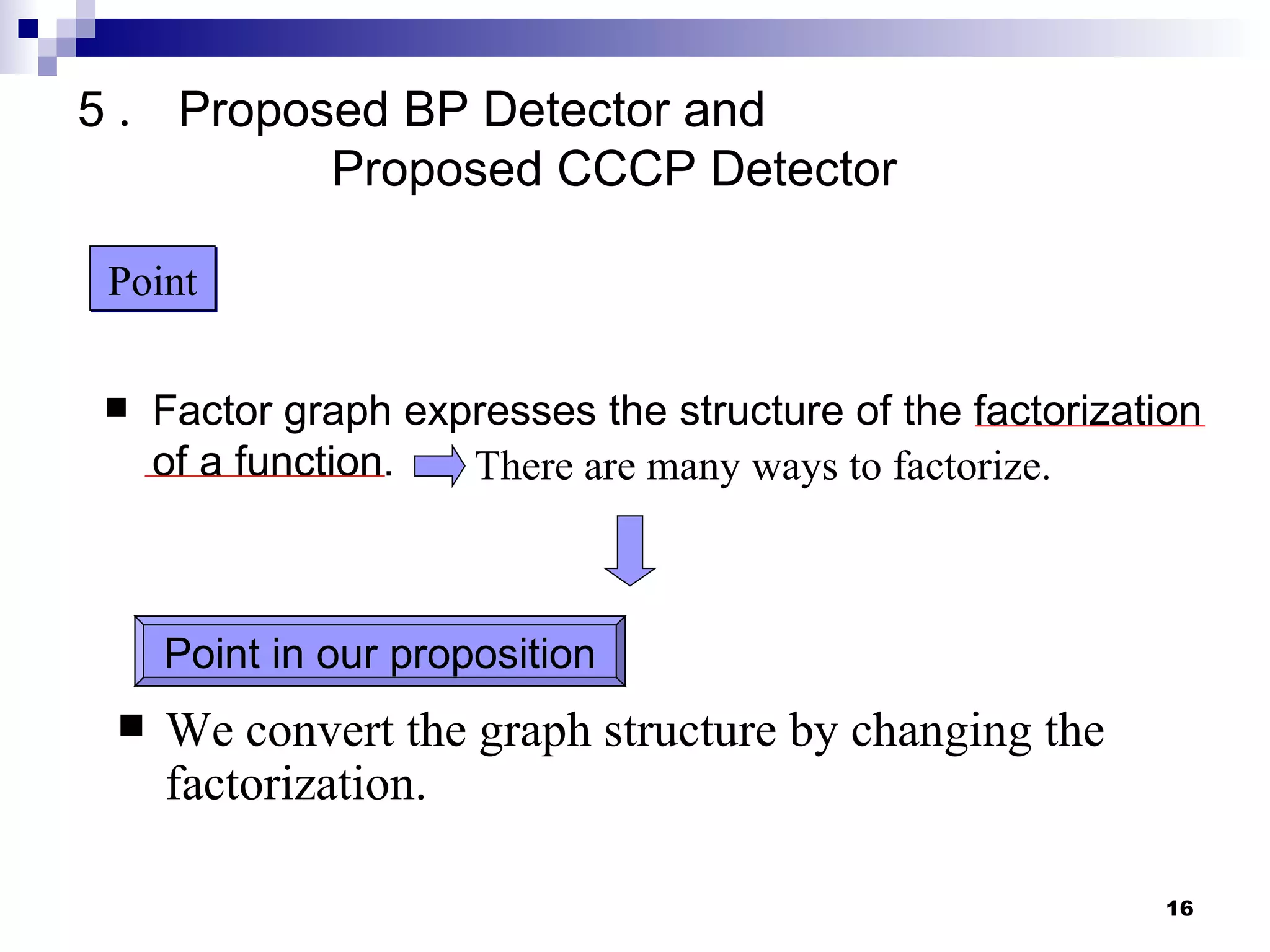
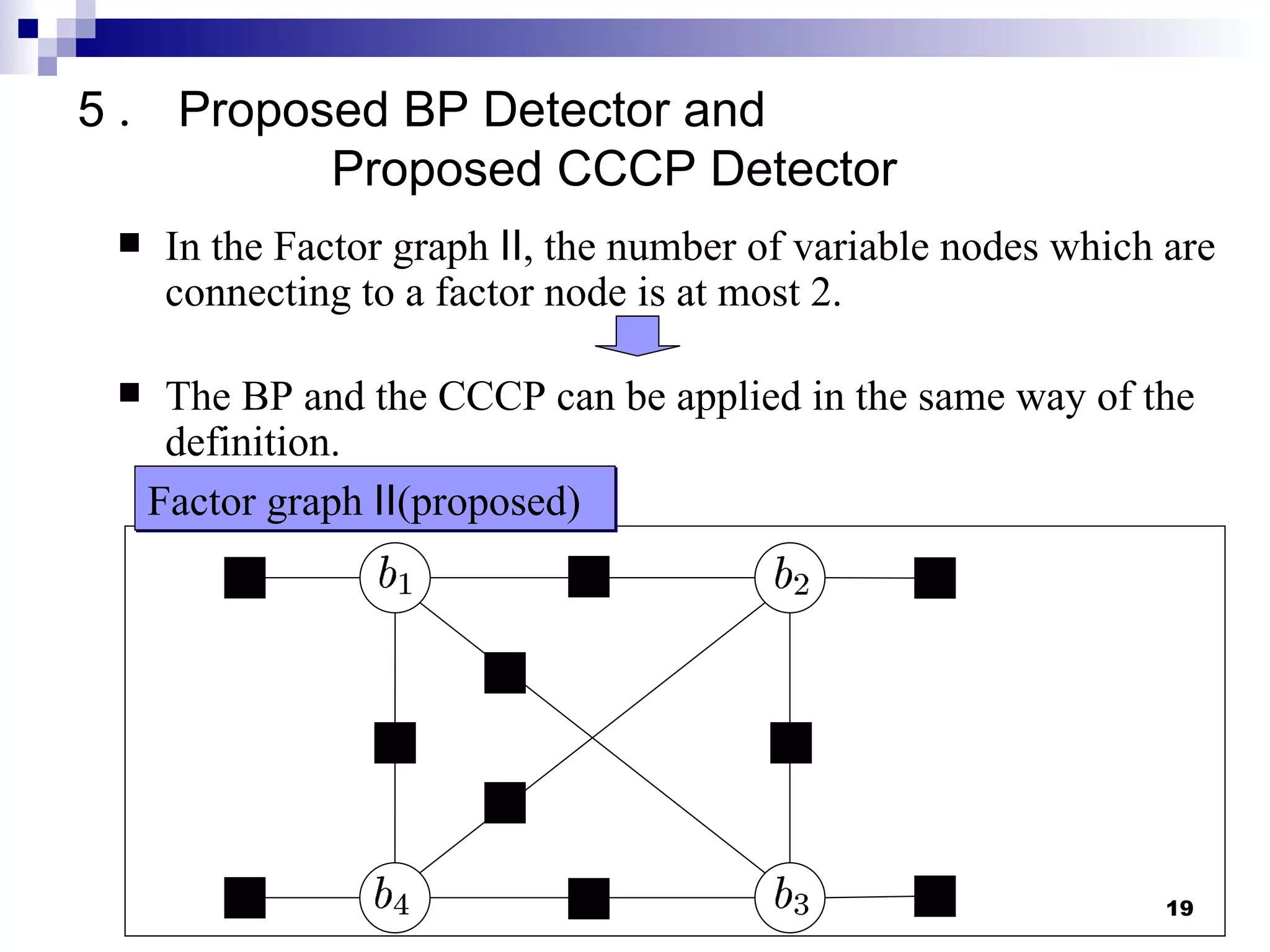
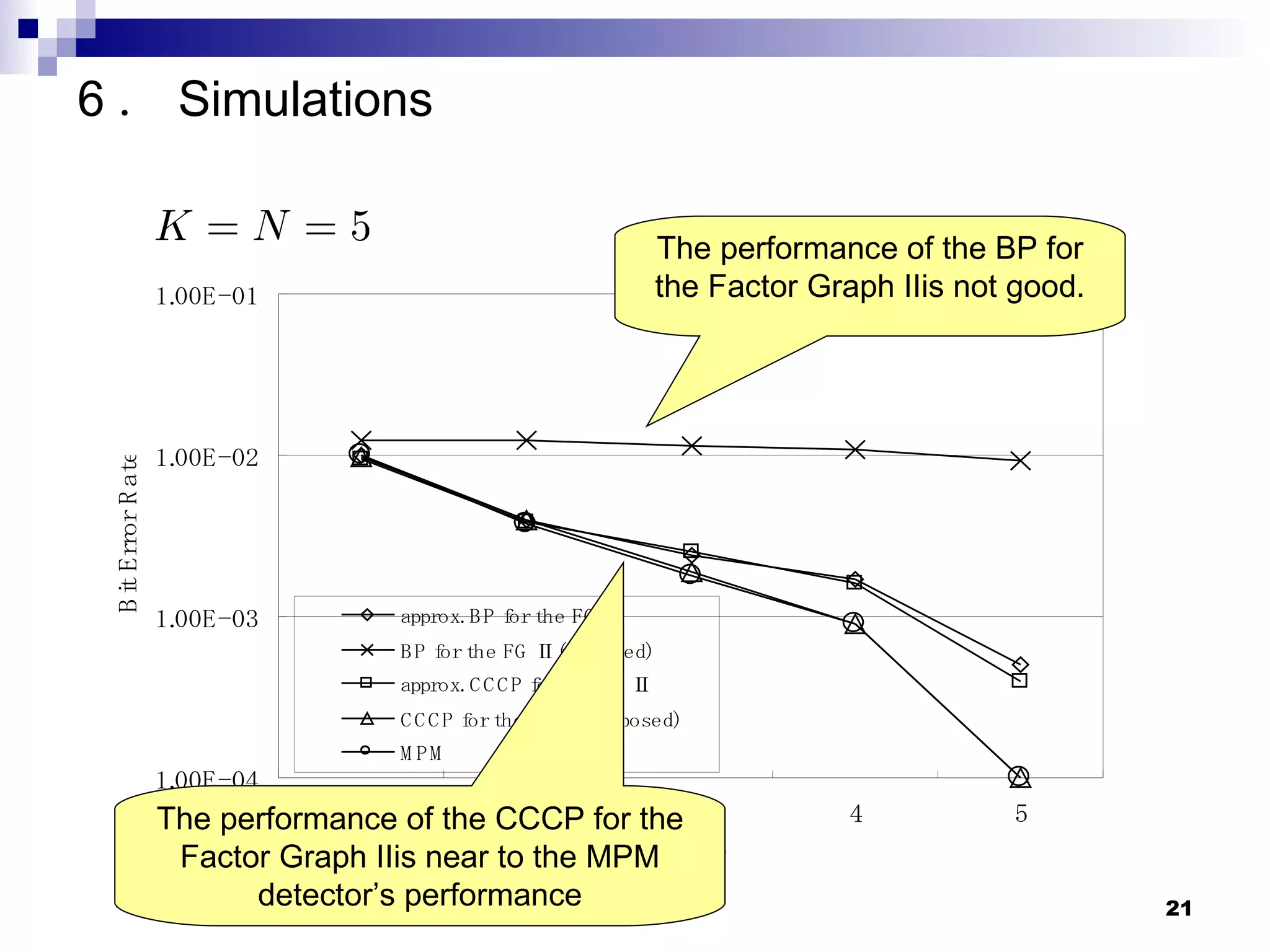
The document proposes reducing the computational complexity of message passing algorithms like belief propagation (BP) and concave-convex procedure (CCCP) for multiuser detection in CDMA systems. It does this by changing the factor graph structure used to represent the detection problem from a fully connected graph (Factor Graph I) to a sparsely connected graph (Factor Graph II). Simulation results show the proposed CCCP detector for the new factor graph achieves near optimal performance with lower complexity than existing approaches.

![Optimal detector for CDMA The MPM detector is optimal with respect to the Bit Error Rate. But the computational complexity of the MPM detector increases exponentially with the number of users. -> There are many researches about alternative detectors. 