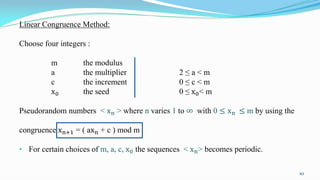
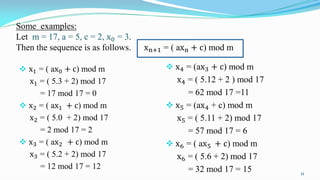
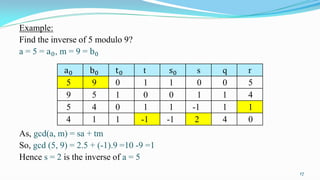
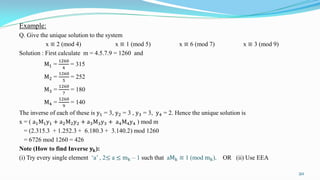
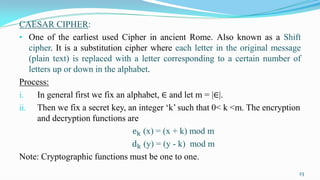
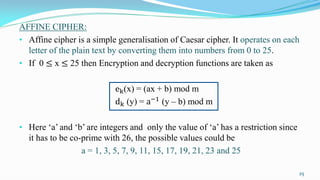
This document presents an overview of number theory, covering its definitions, applications, and relevant concepts such as modular arithmetic, congruences, and cryptography. It also discusses various algorithms including Euclid's algorithm and the extended Euclidean algorithm, alongside examples to illustrate these principles. The document emphasizes the applications of number theory in fields like cryptography and coding theory, providing insights into mathematical processes like the Chinese Remainder Theorem and different ciphers.










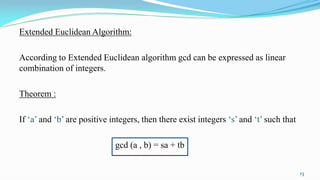
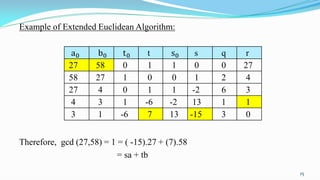
![Algorithm:
Input : Two positive integers a, b
Output: r = gcd ( a, b) and s, t such that
sa + tb = gcd (a,b)
1. a0 = a, b0 = b
2. t0 = 0, t = 1
3. s0 = 1, s = 0
4. q = [a0 / b0]
5. r = a0 - qb0
6. WHILE r > 0 DO
7. temp = t0 – qt
8. t0 = t, t = temp
9. temp = s0 – qs
10. s0 = s, s = temp
11. a0 = b0, b0 = r
12. q = [a0 / b0], r = a0 - qb0
13. IF r > 0 THEN
14. gcd = r
15. END
16. END
17. Output gcd, s, t 14](https://image.slidesharecdn.com/astudyonnumbertheoryanditsapplications-180315185721/85/A-study-on-number-theory-and-its-applications-14-320.jpg)












![REFERENCES
[1] Introduction to number theory and its application by Lucia Moura
[2] Number theory applications by Christopher M. Bourke Instructor: Berthe Y. Choueiry
2007
[3] Number theory and computer applications by Ramanujachary Kumanduri
[4] Neal Koblitz. A Course in Number Theory and Cryptography. New York: Springer-
Verlag, 1994
[5] Applications of number theory in cryptography, Zihao Jiang
32](https://image.slidesharecdn.com/astudyonnumbertheoryanditsapplications-180315185721/85/A-study-on-number-theory-and-its-applications-32-320.jpg)
