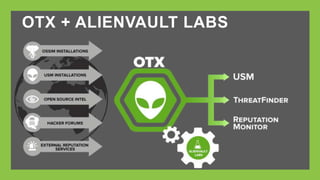
Open Threat Exchange (OTX) is an open information-sharing network that allows security professionals to access and share real-time threat data globally. It hosts the largest crowd-sourced repository for threat data, which expires after 30 days without additional evidence, and is focused on privacy by not collecting personal or internal information. OTX facilitates collaboration among users to enhance threat response through validated threat intelligence and analysis.