1. Introduction detection problem can be regarded as a probabilistic inference problem Message passing algorithms defined in terms of operations on a graph compute marginal probability function efficiently Recently, detectors based on the message passing algorithms were developed. But it have been reported that the computational complexity of the message passing algorithms for the detection problem also increases exponentially with the number of users. [Kabashima, 2003] [Tonosaki et al., 2004]](https://image.slidesharecdn.com/ma112006id3373361/75/ma112006id337-3-2048.jpg)



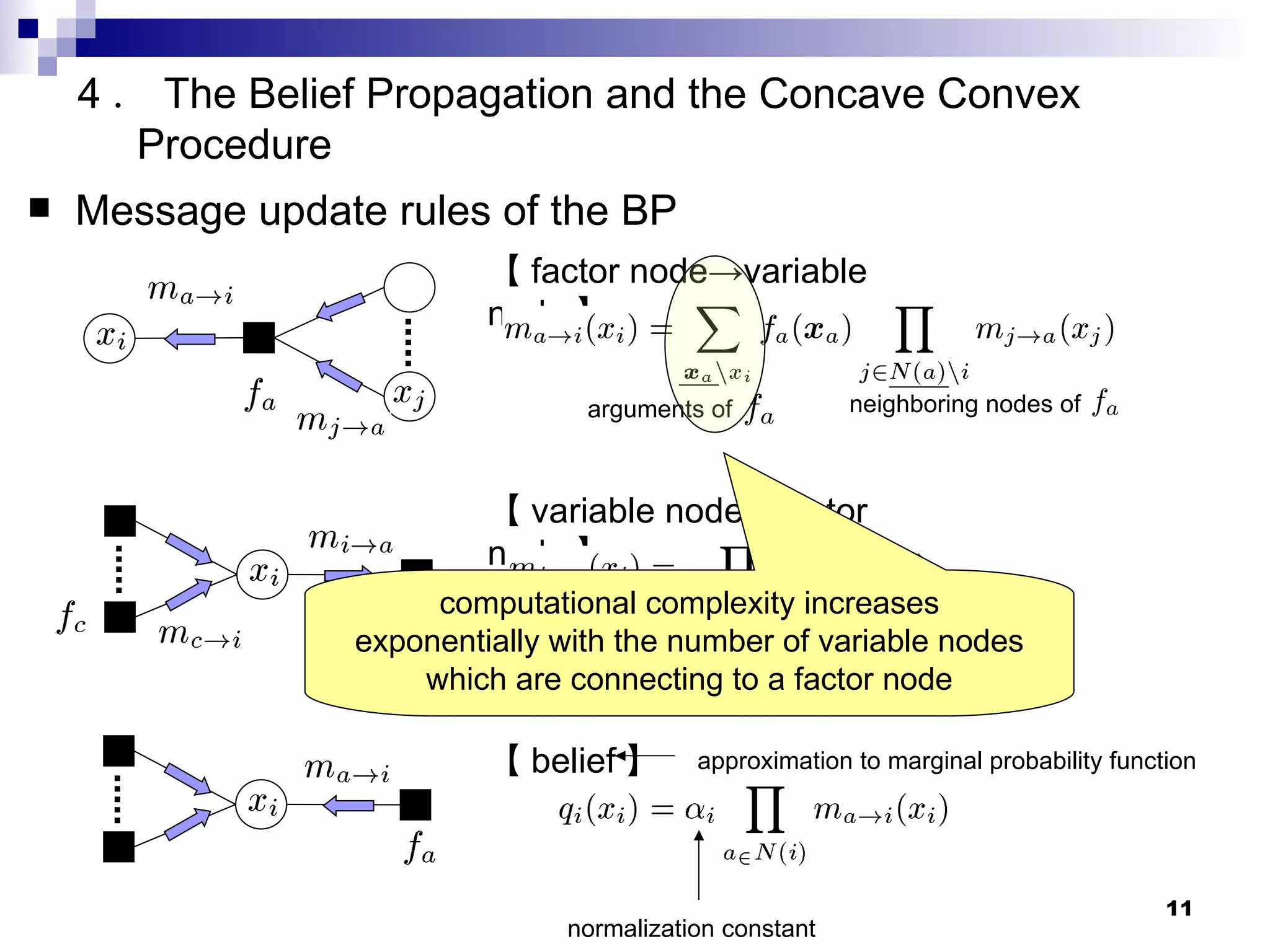
