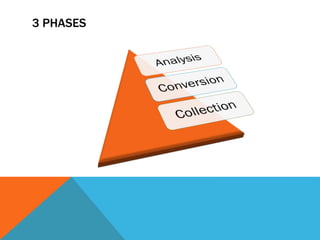
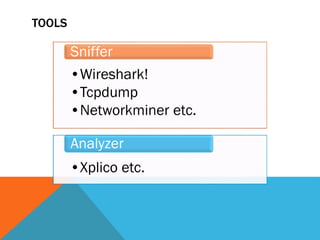
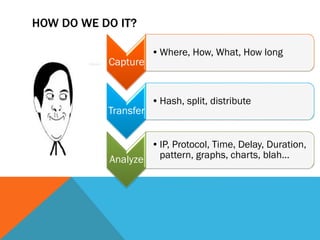
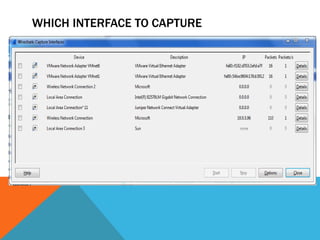
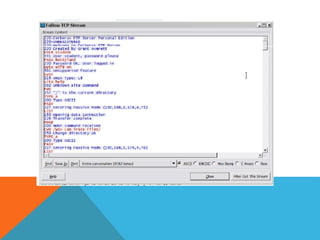
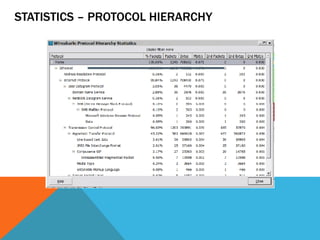
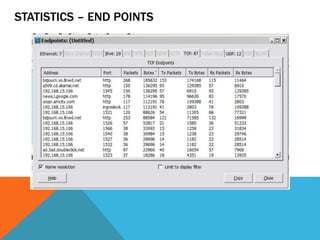
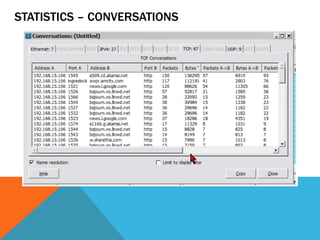
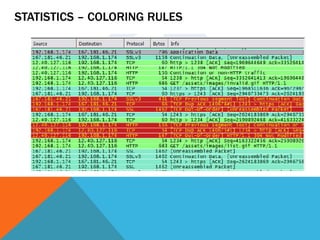
The document discusses the complexities of network forensics, emphasizing the need for tools like Wireshark, tcpdump, and networkminer for in-depth packet analysis. It highlights the importance of understanding network dynamics, suspicious communications, and effective capture and analysis techniques while advocating for a methodical approach to problem-solving. Key pre-requisites include patience, organization, and an inquisitive mindset to effectively gather and analyze network data.