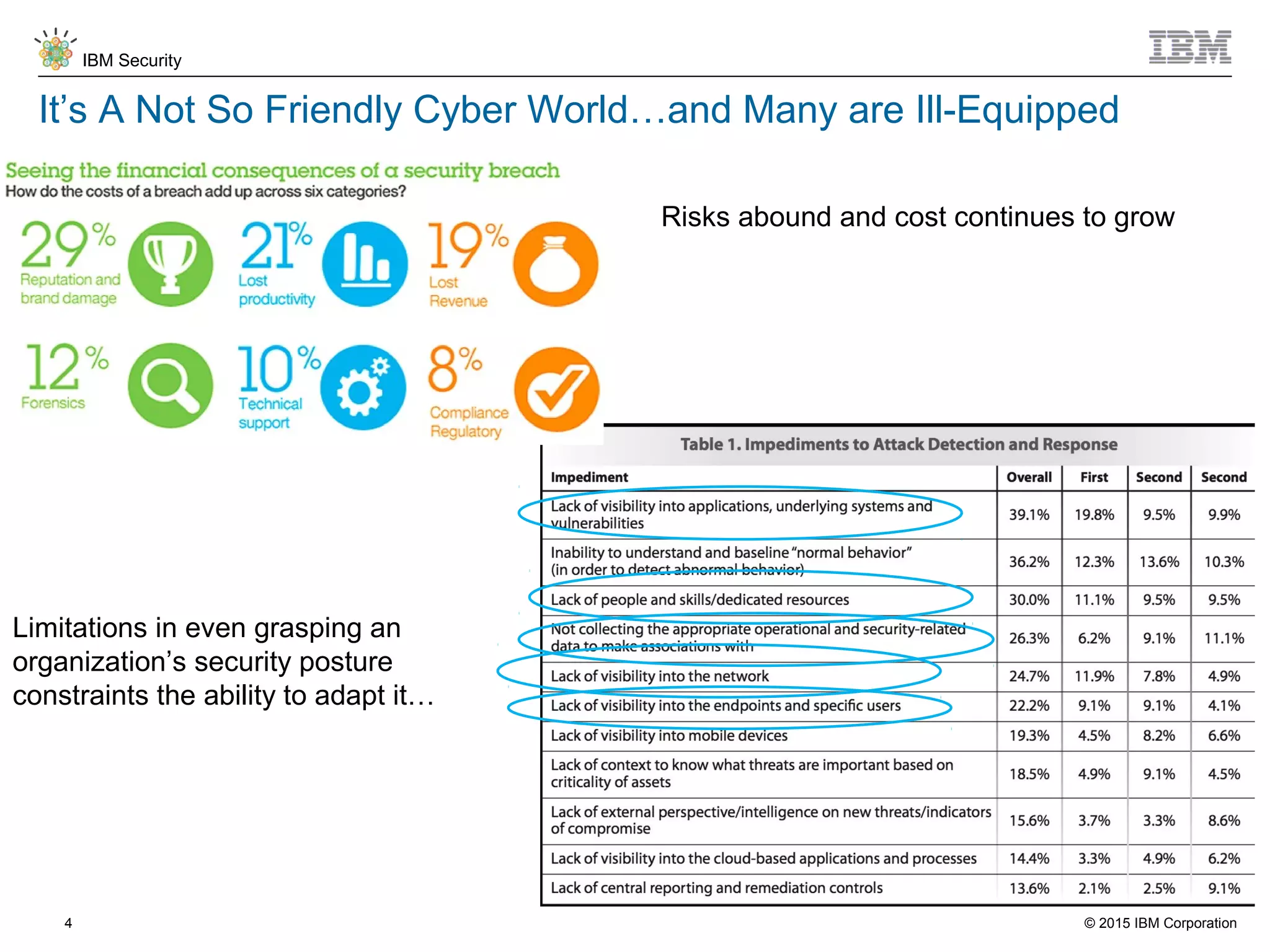
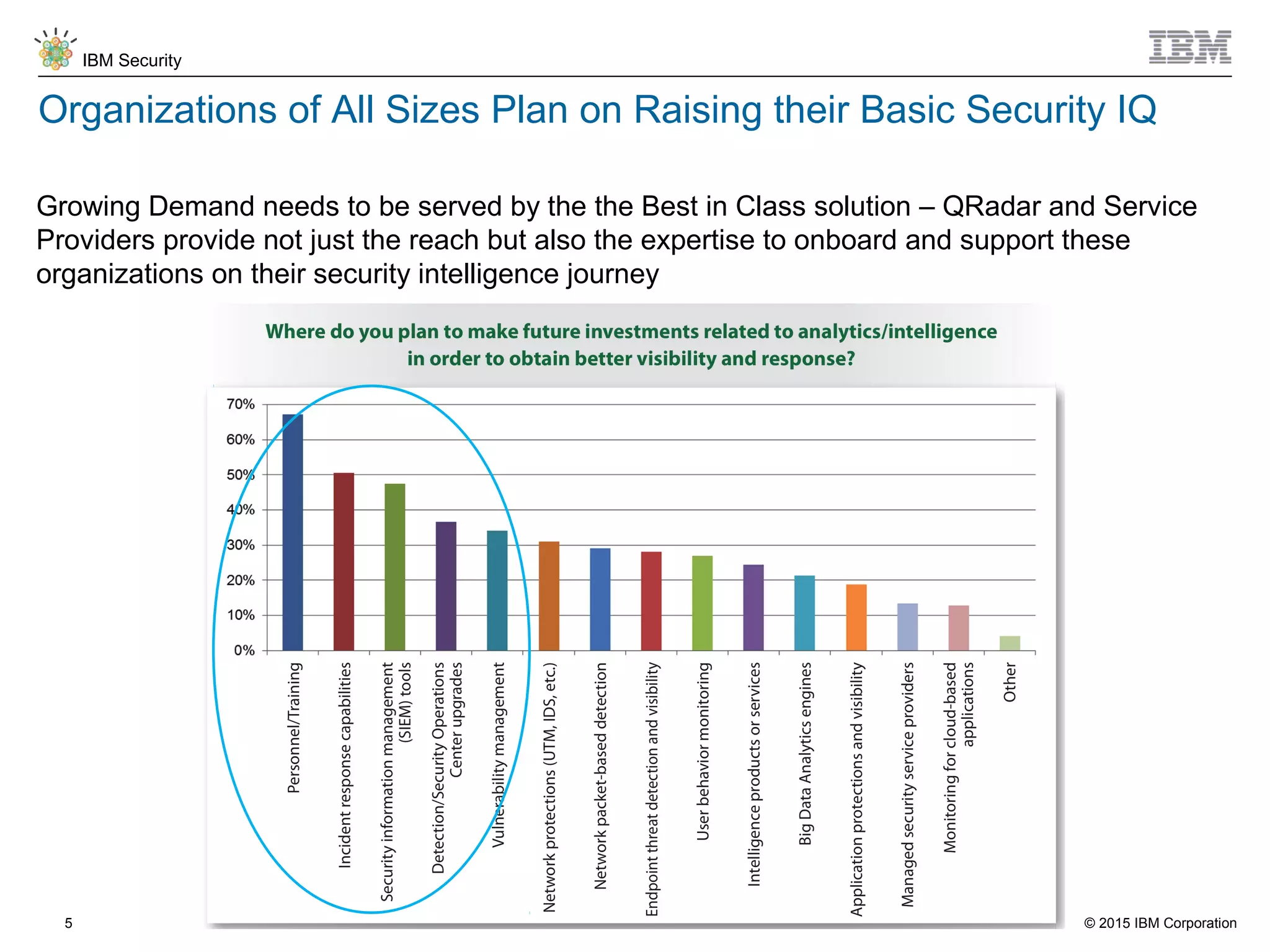
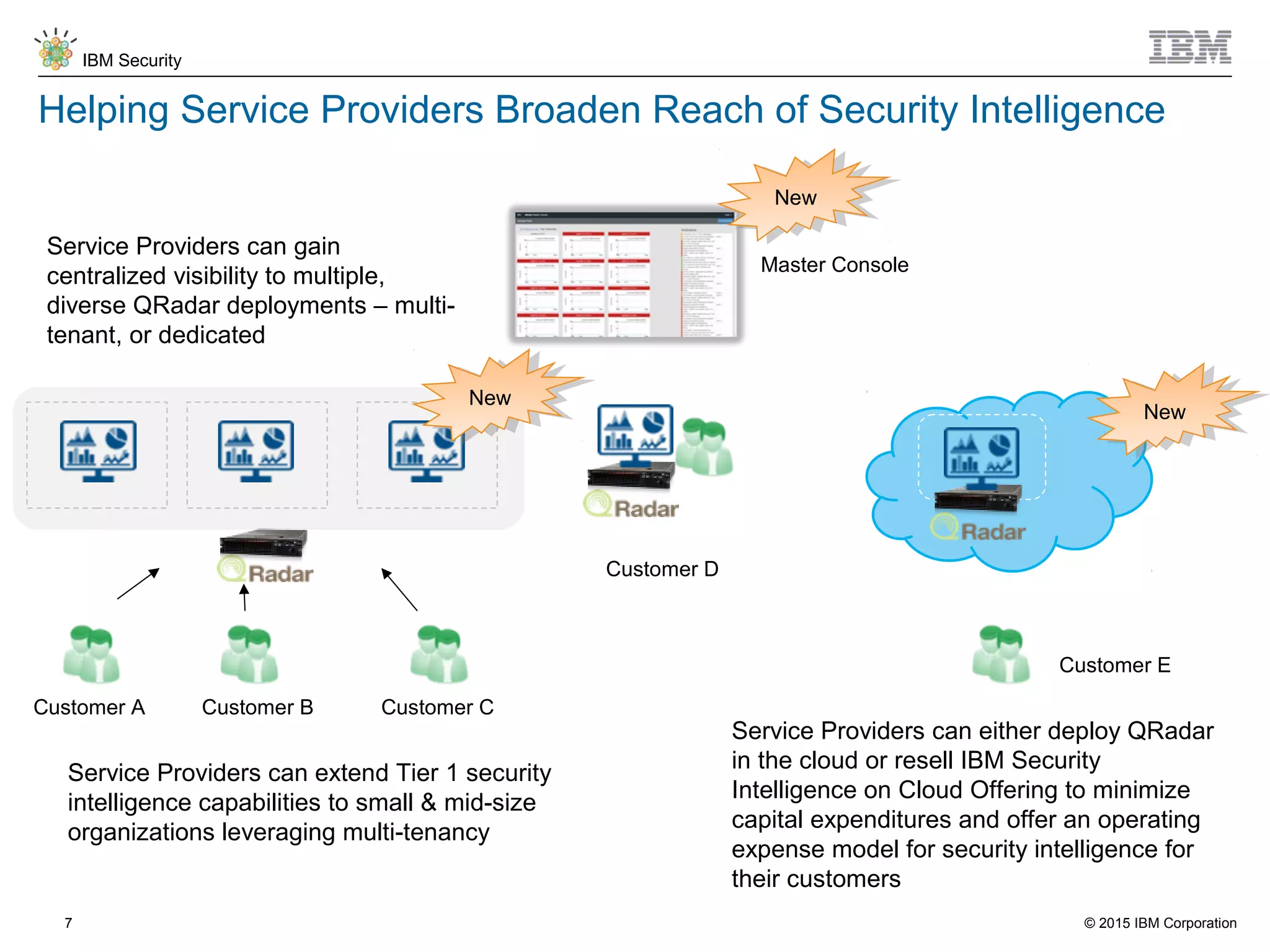
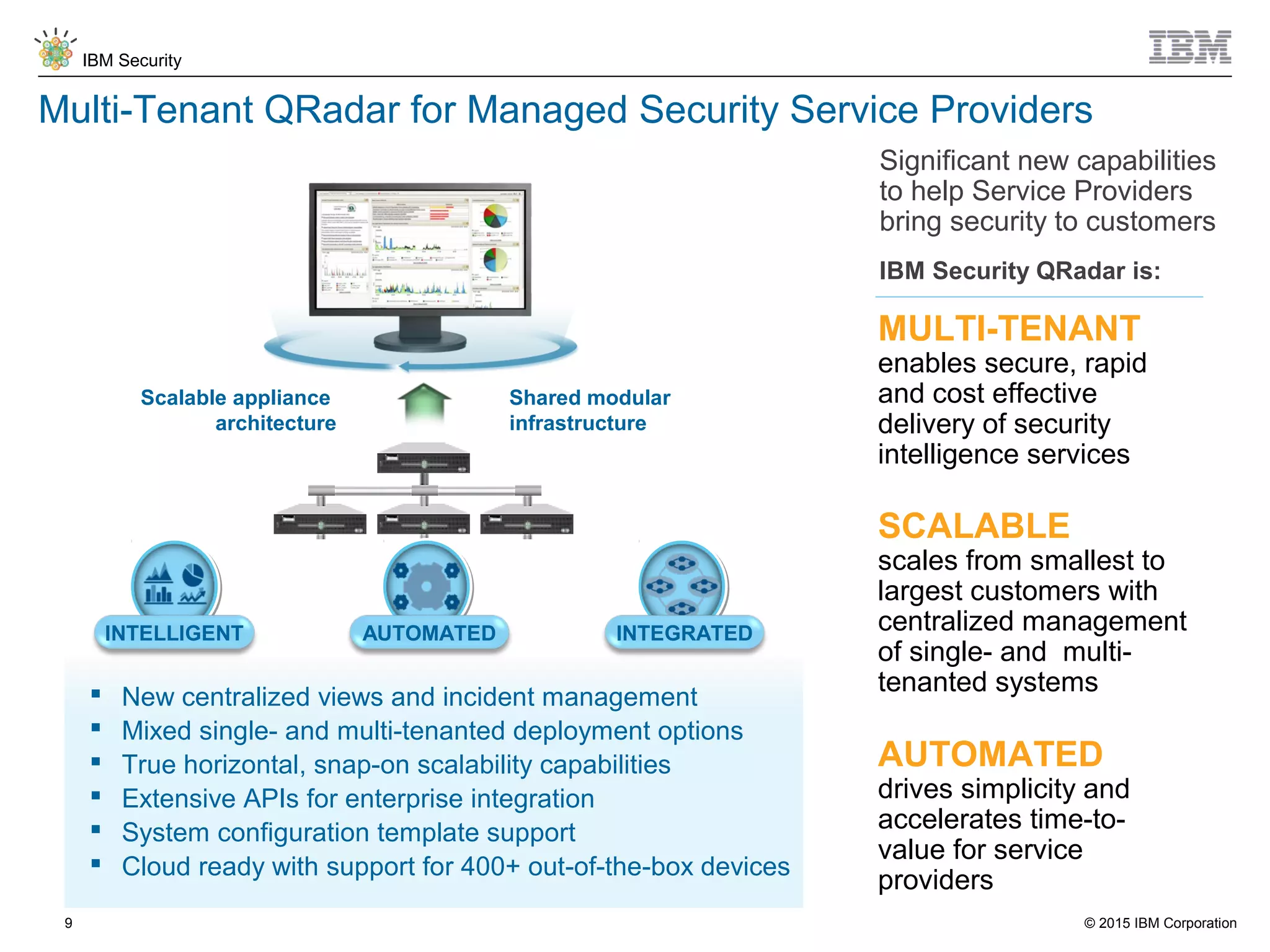
