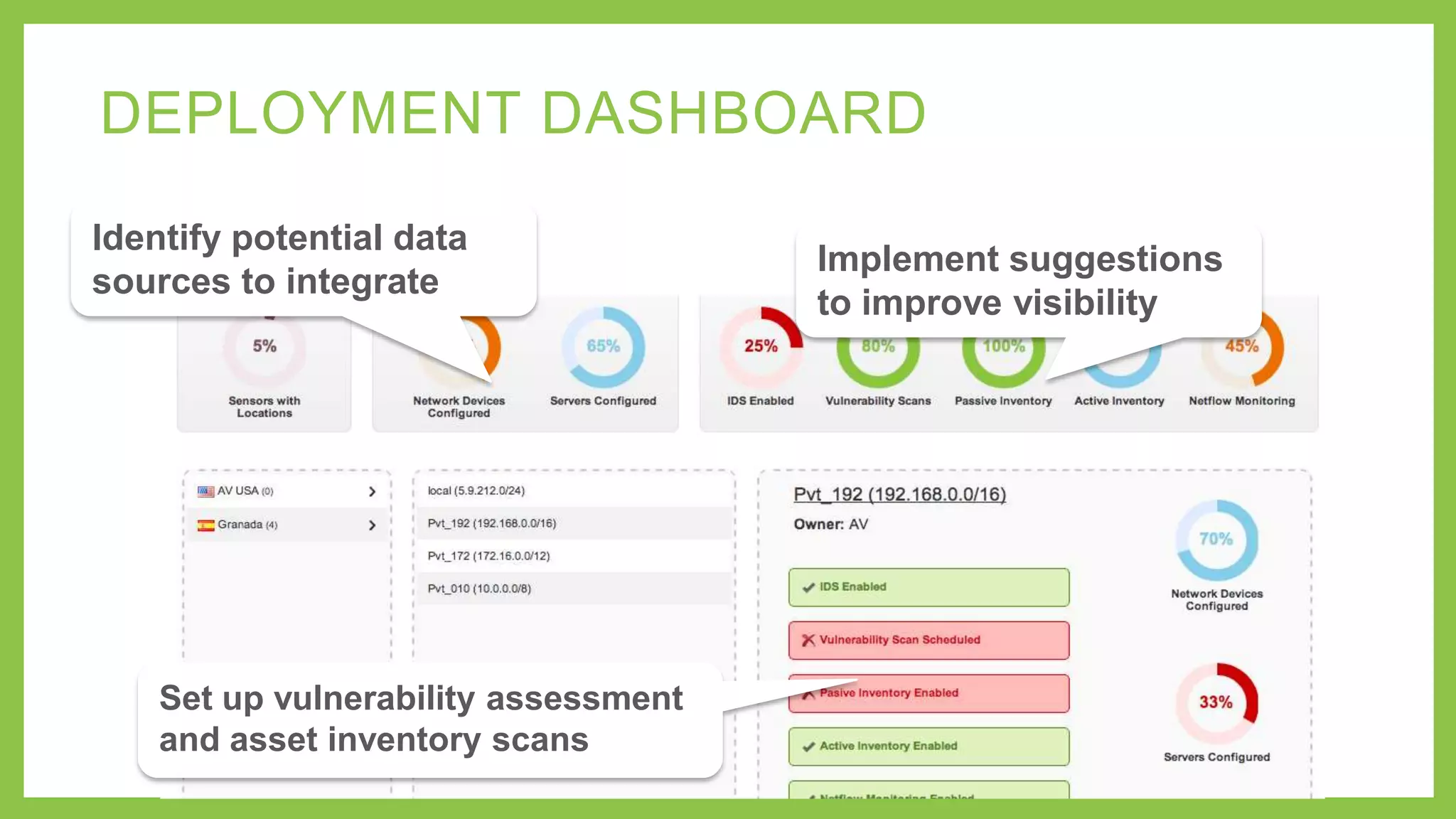
This document outlines six steps to ensure SIEM success: 1) Avoid single-purpose SIEM tools and look for built-in security controls, 2) Know your use cases before evaluating tools, 3) Imagine worst case scenarios for your business, 4) Include built-in threat intelligence, 5) Use IP reputation data to prioritize alarms, and 6) Automate deployment. It emphasizes the importance of integrated security tools to reduce costs and complexity, and knowing business needs and threats to properly focus the SIEM.