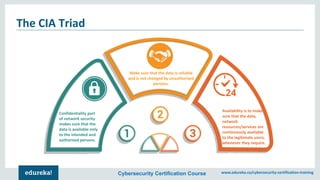
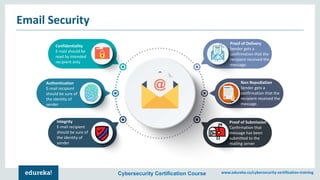
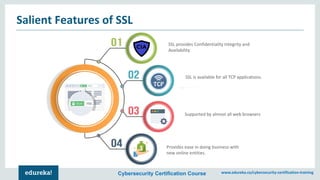
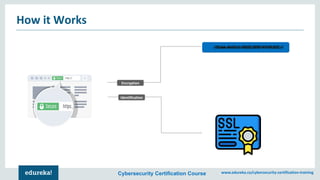
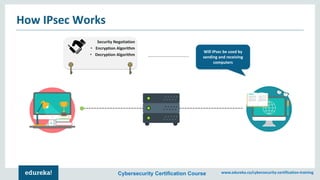
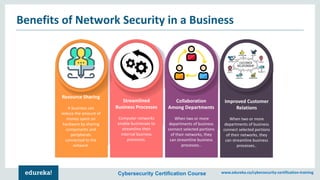
The document outlines a cybersecurity certification course offered by Edureka that emphasizes the importance of network security, including its components such as hardware and software technologies. It covers key concepts like vulnerabilities in TCP/IP, the CIA triad (confidentiality, integrity, availability), application and transport layer security, and SSL protocols. Additionally, the document discusses the benefits of network security for businesses, including resource sharing and improved customer relations.