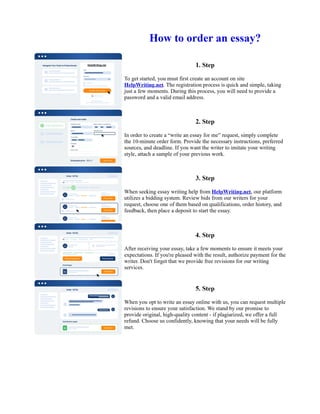
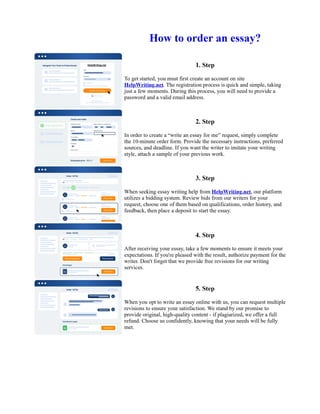
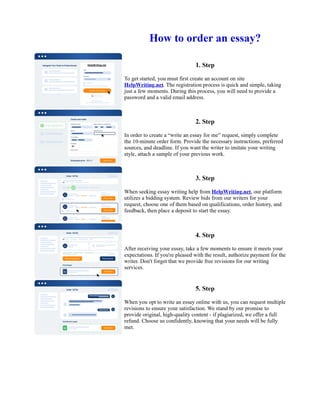
The document discusses the Flask operating system architecture prototype created by the NSA and University of Utah researchers to address the need for flexibility in controlling access rights policies. The Flask prototype was found to be practical and flexible to operate, with the ability to cleanly separate security policy logic from enforcement mechanisms. It was shown to meet the needs of a system requiring policy flexibility through a security policy server capable of making access determinations and revoking prior access rights.












![Designing A Scalable Workload Management System
2.4.1 Neutron Overview
Without including any network–specific functionality, it would be possible to develop a scalable
workload management system. While the connectivity between compute nodes is required and also
for the external access, it is important to have network–specific functionality, but it would be
possible to benefit from the existing networking infrastructure to allocate IP addresses and relay data
between nodes. However, the main problem with such an approach is the network management
system would not be able to separate traffic between users securely and efficiently when there will
be a multitenant environment[13]. Neutron is a part of OpenStack project focused on delivering
networking as a service and manages the ... Show more content on Helpwriting.net ...
A simple model of virtual network, subnet, and port abstractions to define network resources are the
base for creating OpenStack Networking component. Similar to a VLAN in the physical networking
world, network in OpenStack is an isolated layer–2 segment. Subnet is a block of IP version 4 or
version 6 addresses, set as an address pool from which OpenStack can assign IP addresses to virtual
machines (VMs). Each subnet is stated as a Classless Inter–Domain Routing range[13].
2.4.2 Neutron Architecture
The main process of the openstack networking component is neutron–server, which transmit user
requests from OpenStack Networking API to the configured plug–in. There are three agents that
interact with the main neutron process though the message queue or the OpenStack Networking
API[9]:
– Neutron–dhcp–agent: The main function of this agent is to provide Dynamic Host Configuration
Protocol (DHCP) service to all tenant networks[9].
– Neutron–l3–agent: The main function of this agent is to translate and forward Layer3/Networking
address to enable external network access for VMs on the tenant networks[9].
– Neutron–*–agent: This is an optional plug–in agent, which is responsible of performing local
virtual switch configuration on each hypervisor[9].
When Nova launches a VM instance, the service communicates with OpenStack Networking in
order to plug each virtual network interface into a particular port.
2.4.3 How Neutron works
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/applicationofanoperatingsystemsecurity-231113194125-dda8d9d9/85/Application-Of-An-Operating-System-Security-24-320.jpg)