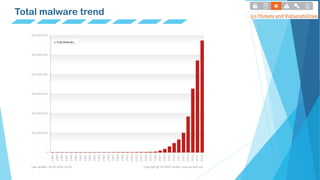
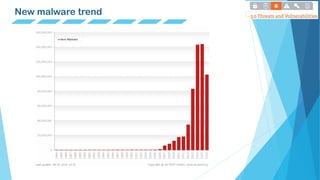
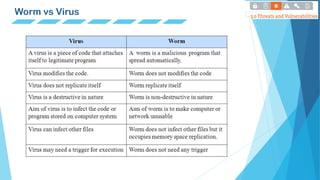
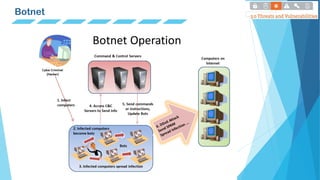
This document defines and describes different types of malware including viruses, worms, spyware, trojans, rootkits, backdoors, botnets, and ransomware. It provides examples of each type and notes key characteristics like how they spread, what damage they can cause, and whether they self-replicate or need user execution. Charts are included showing overall malware trends over time as well as trends in new malware detections.