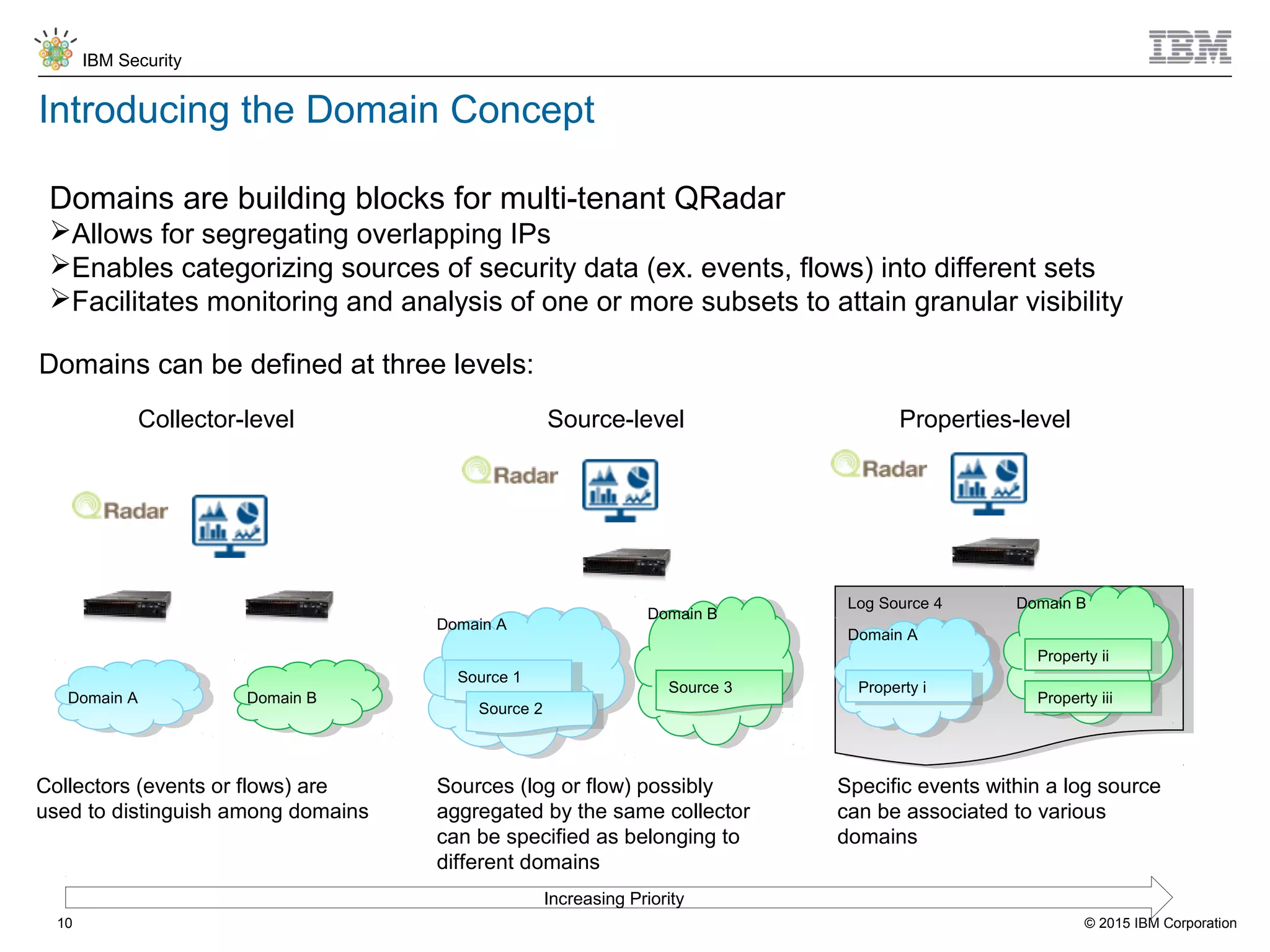
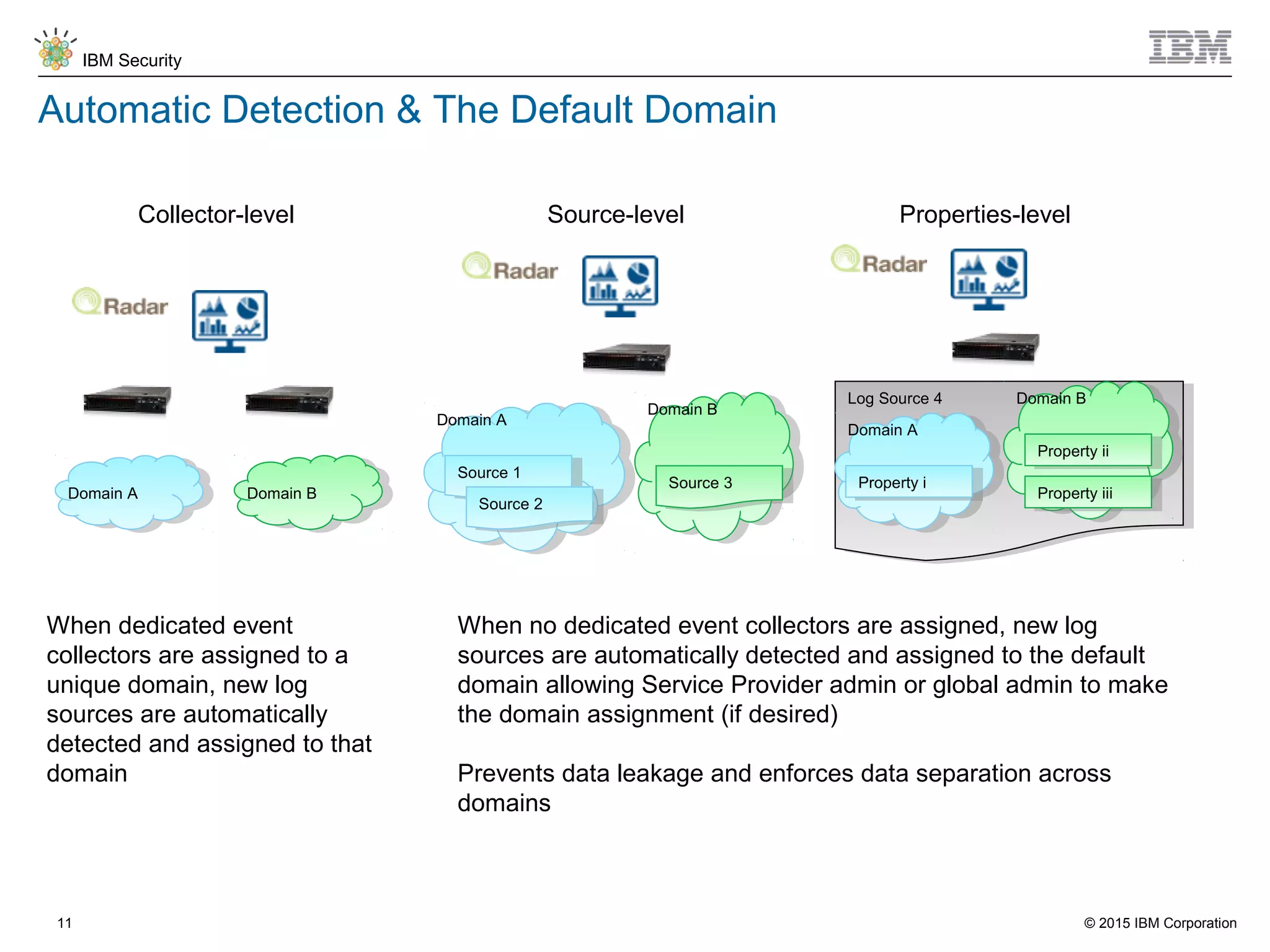
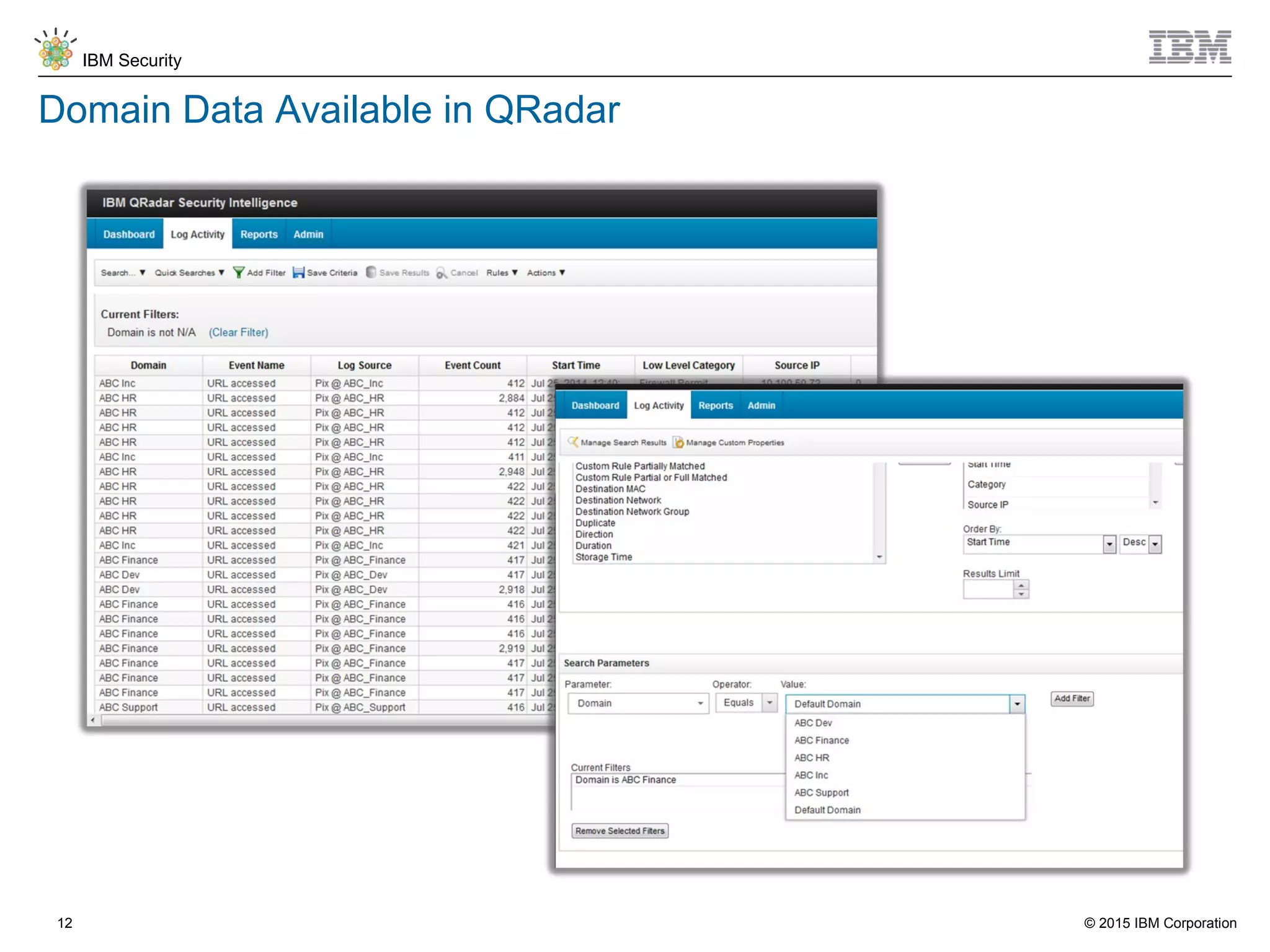
