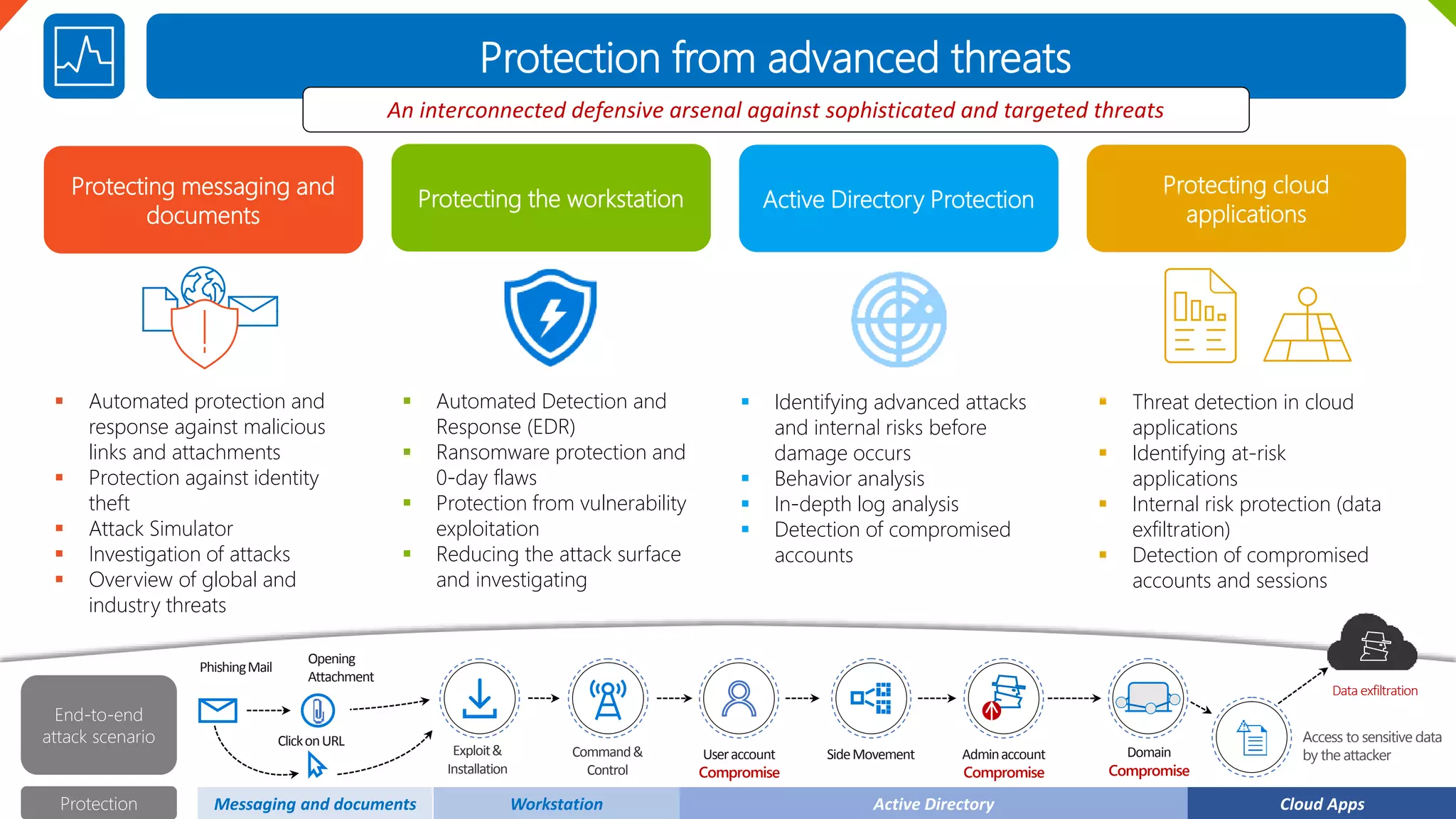
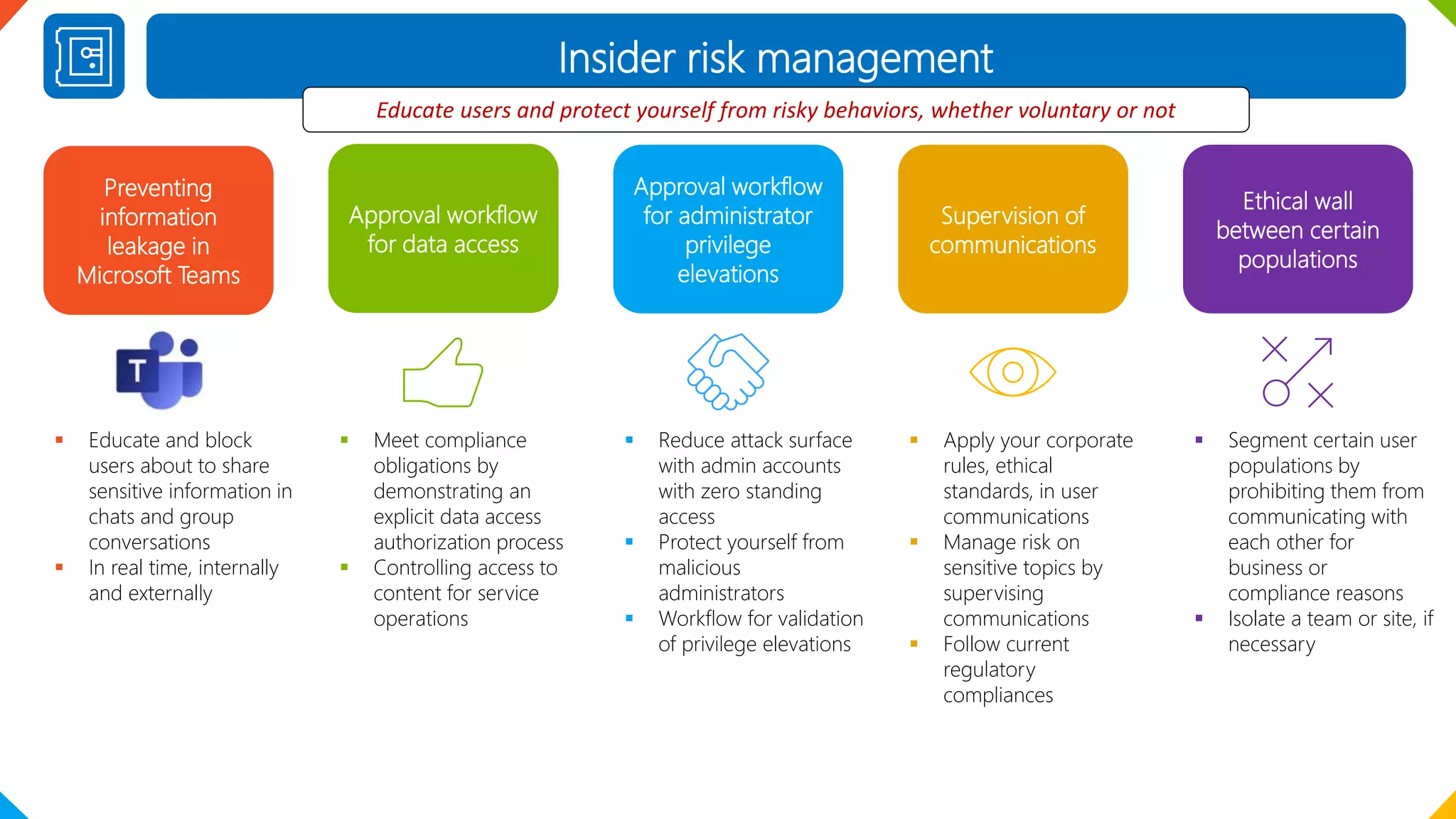
The document outlines the features and benefits of Microsoft 365 E5, focusing on information protection, identity management, advanced threat protection, and data governance. Key functionalities include automated data protection, sophisticated telephony solutions, and comprehensive data oversight to safeguard against risks in cloud applications. It emphasizes tools for managing sensitive data lifecycle, user access, and internal communication compliance.