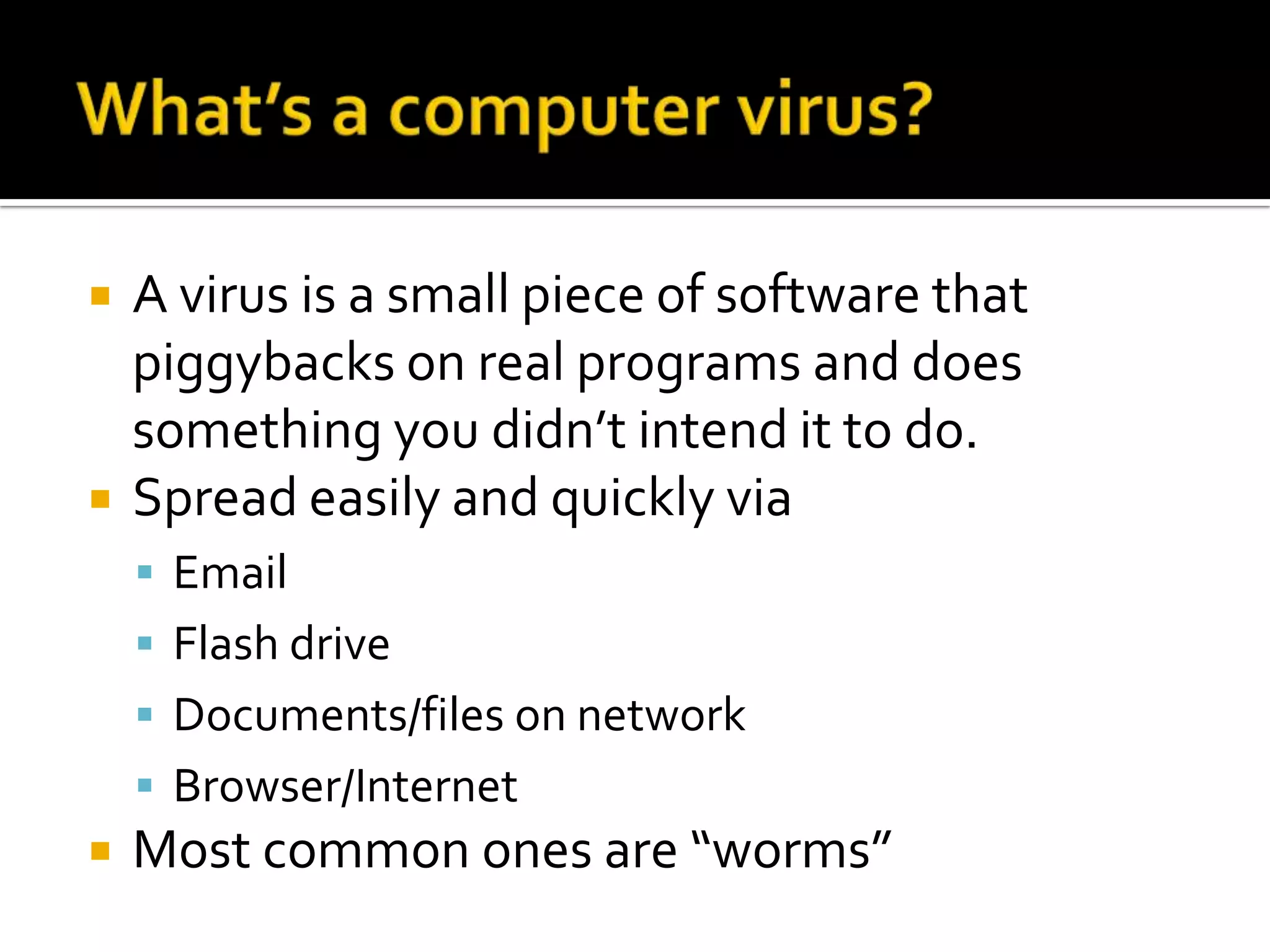
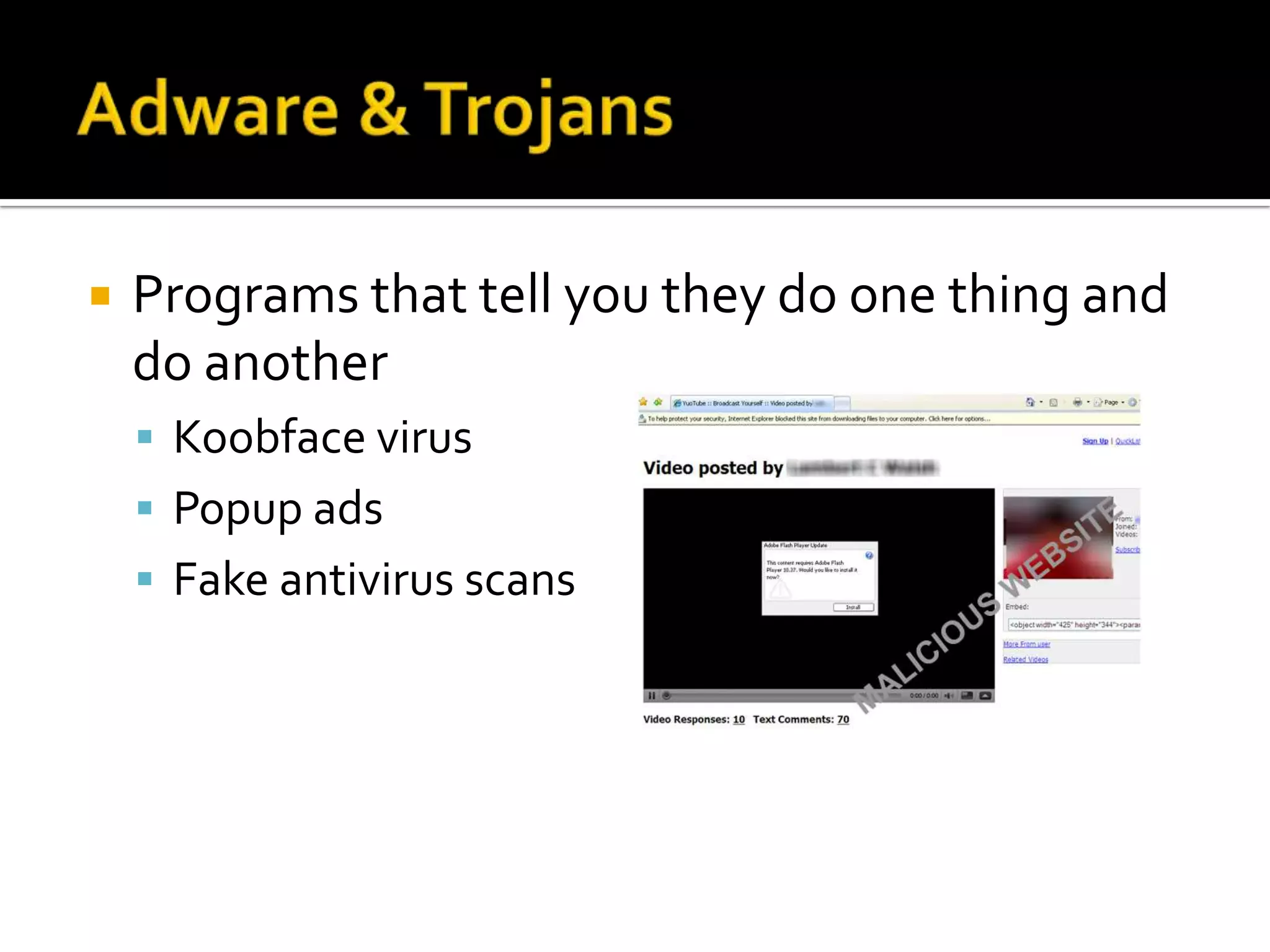
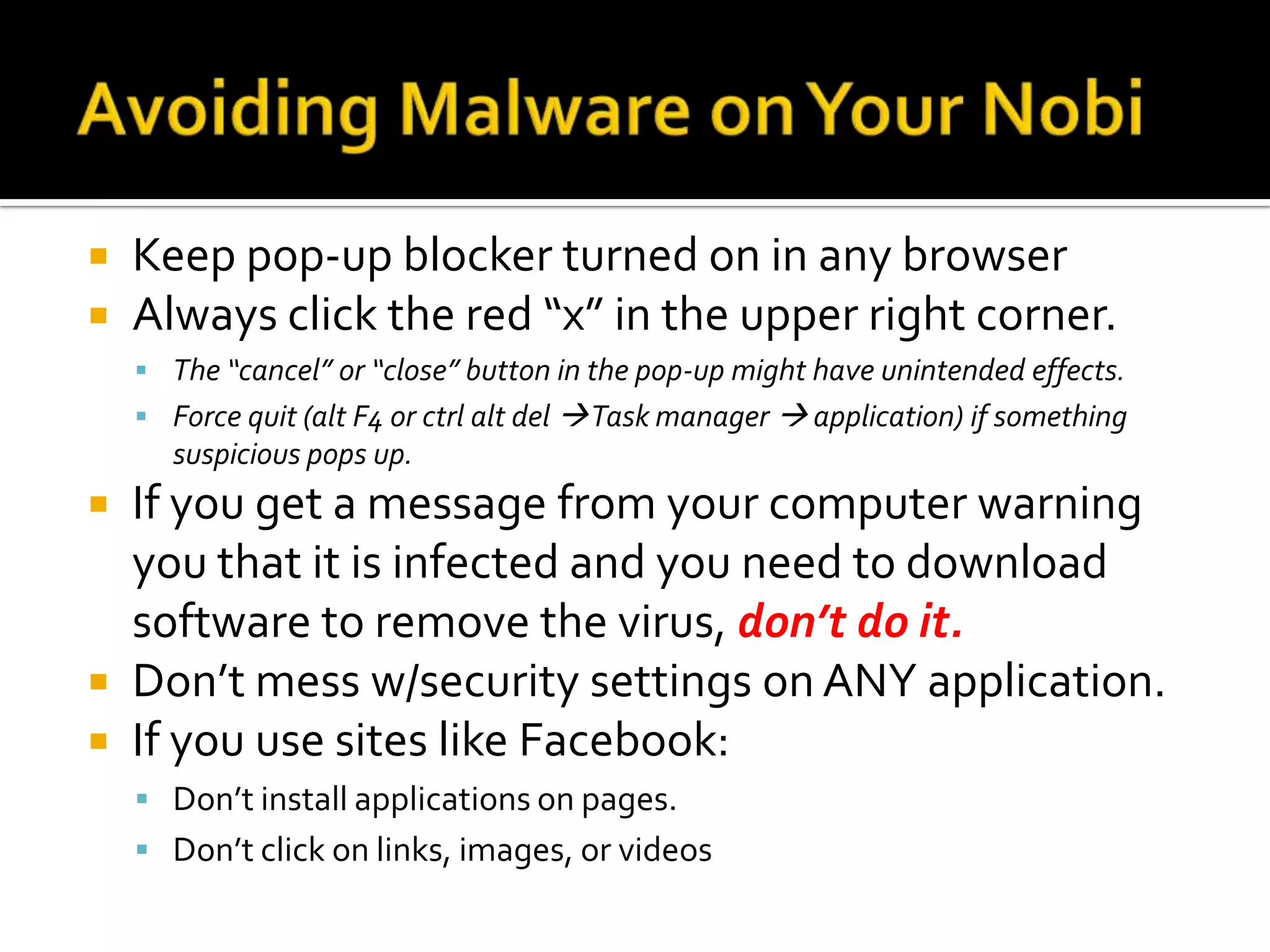
Viruses and spyware can infect computers through email attachments, websites, and removable drives. Viruses spread software without permission and spyware monitors users' activities. Adware displays unwanted pop-up ads through programs that claim to do one thing but do another. Users can avoid malware by practicing common sense online safety like avoiding random website clicks, not installing unknown software, and running regular antivirus scans.