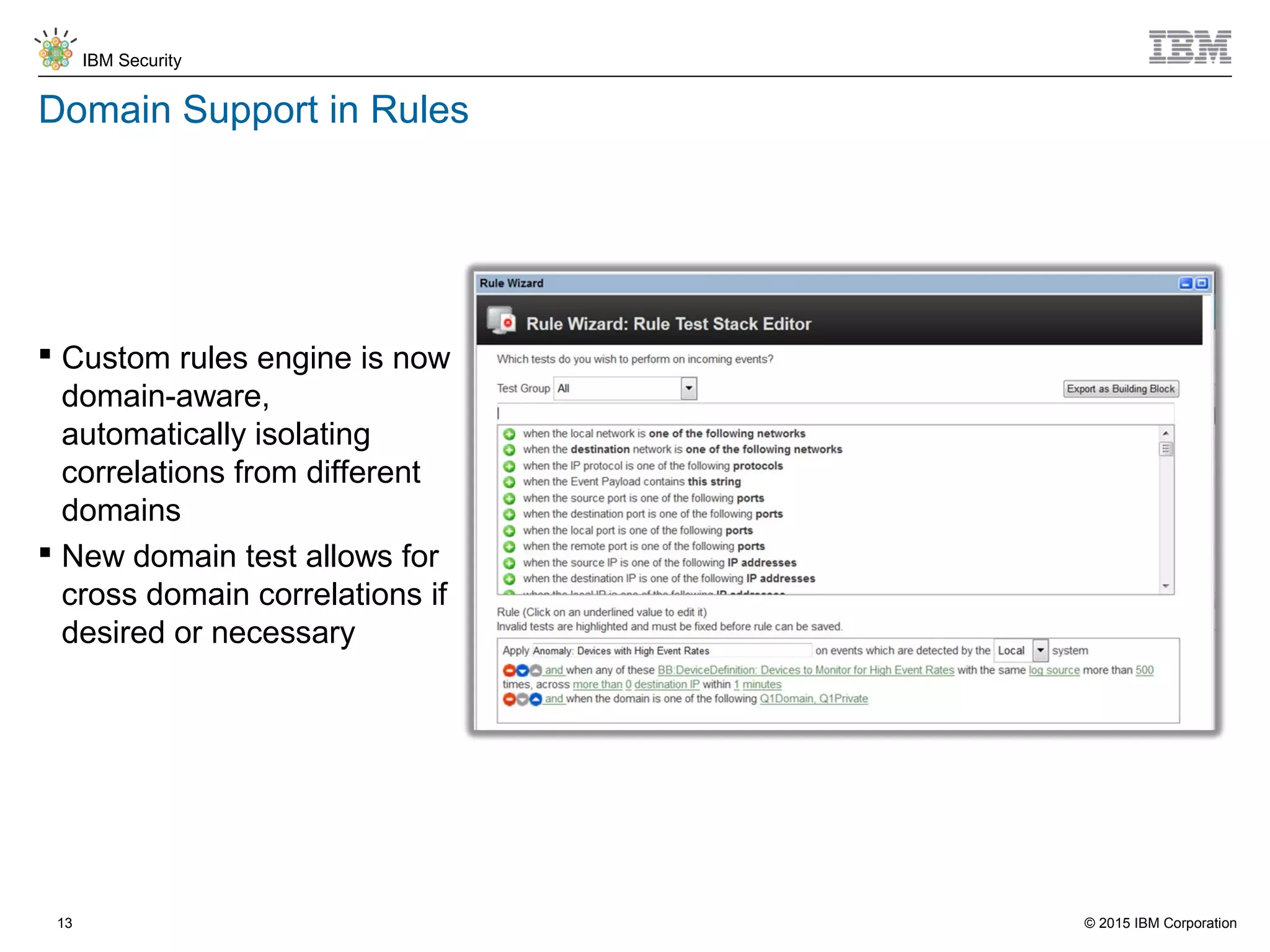
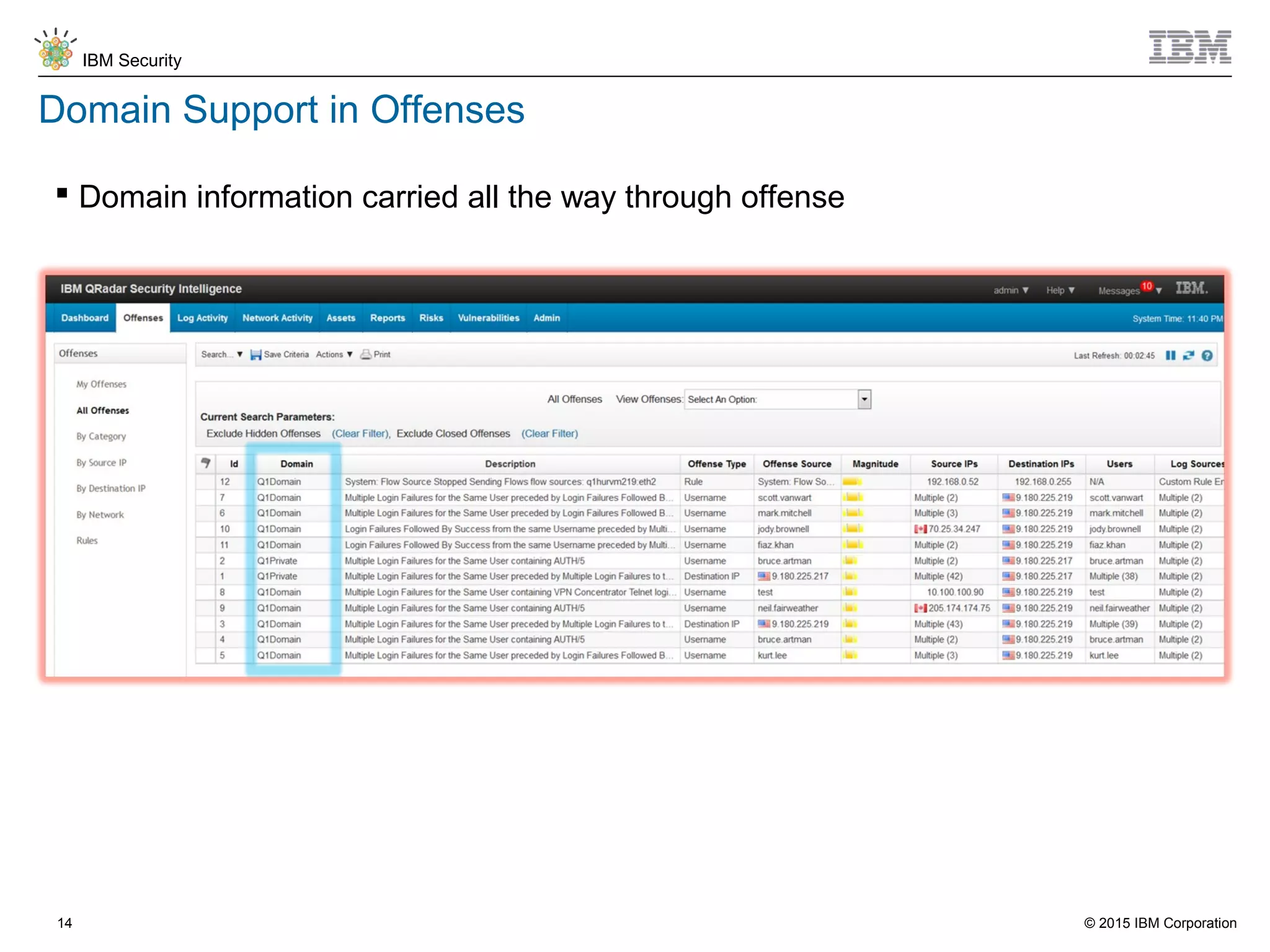
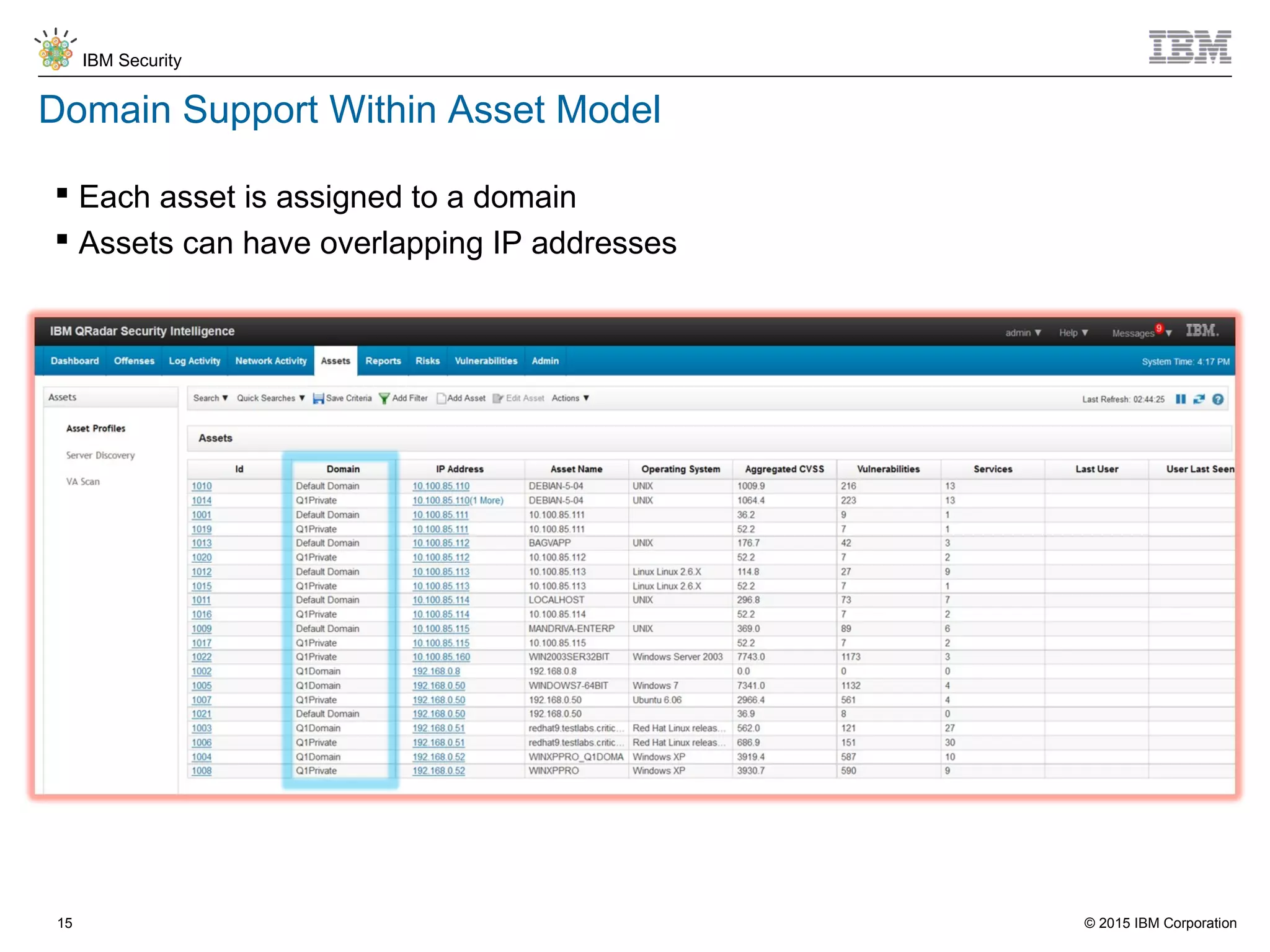
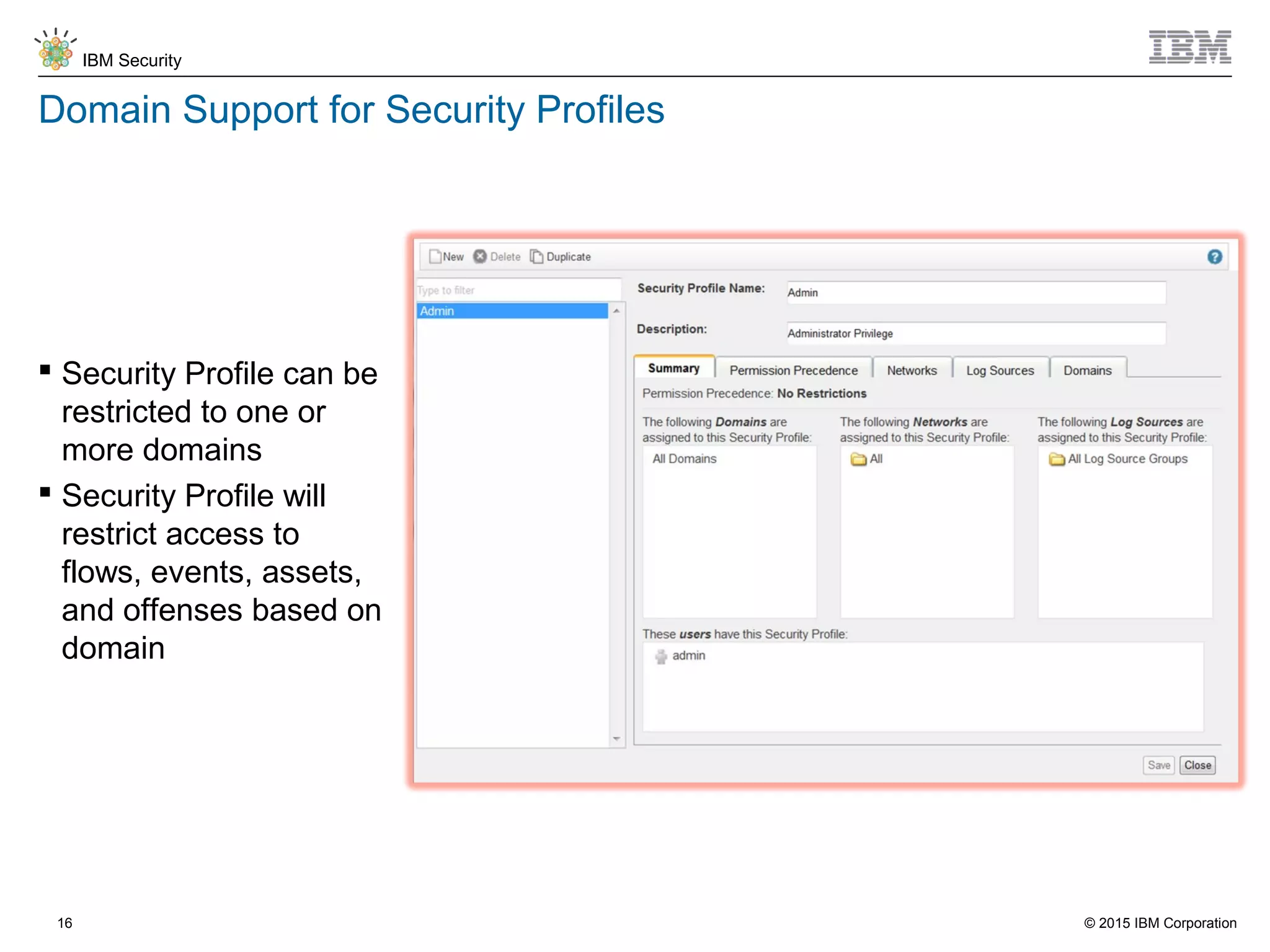
