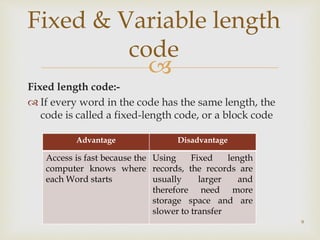
Huffman coding is a lossless data compression algorithm developed by David A. Huffman in 1952, which minimizes the average number of coding digits per message using variable-length codes based on character frequencies. It employs a greedy approach by merging the two smallest nodes to build a binary tree, and is widely used for efficient file compression in applications such as image and text transmissions. The method effectively reduces storage costs and transmission times by optimizing the encoding process for frequently used symbols.