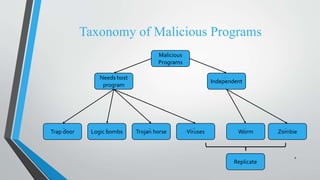
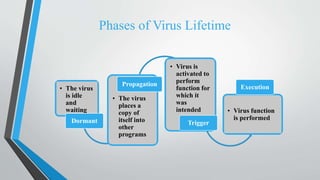
This document defines and describes different types of malicious software programs. It begins by defining a malicious program as a set of instructions that runs on a computer without the user's consent to perform unauthorized actions. It then categorizes malicious programs into those that need a host program and those that are independent. Specific types of malicious programs discussed include trap doors, logic bombs, Trojan horses, zombies, viruses, and worms. For each type, details are provided about how they function, spread, and the harm they can cause systems.