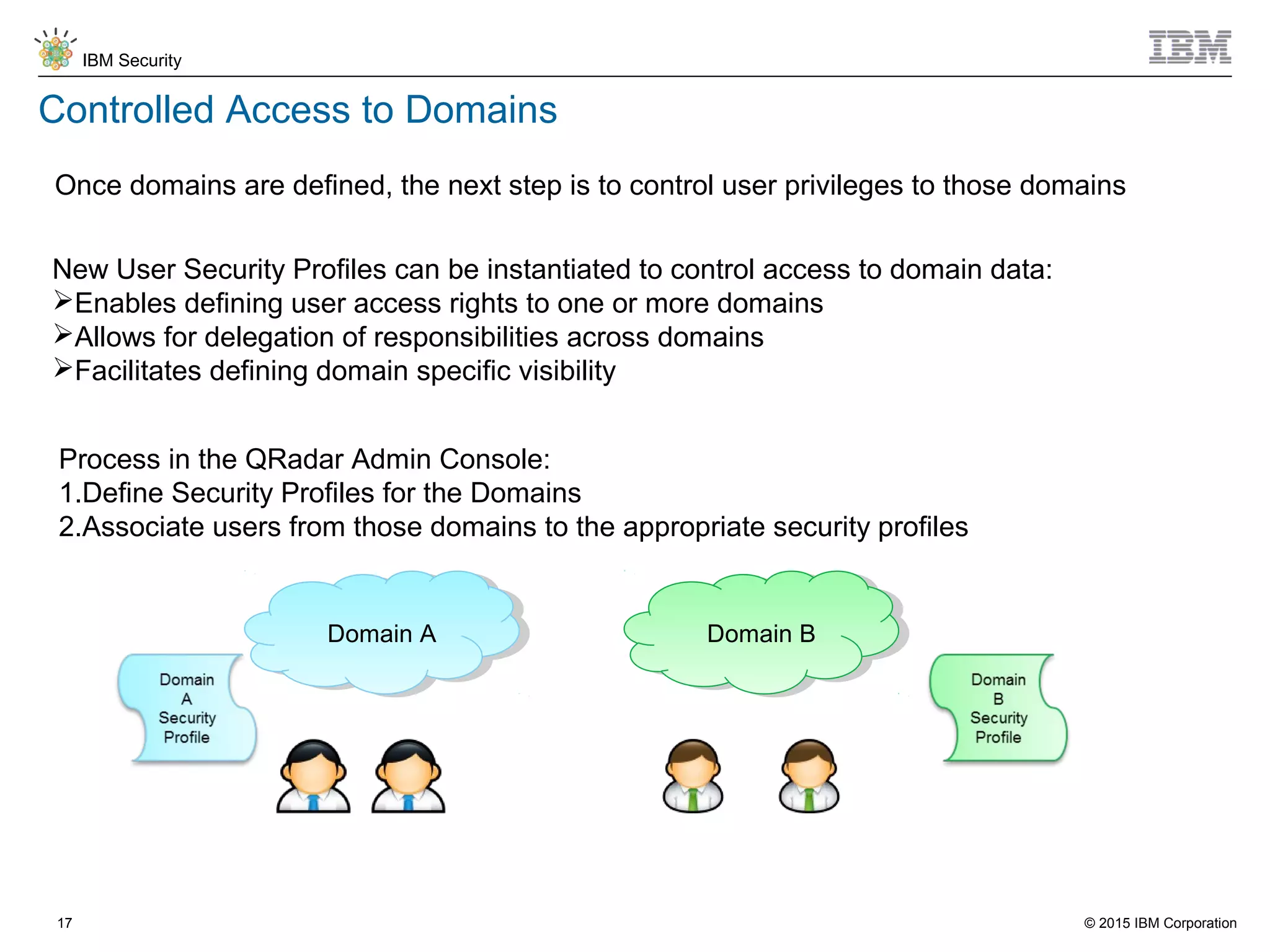
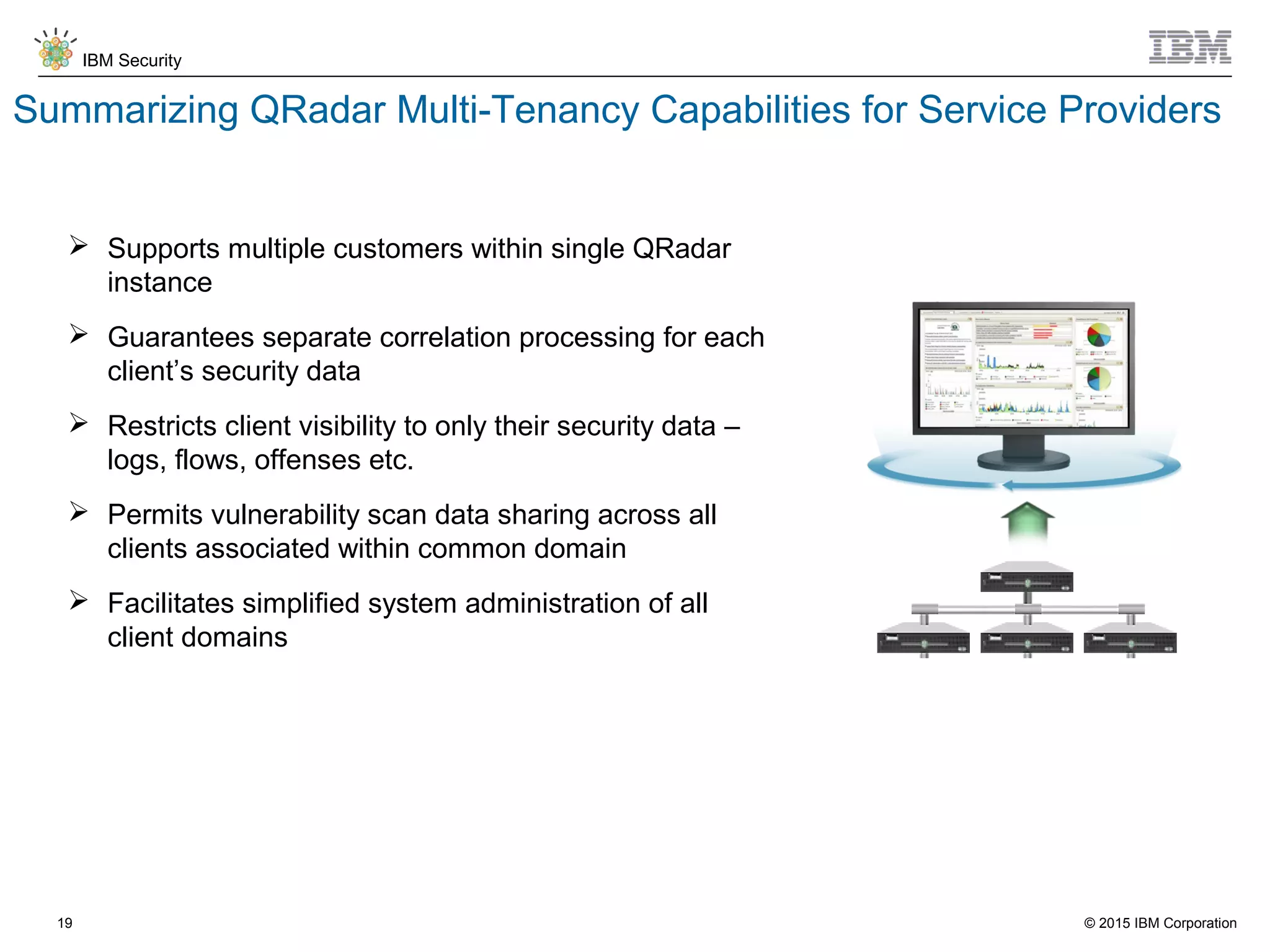
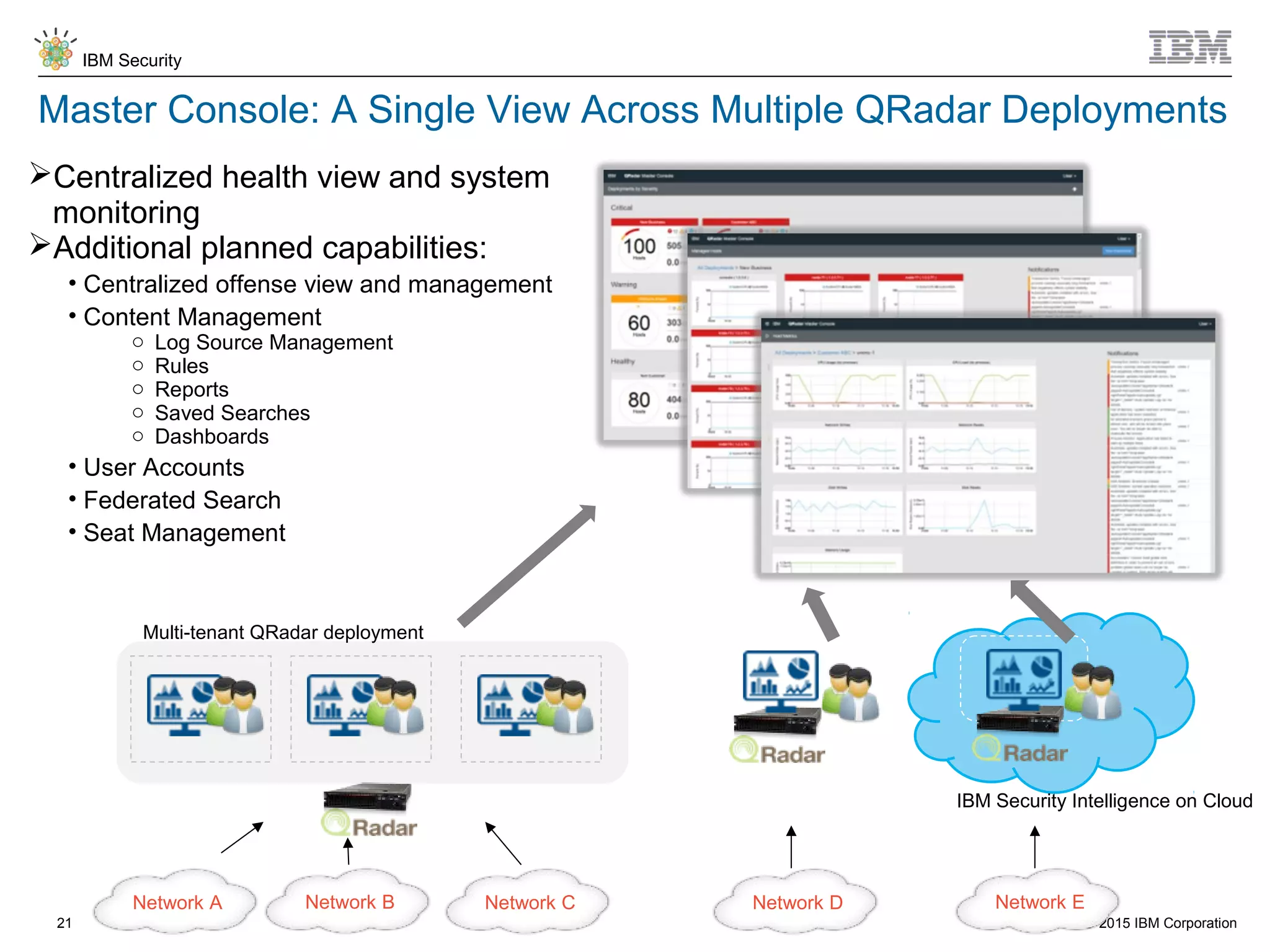
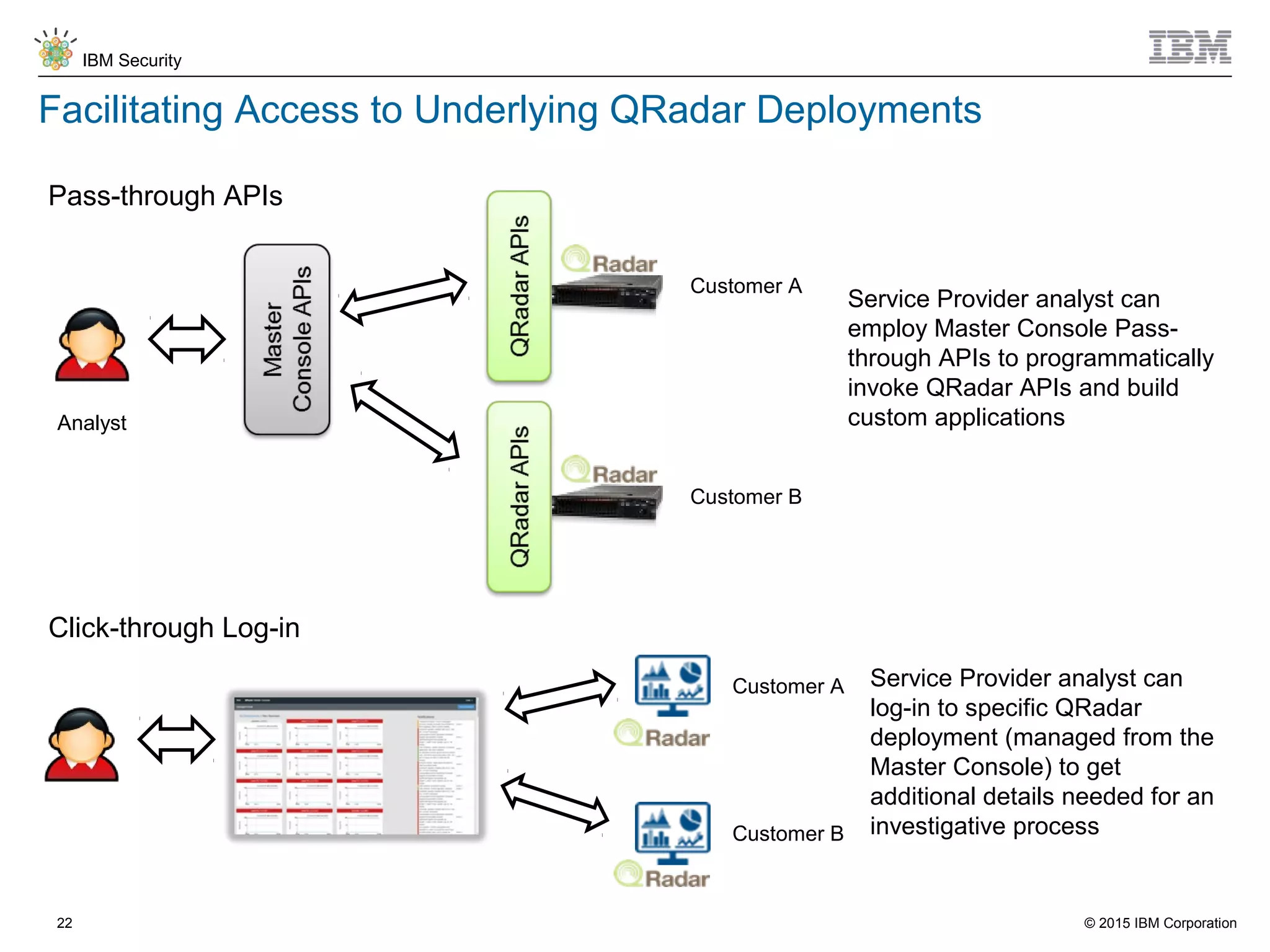
