This document proposes a linear programming (LP) based approach for solving maximum a posteriori (MAP) estimation problems on factor graphs that contain multiple-degree non-indicator functions. It presents an existing LP method for problems with single-degree functions, then introduces a transformation to handle multiple-degree functions by introducing auxiliary variables. This allows applying the existing LP method. As an example, it applies this to maximum likelihood decoding for the Gaussian multiple access channel. Simulation results demonstrate the LP approach decodes correctly with polynomial complexity.


![Motivation
Problem: MAP estimation problems on graphical models
Ex: MAP (ML) decoding problem of binary linear codes
Linear Programming based decoding algorithm is attracting.
[Feldman et al. 2005]
Extension of LP decoding to other problems
decoding for q-ary linear codes [Flanagan et al. 2008]
application to Partial-Response (PR) channel [Taghavi et al. 2007]
MAP estimation problems on factor graphs which don’t have
multiple-degree non-indicator functions [Flanagan 2010]
Our research
.
LP based inference algorithm for MAP estimation problems on factor
graphs which have multiple-degree non-indicator functions
include decoding problems of linear codes over multiple-access
channels
3 / 23](https://image.slidesharecdn.com/ma112011id5352213-120418043253-phpapp01/75/ma112011id535-3-2048.jpg)


![Factor graph
Factor graph [F. R. Kschischang et al. 2001]
A bipartite graph which expresses the structure of a factorization of a
product of functions
variable nodes: represent the variables {xn }n=1,2,··· ,N
factor nodes: represent the functions {fa }a∈A
.
edge-connections: variable node xn and factor node fa is connected
iff xn is an argument of fa
Example: g(x , x , x , x ) = f (x , x )f (x , x , x )f (x , x )
1 2 3 4 A 1 2 B 2 3 4 C 2 4
.
6 / 23](https://image.slidesharecdn.com/ma112011id5352213-120418043253-phpapp01/75/ma112011id535-6-2048.jpg)



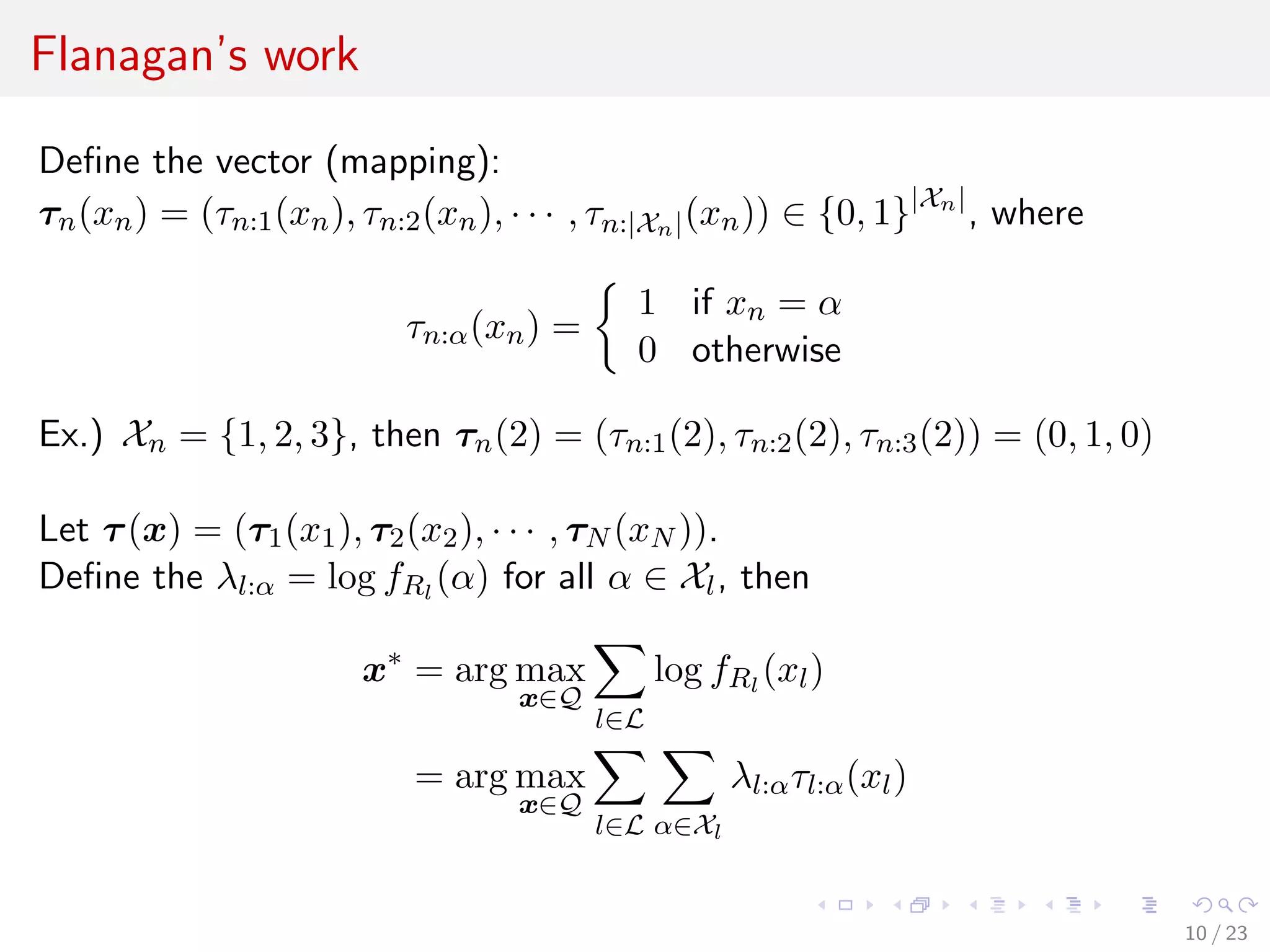
![Flanagan’s work
{ }
Define the polytope Pj = τ (x) : fIj (xIj = 1) and
(∩ )
P = conv j∈J Pj (conv(·): convex hull of a set), then
∑∑ ∑∑
max λl:α τl:α (xl ) = max λl:α τl:α
x∈Q τ ∈P
l∈L α∈Xl l∈L α∈Xl
where τ is the variable that takes its value in the range of τ (x) and τl:α is
an element of τ .
LP relaxed problem is derived as follows:
∑∑
max λl:α τl:α
τ ∈P
˜
l∈L α∈Xl
˜ ∩
where P = j∈J conv(Pj ). is the relaxed polytope.
See [Flanagan, 2010] for detail.
11 / 23](https://image.slidesharecdn.com/ma112011id5352213-120418043253-phpapp01/75/ma112011id535-11-2048.jpg)