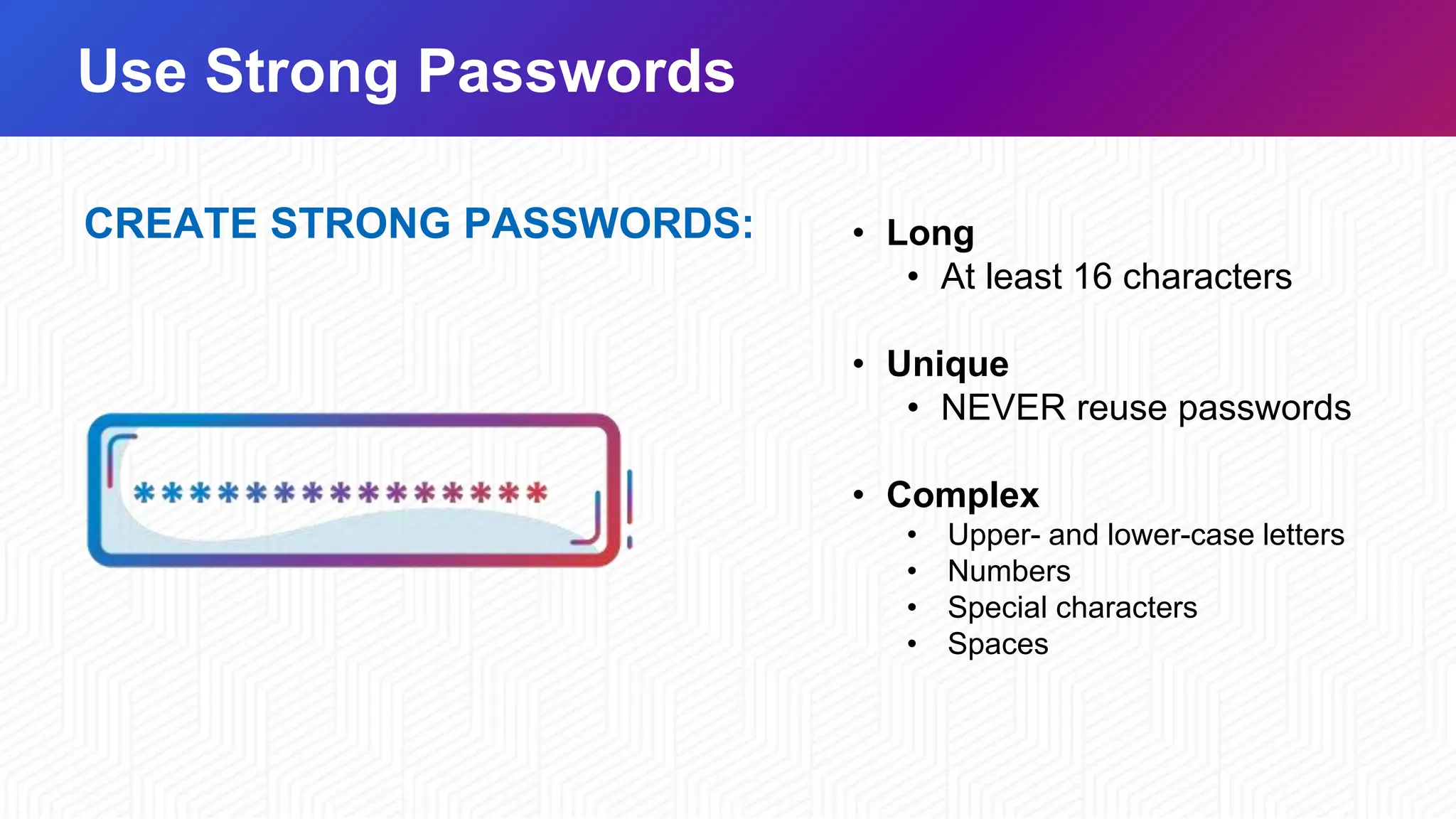
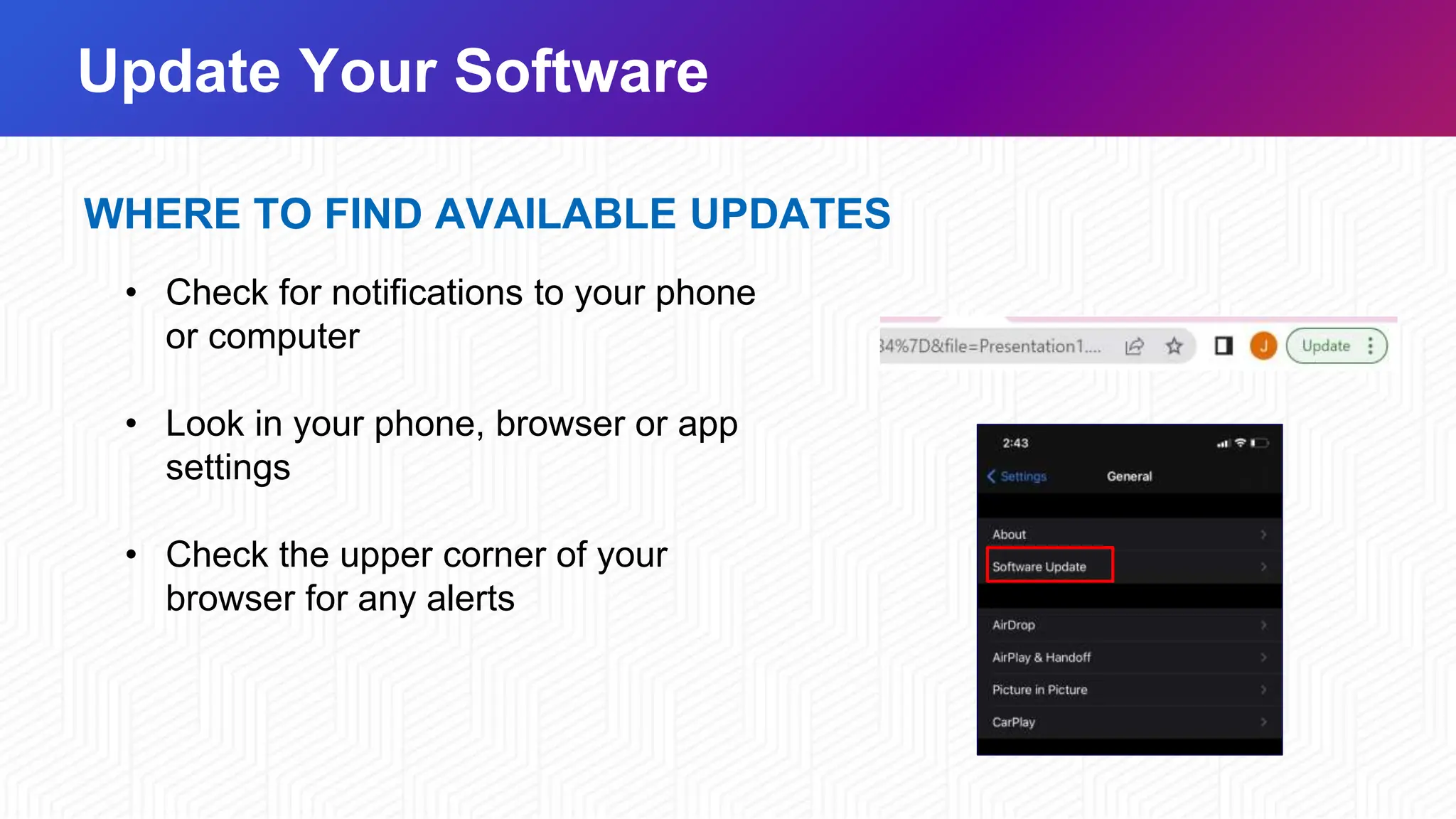
October is Cybersecurity Awareness Month, emphasizing the shared responsibility of protecting against cyber threats through collaboration and awareness. Cybersecurity best practices are crucial for individuals and organizations to safeguard sensitive information, with only a minority of people effectively utilizing tools like unique passwords and multifactor authentication. Strategies for staying safe online include using strong passwords, enabling multifactor authentication, recognizing and reporting phishing attacks, and keeping software updated.