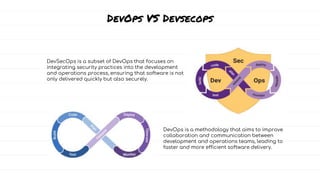
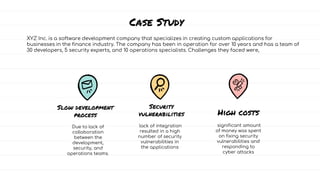
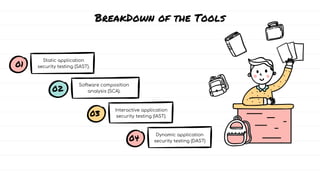
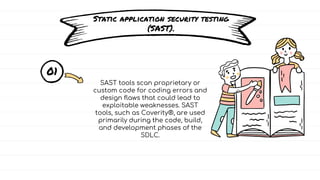
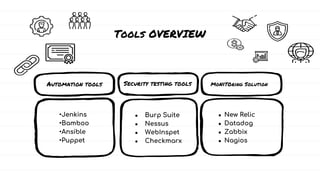
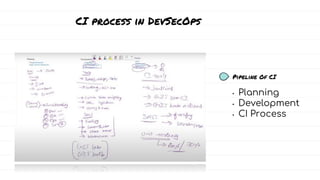
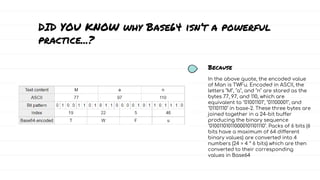
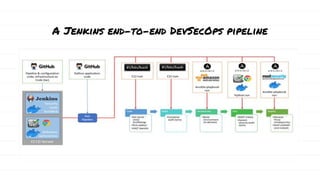
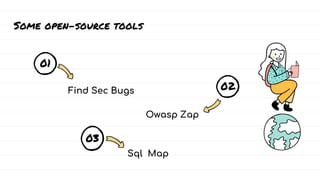
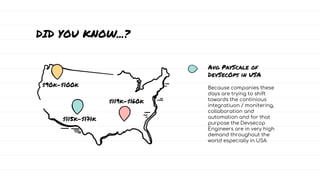
The document discusses DevSecOps, which integrates security practices into the DevOps development and operations process, enhancing software security while maintaining speedy delivery. It details a case study of XYZ Inc., highlighting their transition to DevSecOps to mitigate security vulnerabilities and costs through collaboration and automation. Additionally, it outlines various security testing tools and provides a tutorial for implementing DevSecOps in an organization.