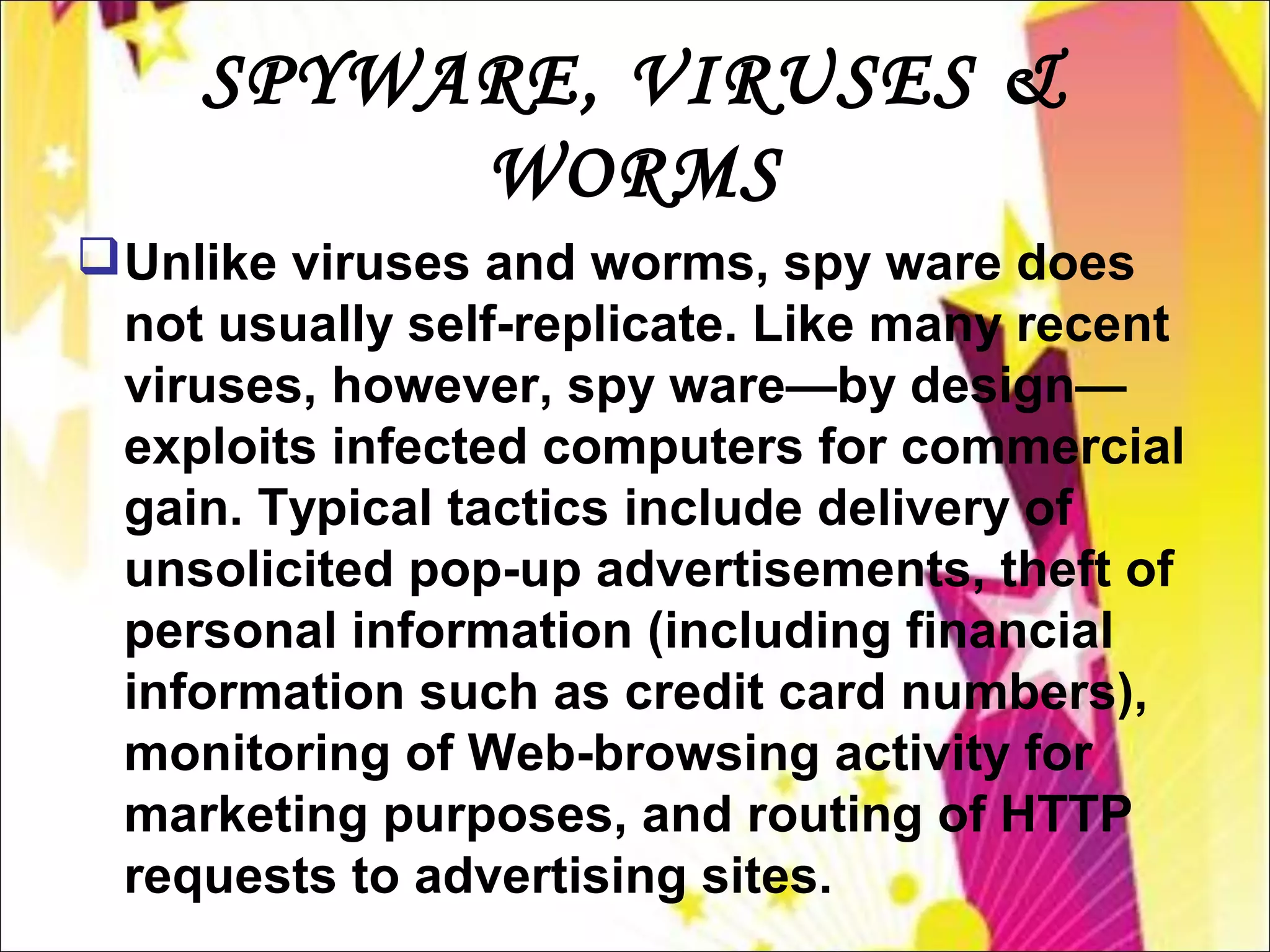
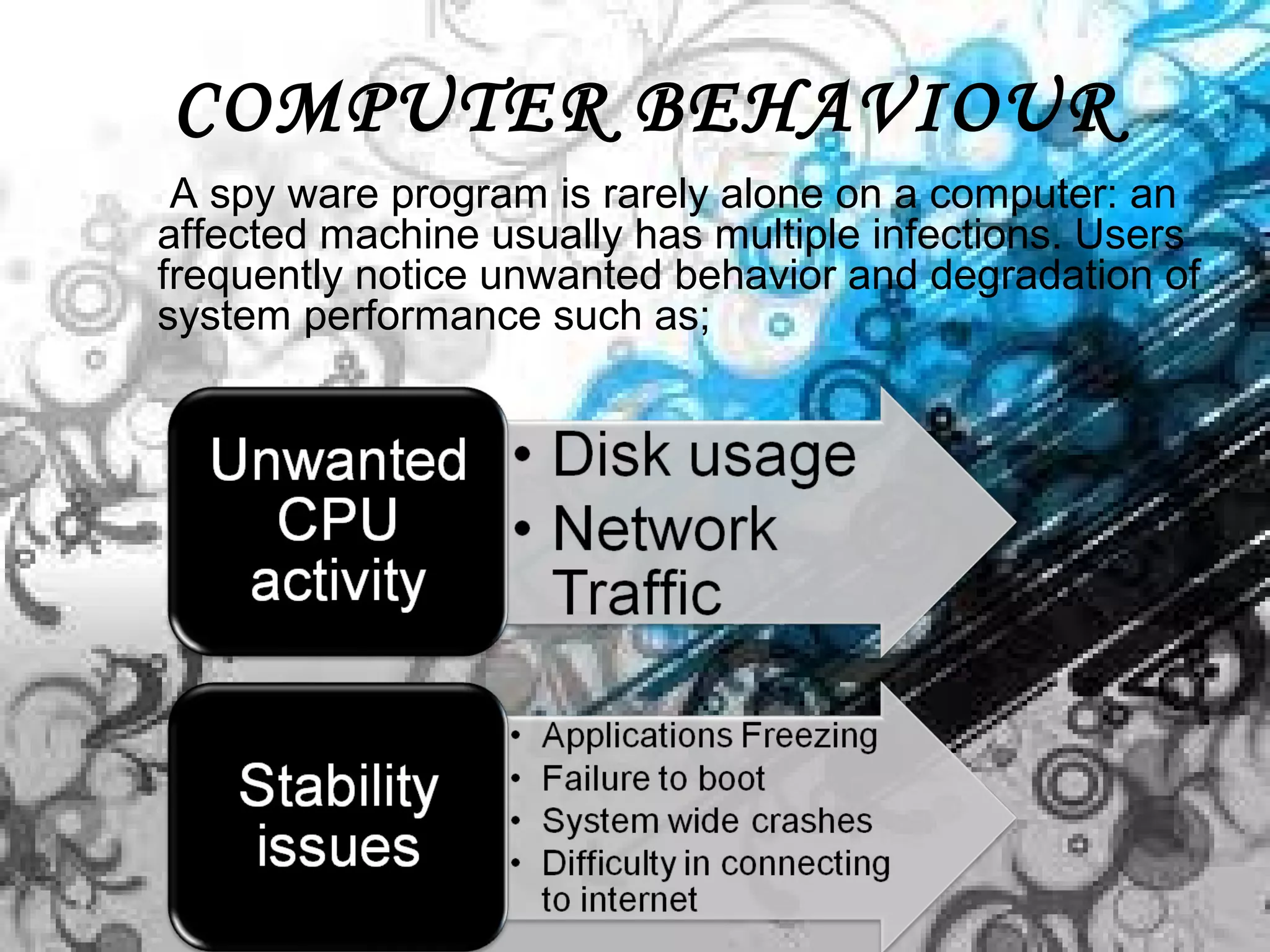
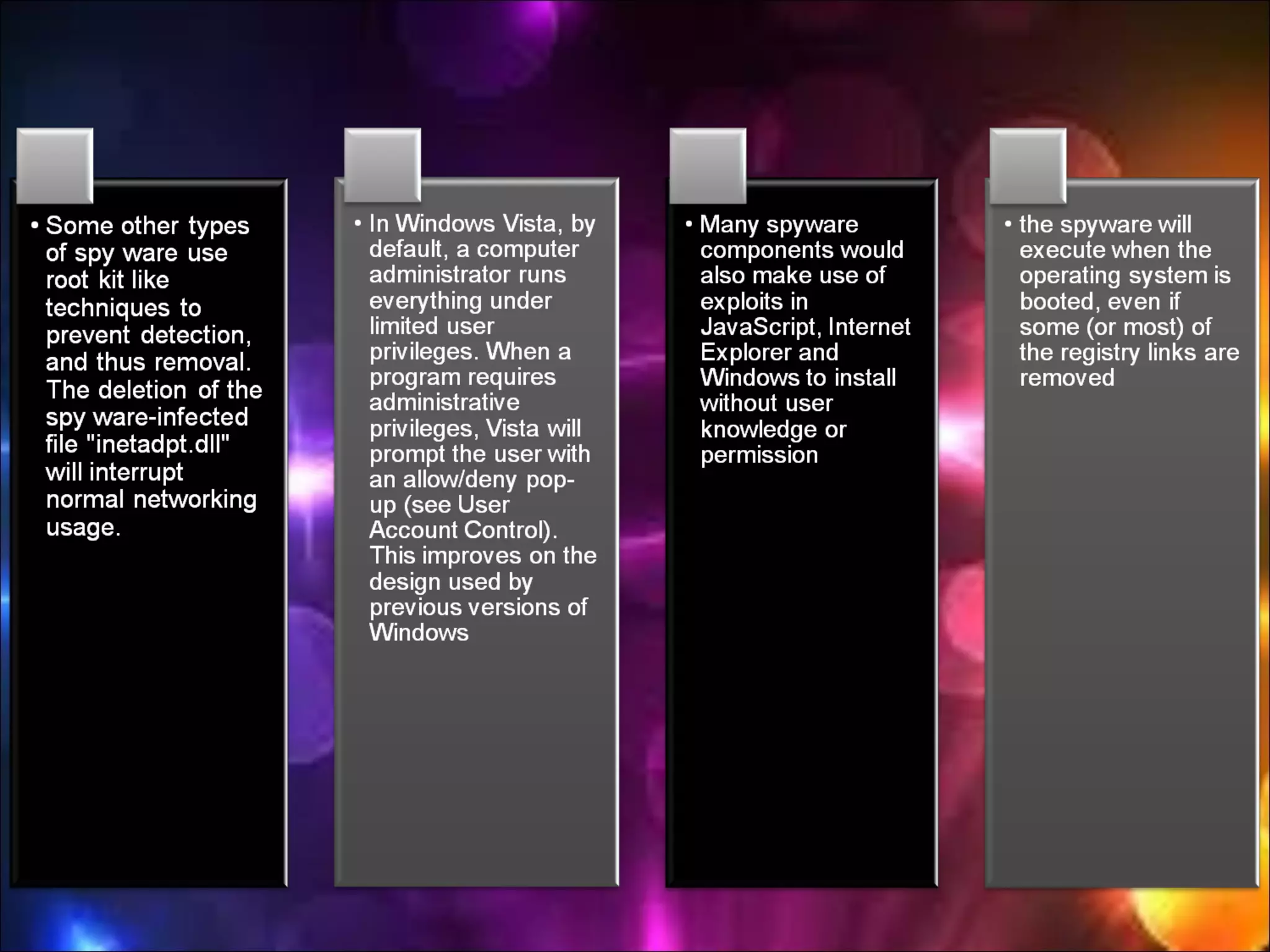
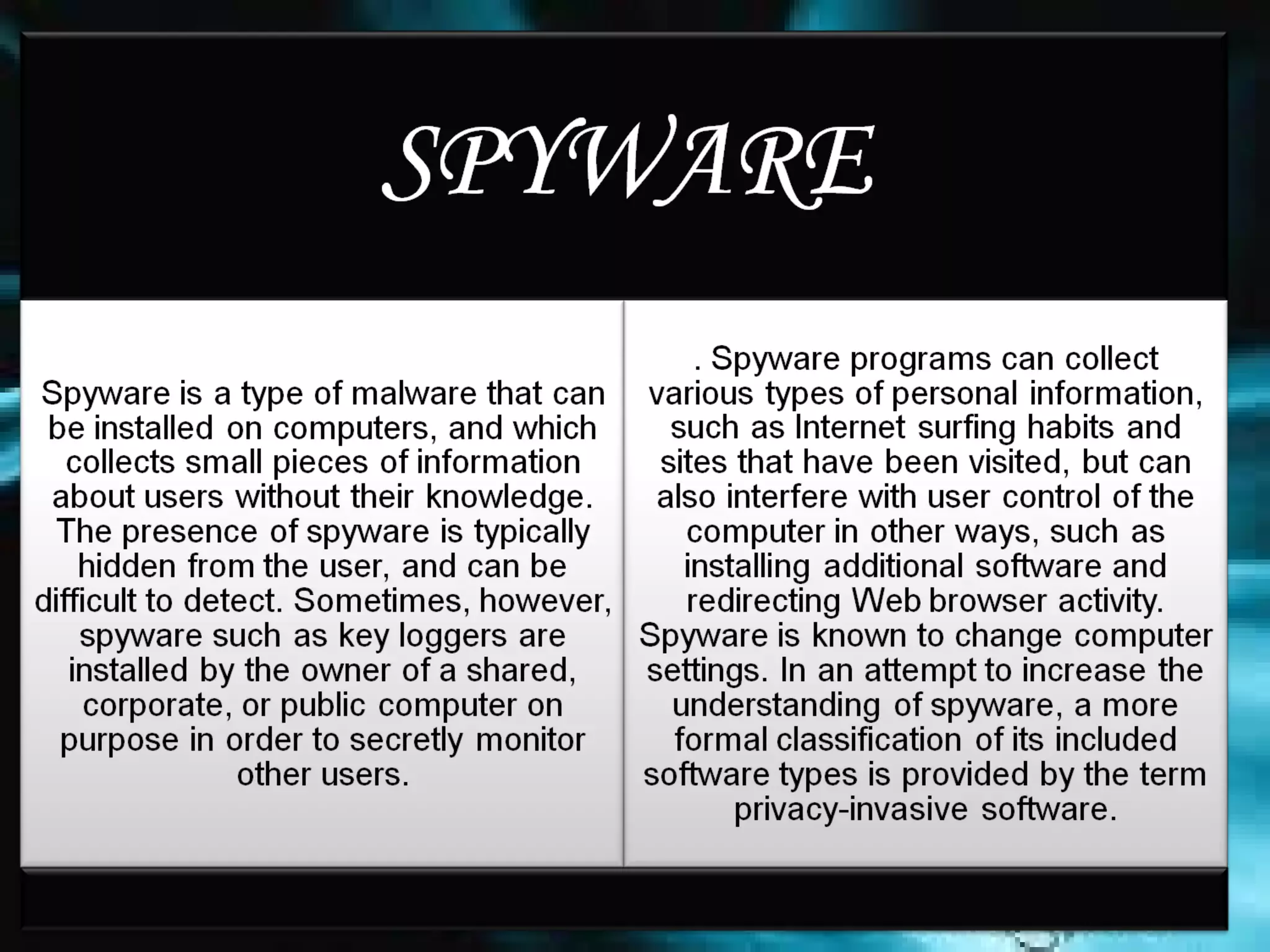
Spyware refers to software that is installed on an user's computer without their consent and is used to collect information about their internet activity. Unlike viruses and worms, spyware does not self-replicate but exploits infected computers to display unsolicited ads, steal personal information, and monitor browsing activity. Users typically notice unwanted ads, reduced performance, and changes to browser settings due to multiple spyware infections. While anti-spyware software and safe computing practices can help detect and remove spyware, rogue anti-spyware programs also pose a threat by falsely claiming to find infections.

![DEVELOPMENT
.
• The first recorded use of the term spyware
occurred on 16 October 1995 in a Usenet post
that poked fun at Microsoft's business model.[1]
Spyware at first denoted software meant for
espionage purposes. However, in early 2000 the
founder of Zone Labs, Greg or Freund, used the
term in a press release for the Zone Alarm
Personal Firewall. Since then, "spyware" has
taken on its present sense.](https://image.slidesharecdn.com/spyware-140824040336-phpapp01/75/Spyware-3-2048.jpg)