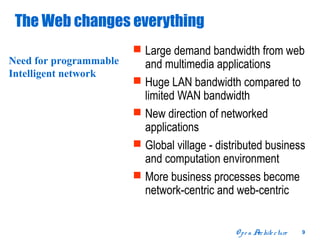
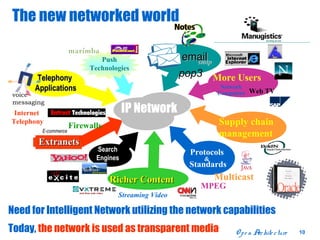
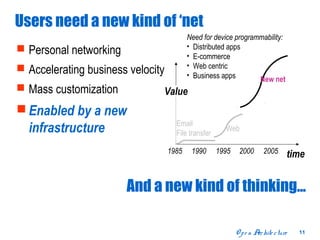
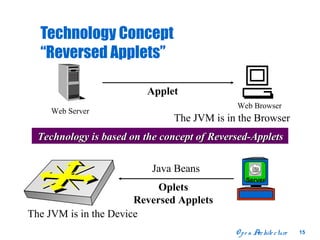
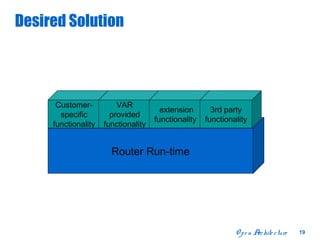
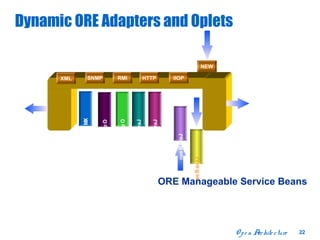
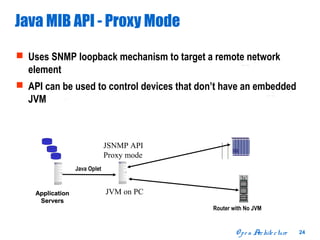
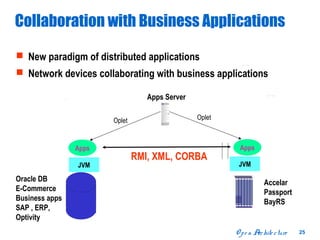
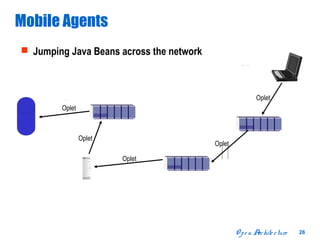
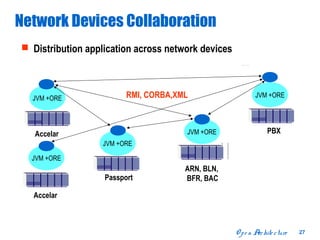
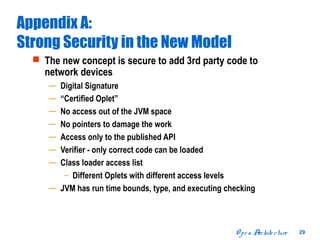
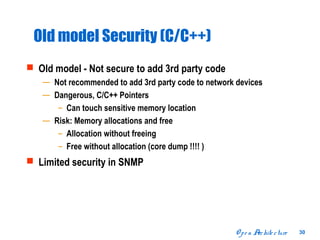
The document discusses open distributed networking intelligence using a new Java paradigm. It proposes transferring intelligence to network devices by making them programmable using Java, allowing third-party developers to create innovative services and applications. This would enable new intelligent distributed applications through collaboration between network devices and business applications using technologies like RMI, XML, and CORBA.