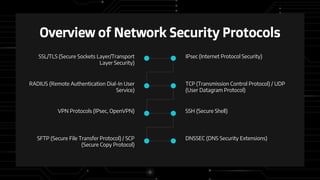
Network security protocols play a vital role in securing digital communication and establishing trust online. They provide encryption, authentication, access controls and other functions to protect data confidentiality, integrity and availability. Common protocols like TLS/SSL, IPsec, SSH ensure sensitive information is securely transmitted, while firewalls and VPNs control network traffic flow. Regular software updates, access controls and user awareness are important aspects of network defense. Recent incidents like the massive Yahoo breach demonstrate the consequences when security is insufficient and underscore the ongoing need for robust protocols and vigilance against cyber threats.