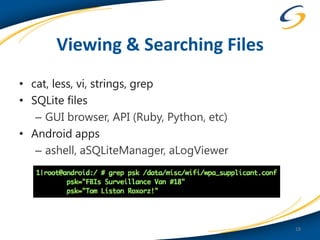
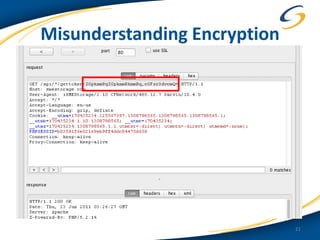
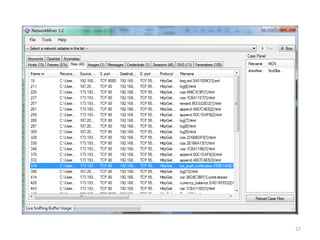
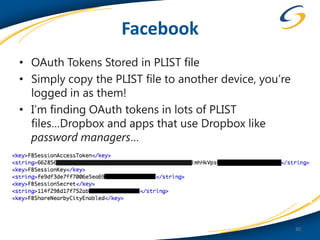
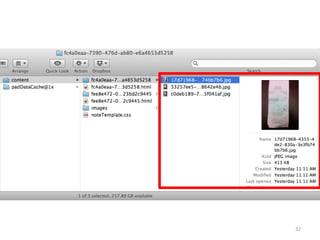
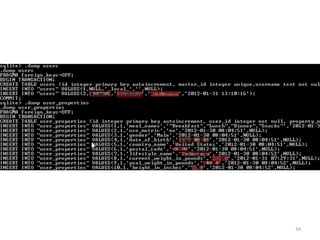
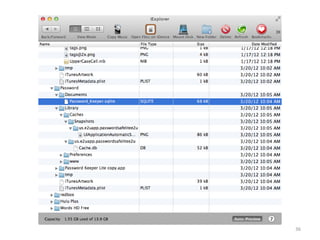
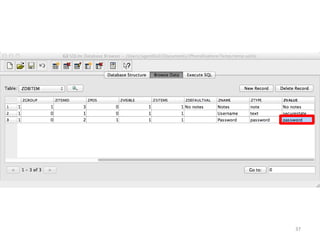
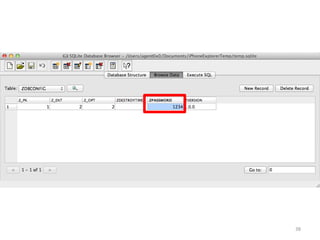
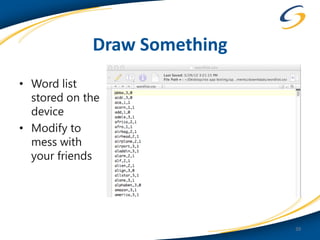
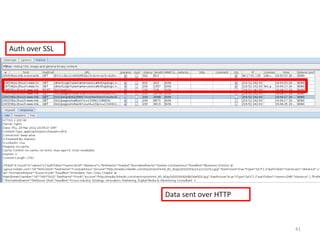
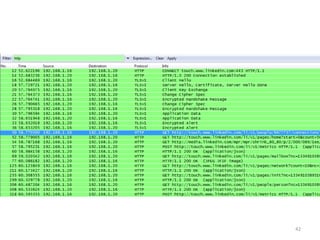
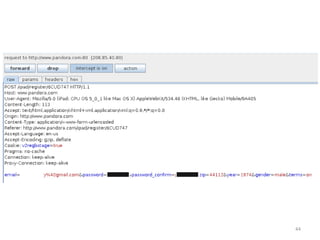
This document discusses common vulnerabilities found in mobile applications. It begins by outlining the types of sensitive data stored on mobile devices and used by mobile apps. It then covers tools for analyzing the file system, application layer, and transport layer of mobile apps. Specific vulnerabilities are highlighted from the OWASP Mobile Top 10 list, including insecure data storage, weak server-side controls, and insufficient transport layer protection. Examples of vulnerabilities found in popular apps like Facebook, Evernote, MyFitnessPal, and LinkedIn are provided. The document concludes by emphasizing that mobile security issues go beyond just application vulnerabilities.