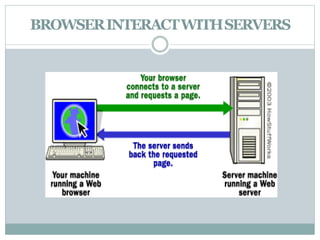
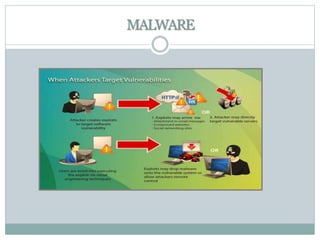
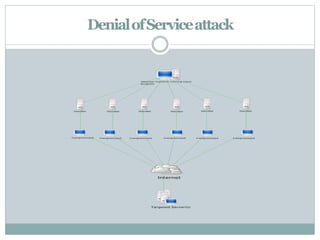
The document discusses web server security issues, defining web servers and their types, including Apache and IIS. It outlines various security threats such as brute force attacks, botnets, malware, SQL injection, and denial-of-service attacks, emphasizing the importance of keeping software updated and maintaining strong security practices. Careless user behavior is highlighted as a significant risk factor for server security.