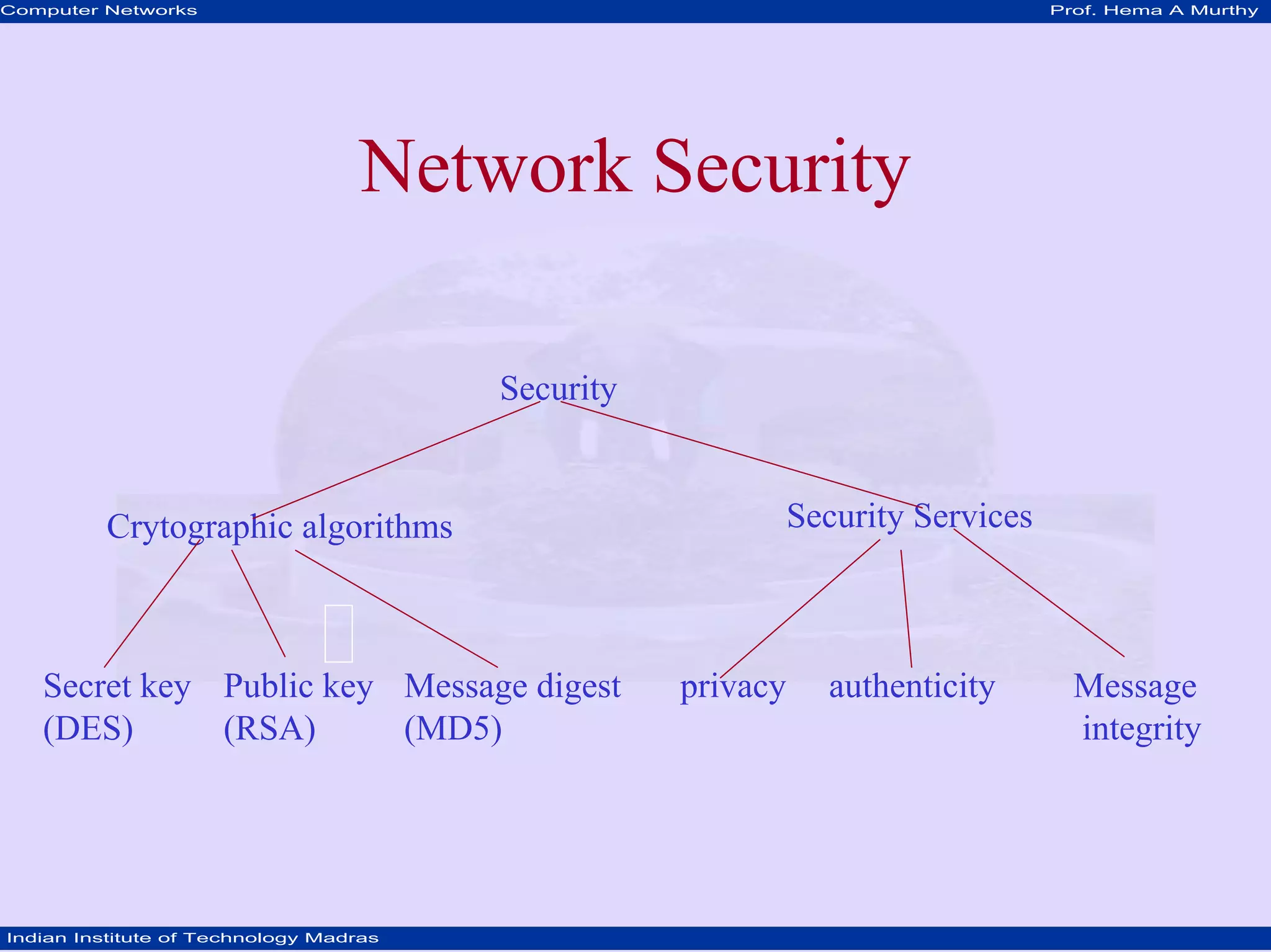
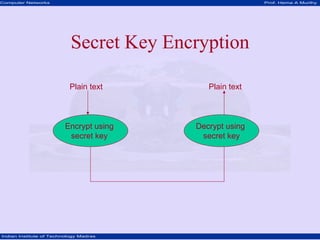
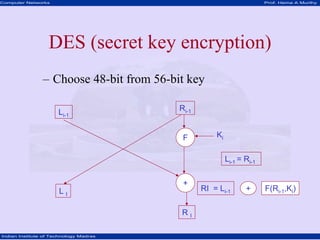
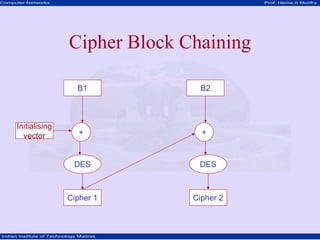
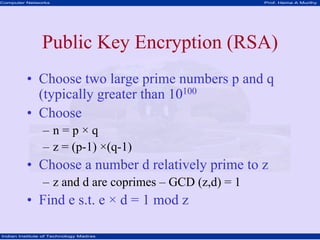
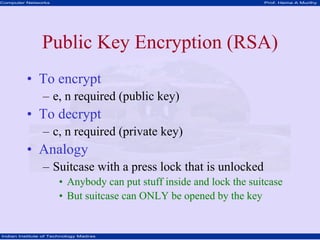
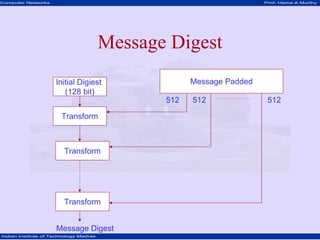
This document discusses network security concepts like cryptographic algorithms, secret key encryption, public key encryption, and message digest encryption. It provides details on DES secret key encryption including its use of a 64-bit block cipher and 16 rounds of encryption. It also explains the RSA public key encryption process of using prime numbers and modular exponentiation. Finally, it gives a high-level overview of how message digest encryption works by mapping messages into fixed-length numbers.