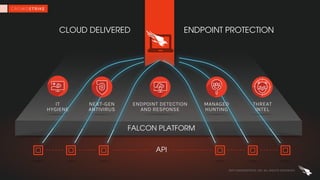
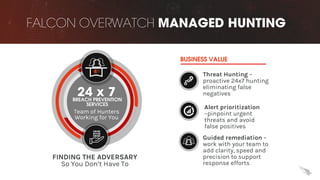
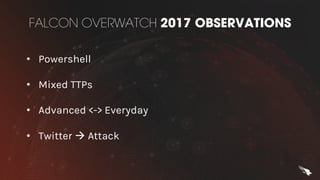
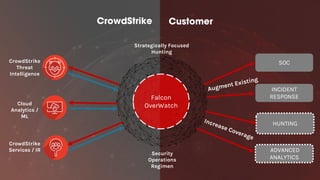
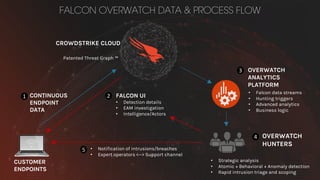
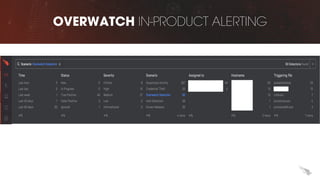
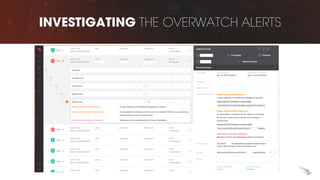
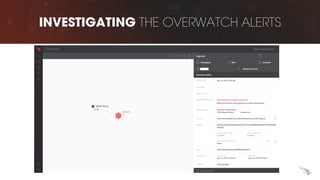
The document discusses proactive threat hunting as a vital endpoint protection strategy that goes beyond traditional alerting, emphasizing the need for managed detection and response to address emerging threats. It highlights the evolution of endpoint detection maturity and the benefits of proactive hunting through CrowdStrike's Falcon Overwatch service. The approach involves continuous investigation, prioritization of alerts, and collaboration with organizations to enhance response efforts and prevent significant security breaches.