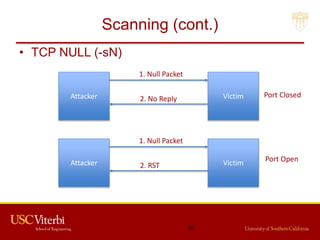
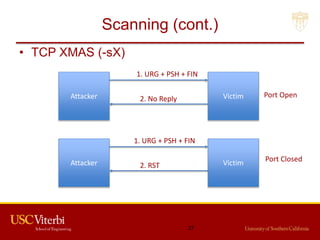
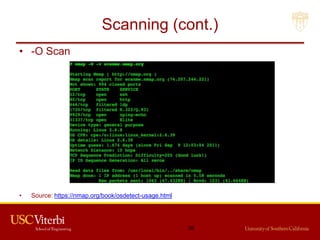
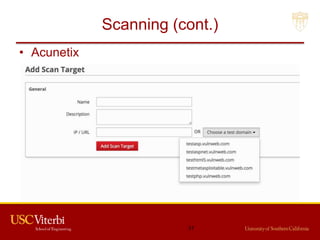
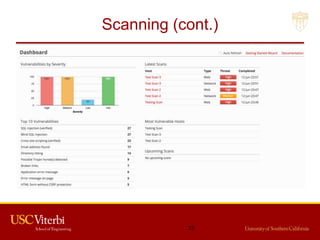
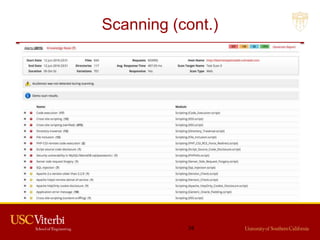
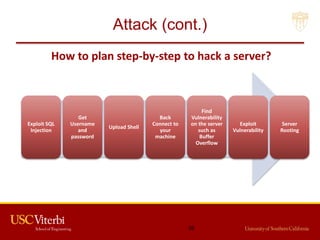
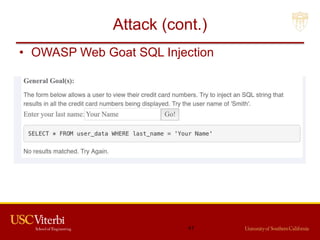
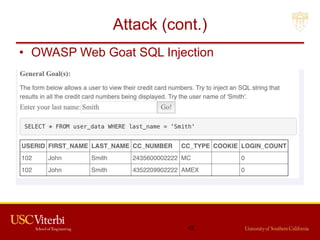
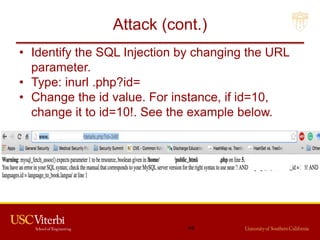
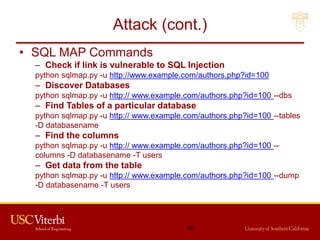
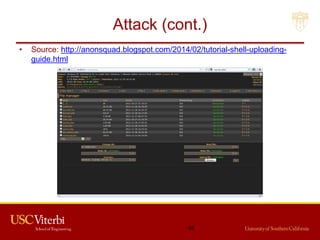
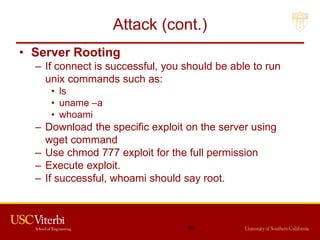
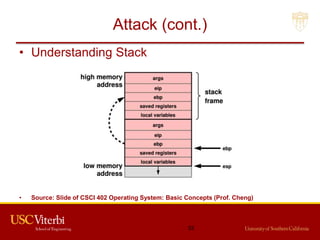
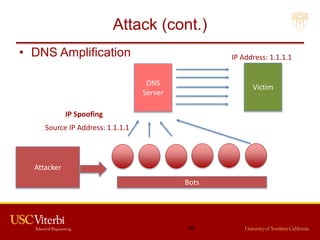
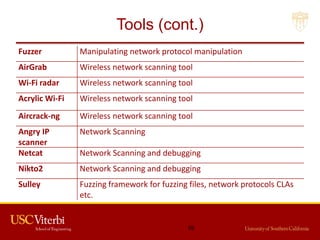
The document outlines a lecture on secure systems administration, focusing on topics such as ethical hacking, penetration testing tools, and methodologies. It discusses the stages of ethical hacking including information gathering, scanning, exploiting vulnerabilities, and maintaining access, while emphasizing best practices and ethical considerations in cybersecurity. Additionally, it includes specific tools and techniques used in penetration testing and a case study on the Ukraine power grid attack.















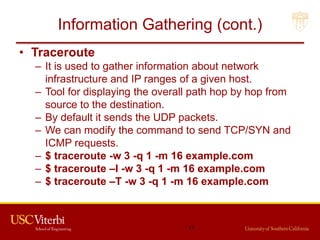
![Information Gathering (cont.)
• DNS Information Gathering
– dnsenum: Tool in the backtrack Kali OS. It starts
querying DNS servers and gather information:
• Host address
• Name servers
• MX records
• Gathering SOA records
• Command: perl dnsnum.pl [host]
– dnsrecon: to gather network infrastructure
information.
– Dig: DNS information groper
• dig example.com MX @ns0.example.com
15](https://image.slidesharecdn.com/sp17-inf526-lec6-190423154745/85/Hacking-penetration-tools-16-320.jpg)