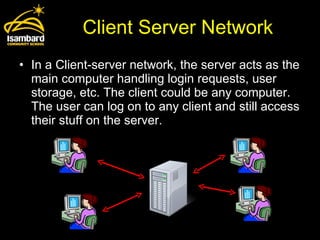
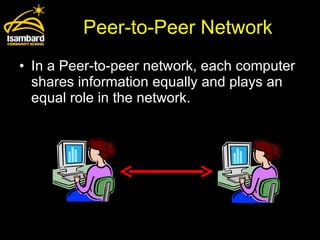
Network policies and security measures are needed to properly manage networks and protect systems and data. Client-server networks have servers that handle data storage and login requests while clients access this data. Peer-to-peer networks have equal sharing between computers. Disaster recovery plans are important in case systems fail, and backups ensure data can be restored if storage devices fail. Network managers must implement passwords, encryption, and user restrictions to secure systems, but new technologies have made networks harder to lock down as hackers can more easily exploit vulnerabilities.