Embed presentation
Download as PDF, PPTX

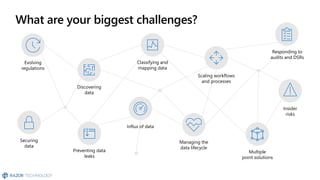



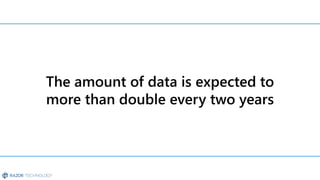
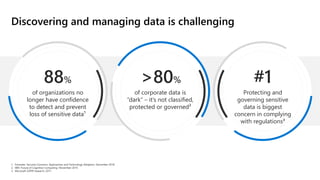
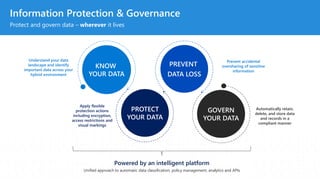

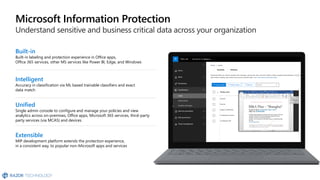
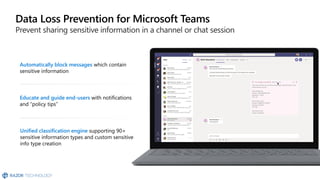
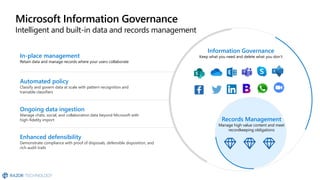
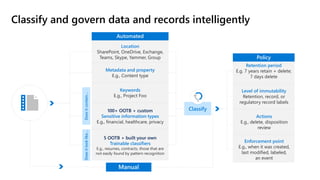




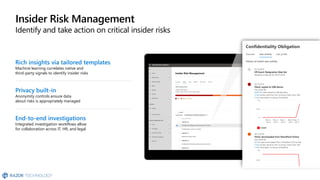

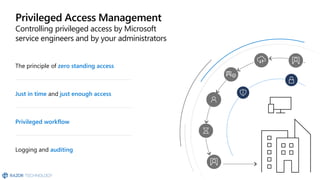
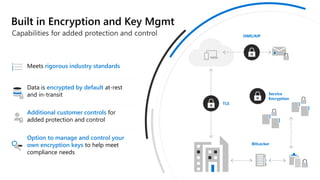

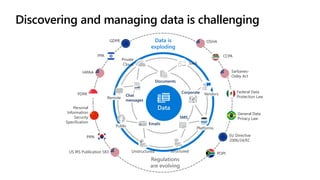

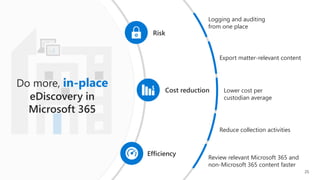
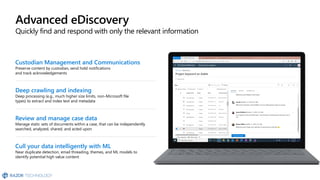
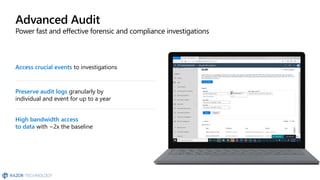


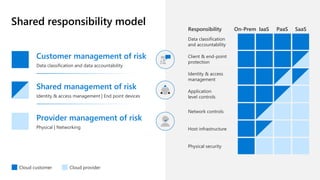









The document discusses the challenges organizations face in compliance and risk management, highlighting the complexities of evolving regulations, data classification, and insider risks. It emphasizes the importance of intelligent solutions that enable organizations to protect, govern, and manage their sensitive data effectively while ensuring compliance with regulations. The Microsoft compliance score and built-in features provide tools and recommendations for organizations to improve their data protection and compliance landscape.





































