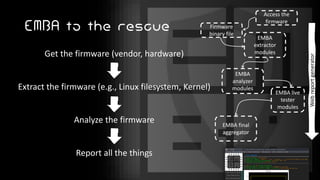
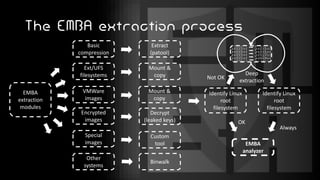
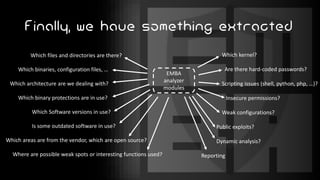
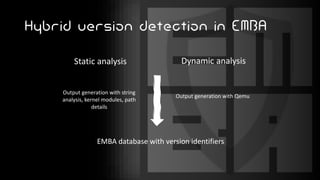
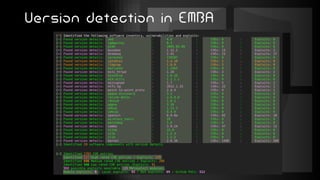
This document introduces EMBA, a free and open-source firmware analysis tool. It describes EMBA's extraction and analysis modules that can extract firmware components like Linux filesystems, decrypt images, and analyze the firmware using tools like binwalk and Yara rules. EMBA aims to automate common firmware analysis tasks and identify security issues like outdated components, weak configurations, and potential 0-day vulnerabilities through static and dynamic analysis techniques.