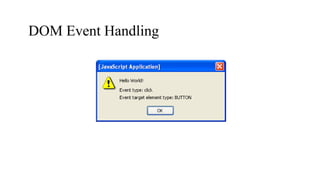
The document discusses the basic web security model, including browser content, the document object model (DOM), and the same origin policy. It provides details on how HTTP works with requests and responses between clients and servers. It also explains how web browsers function to display web pages and render HTML content. The DOM is described as an API that allows programs to interact with HTML documents and define their structure as a hierarchical tree of objects. Event handling and the same origin policy, which restricts interactions between pages from different origins, are also summarized.









![DOM: Referencing Objects
• The div is an element with an id of mydiv
• It contains a text element, which can be referenced by childNodes[0]
(childNode being an array of all childen of a node
• So the text in the div is not a value of the div, but rather the value of
the first (and only) childNode of the div
<div id="mydiv">
An Example Division
</div>](https://image.slidesharecdn.com/6-190819093318/85/Basic-web-security-model-11-320.jpg)