![【 Factor Graph (FG) 】 A bipartite graph which expresses the structure of a factorization of a joint distribution. The BP and the CCCP can be defined in terms of operations on a factor graph. 4 . The Belief Propagation and the Concave Convex Procedure Ex. [Kschischang et al. 01]](https://image.slidesharecdn.com/ma112006id3373361/75/ma112006id337-9-2048.jpg)
![The BP and the CCCP When the factor graph has many cycles, the BP and the CCCP both compute an approximation to a marginal probability function of each variable. the BP does not always converge , while the CCCP is stable and probably convergent even when the BP does not converge . If the algorithms converge, the fixed point of the BP correspond to that of the CCCP. 4 . The Belief Propagation and the Concave Convex Procedure [Yedidia et al. 2005] [Yuille, 2002 ]](https://image.slidesharecdn.com/ma112006id3373361/75/ma112006id337-10-2048.jpg)

![In the past researches, the BP and the CCCP are already applied for the detection problem. 5 . Approximate BP Detector and Approximate CCCP Detector Factor graph Ⅰ [Kabashima, 2003] [Tonosaki et al., 2004]](https://image.slidesharecdn.com/ma112006id3373361/75/ma112006id337-13-2048.jpg)








![7 . Discussions Relations between the graph structure and the performances of the detectors. The BP is not appropriate for the factor graph Ⅱ when the absolute values of the cross correlations are large. Reason It seems to me that the fact that “the strengths of functions are strong, the BP tends to not converge” is one of reasons. Ref.[Welling and Teh, 2001] ※](https://image.slidesharecdn.com/ma112006id3373361/75/ma112006id337-26-2048.jpg)



