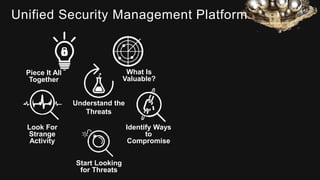
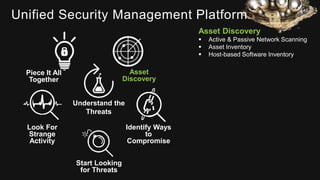
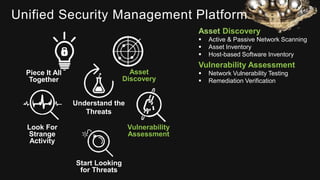
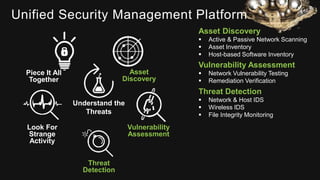
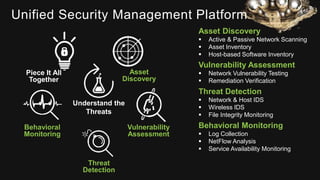
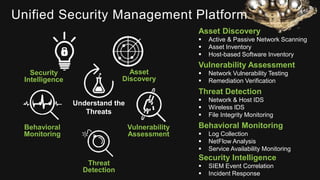
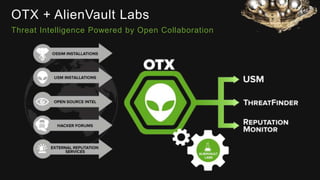
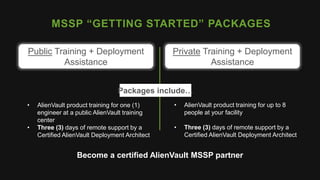
The document provides an overview of AlienVault's Managed Security Service Provider (MSSP) program, highlighting market challenges faced by MSSPs in delivering effective security solutions. It emphasizes the need for unified security management and integrated threat detection to address issues like poor correlation and limited log access. AlienVault's approach aims to offer comprehensive support and training to MSSPs, facilitating better security operations for organizations of all sizes.