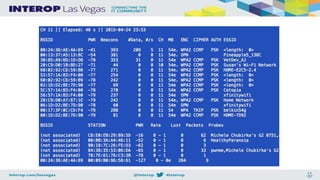
The document provides insights into wireless security and the use of open source tools for network penetration testing and security analysis. Michele Chubirka outlines the necessary hardware, software, and recommended tools while emphasizing the importance of learning and hands-on experience. It also highlights common wireless attacks and methods of protection against them, along with legal cautions regarding wireless signal interference.