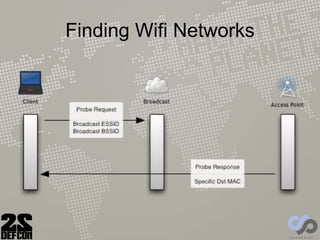
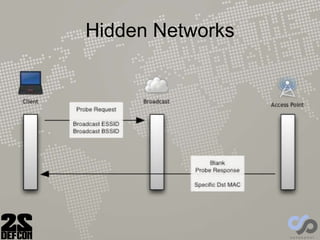
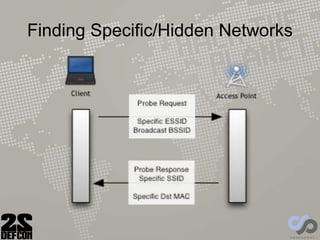
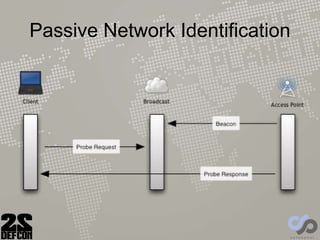
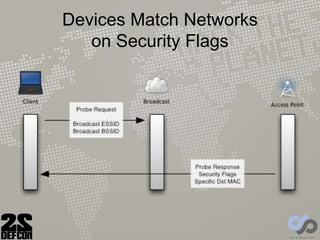
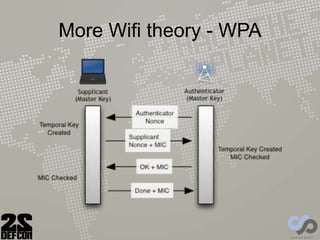
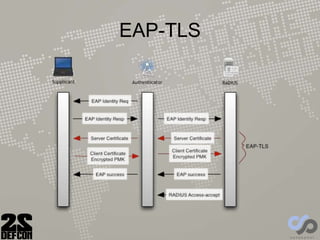
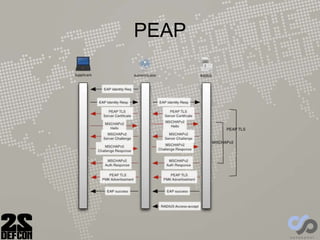
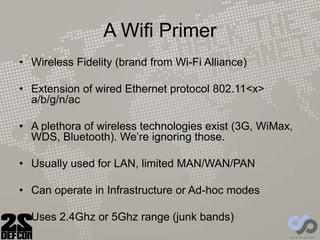
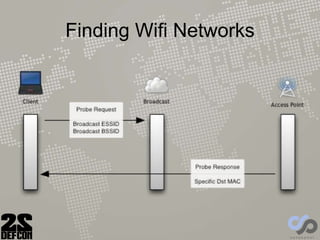
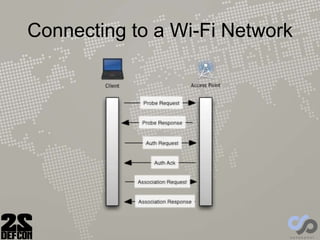
The document discusses advancements in rogue access point attacks presented by Ian de Villiers and Dominic White at DEFCON 22, focusing on vulnerabilities in Wi-Fi security protocols. Key topics include improvements in Karma attacks, the introduction of the Mana toolkit for man-in-the-middle attacks, and strategies for exploiting various devices' weaknesses in connecting to insecure networks. The presentation aims to provide actionable insights on enhancing the effectiveness of these attacks while addressing the challenges posed by evolving security measures.









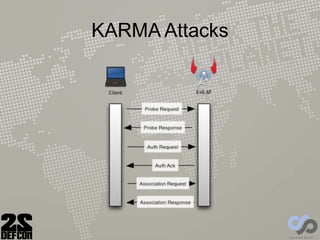
![KARMA Attacks
• Device will probe for remembered nets (preferred
network list [PNL]), even when not near them
• We just respond as the normal network would
– Hey “home network” you there?
– Uh, sure, I’m “home network”
• First presented in 2004 by Dino dai Zovi & Shane
Macaulay
• Modern implementations:
– airbase-ng by Thomas d'Otreppe
• Software only, no master mode needed
– hostapd-1.0-karma by Robin Wood (digininja)
• Used on the Hak5 pineapple](https://image.slidesharecdn.com/dc22-mana-supporting-150223014609-conversion-gate02/85/Improvement-in-Rogue-Access-Points-SensePost-Defcon-22-15-320.jpg)