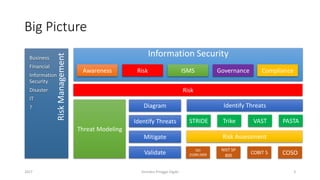
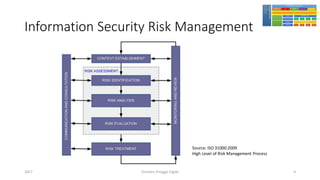
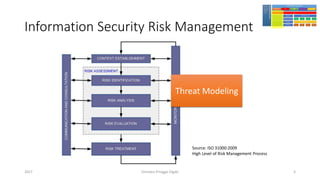
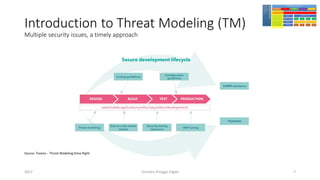
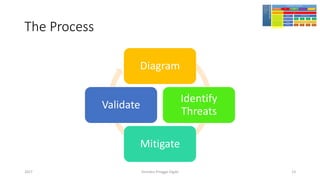
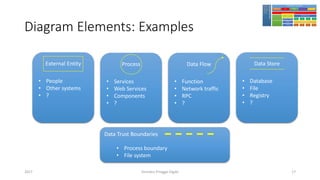
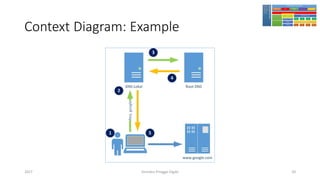
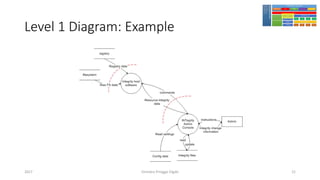
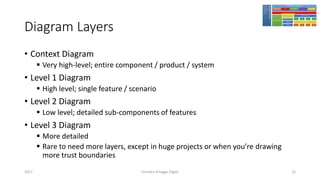
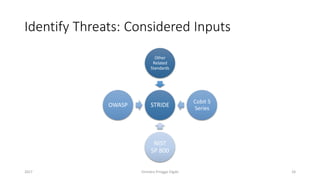
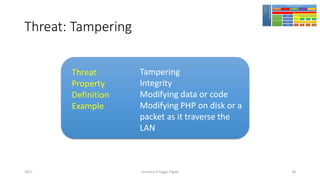
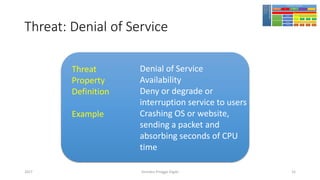
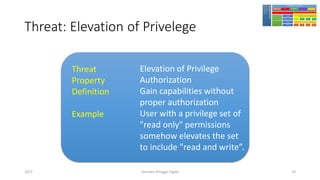
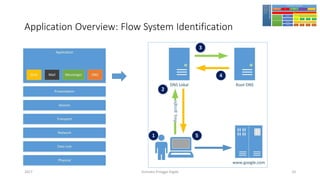
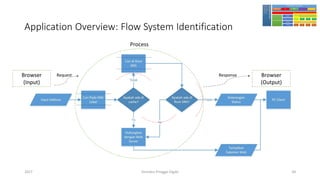
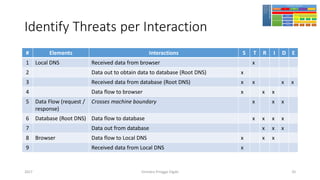
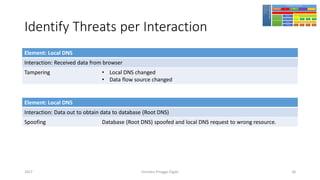
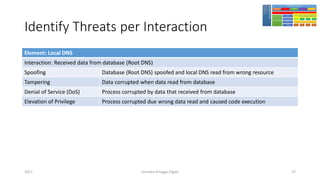
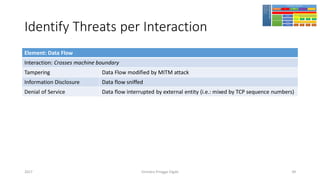
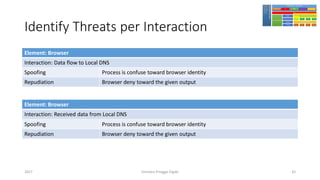
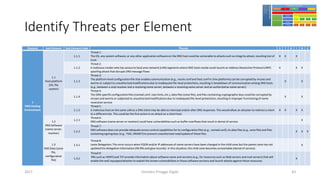
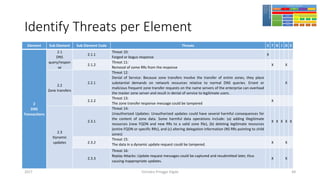
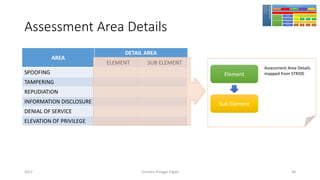
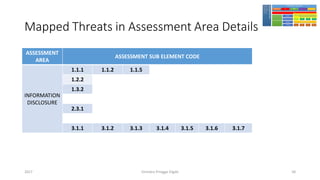
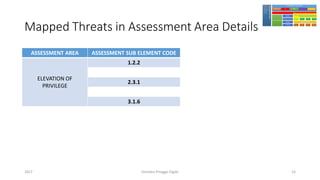
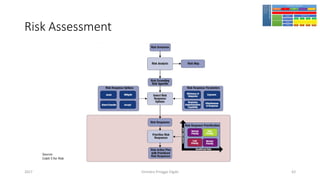
The document discusses threat modeling using STRIDE. It provides an overview of threat modeling and the STRIDE methodology. The document then shows an example of applying STRIDE to identify threats in a DNS system. Threats are identified for each element and interaction in diagrams of the DNS system. This includes threats to the hosting environment, DNS software, DNS data, DNS transactions, and dynamic updates.