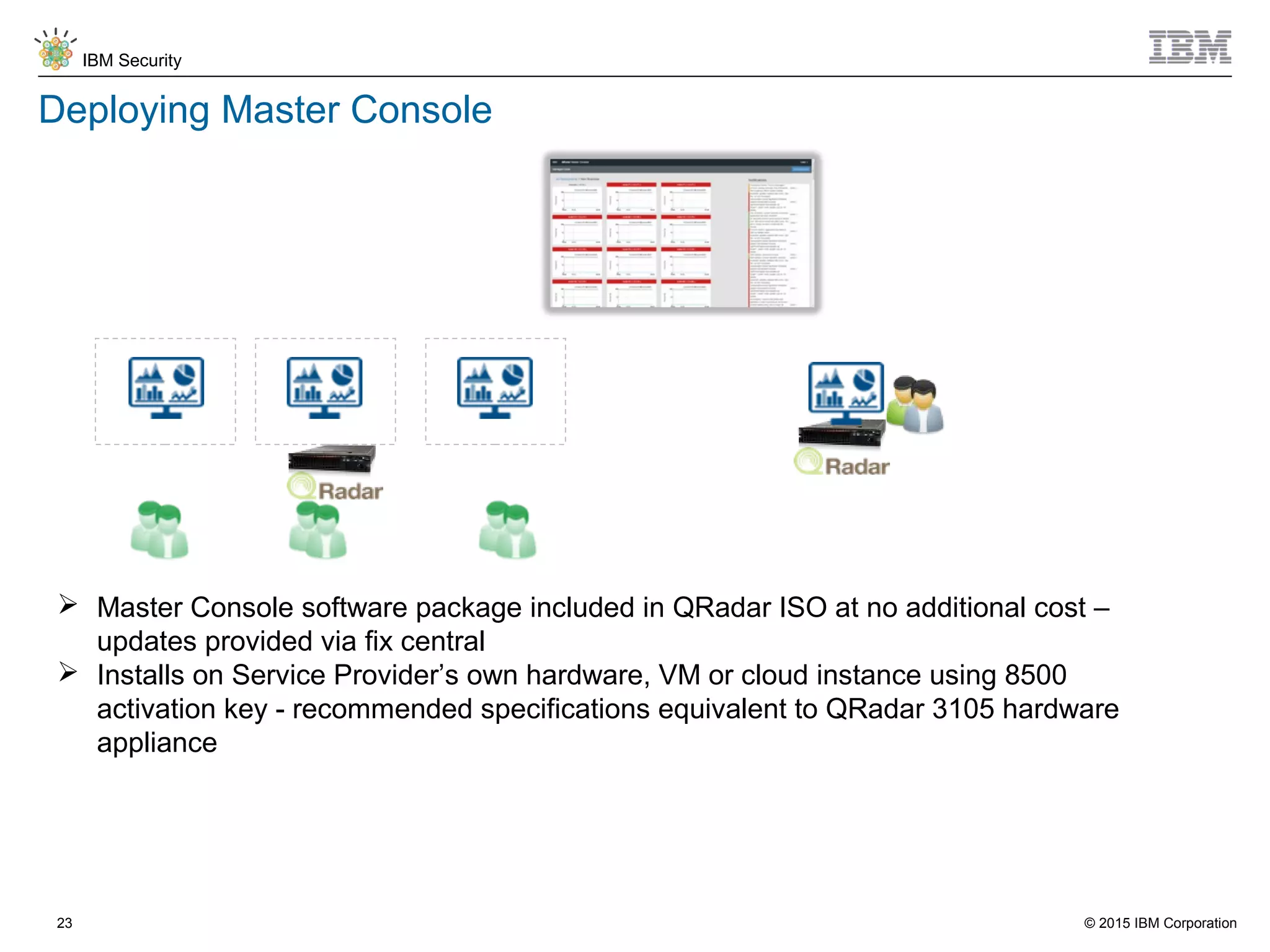
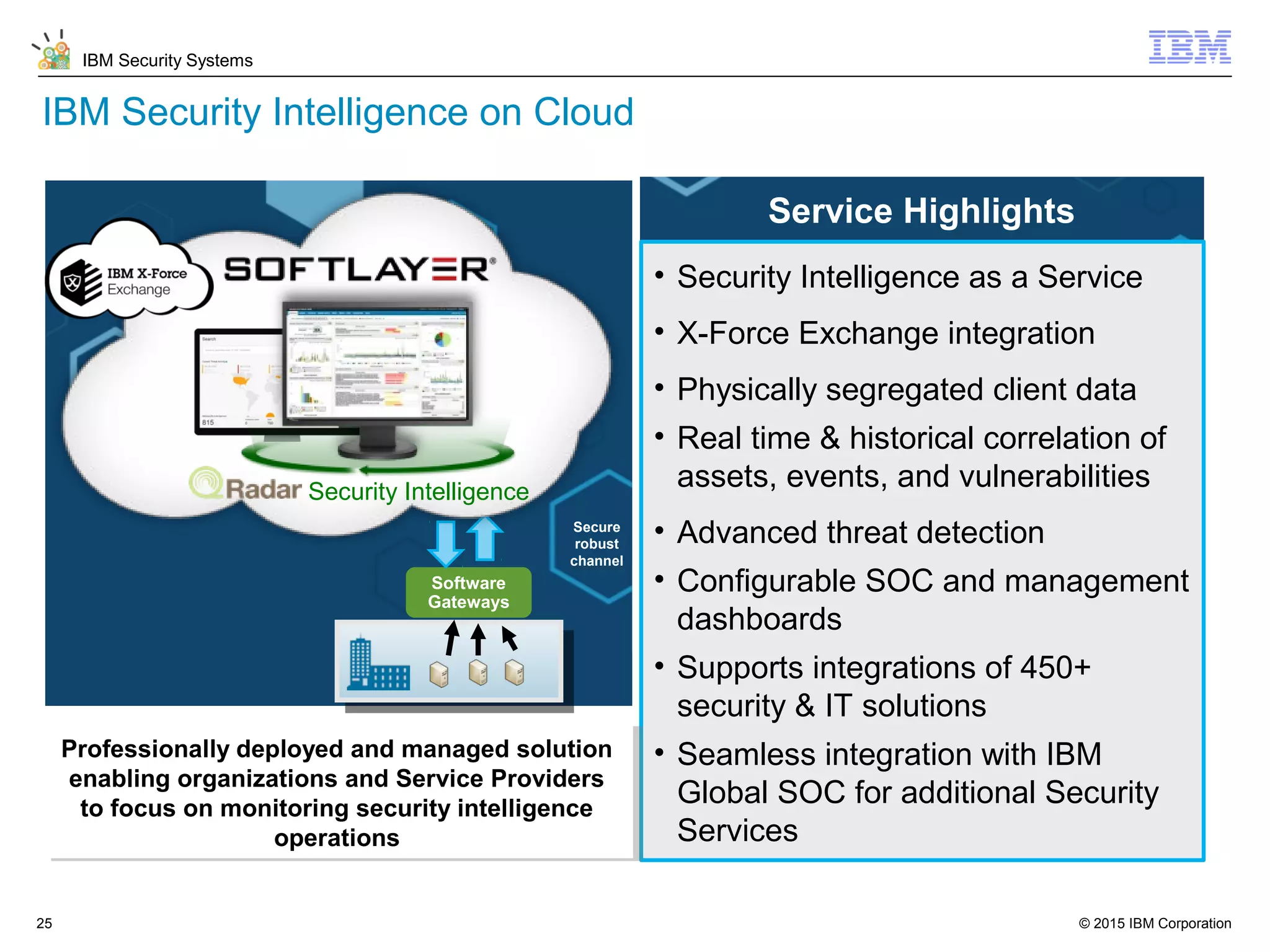
The document discusses IBM QRadar for service providers, emphasizing its multi-tenancy and SaaS capabilities that expand market reach and enhance security intelligence for various organizations. It outlines key functionalities, including centralized management, rapid deployment, and a customizable approach to security for different clients. Additionally, it highlights partnership opportunities and the flexibility of IBM's security solutions, aimed at empowering service providers with best-in-class capabilities.