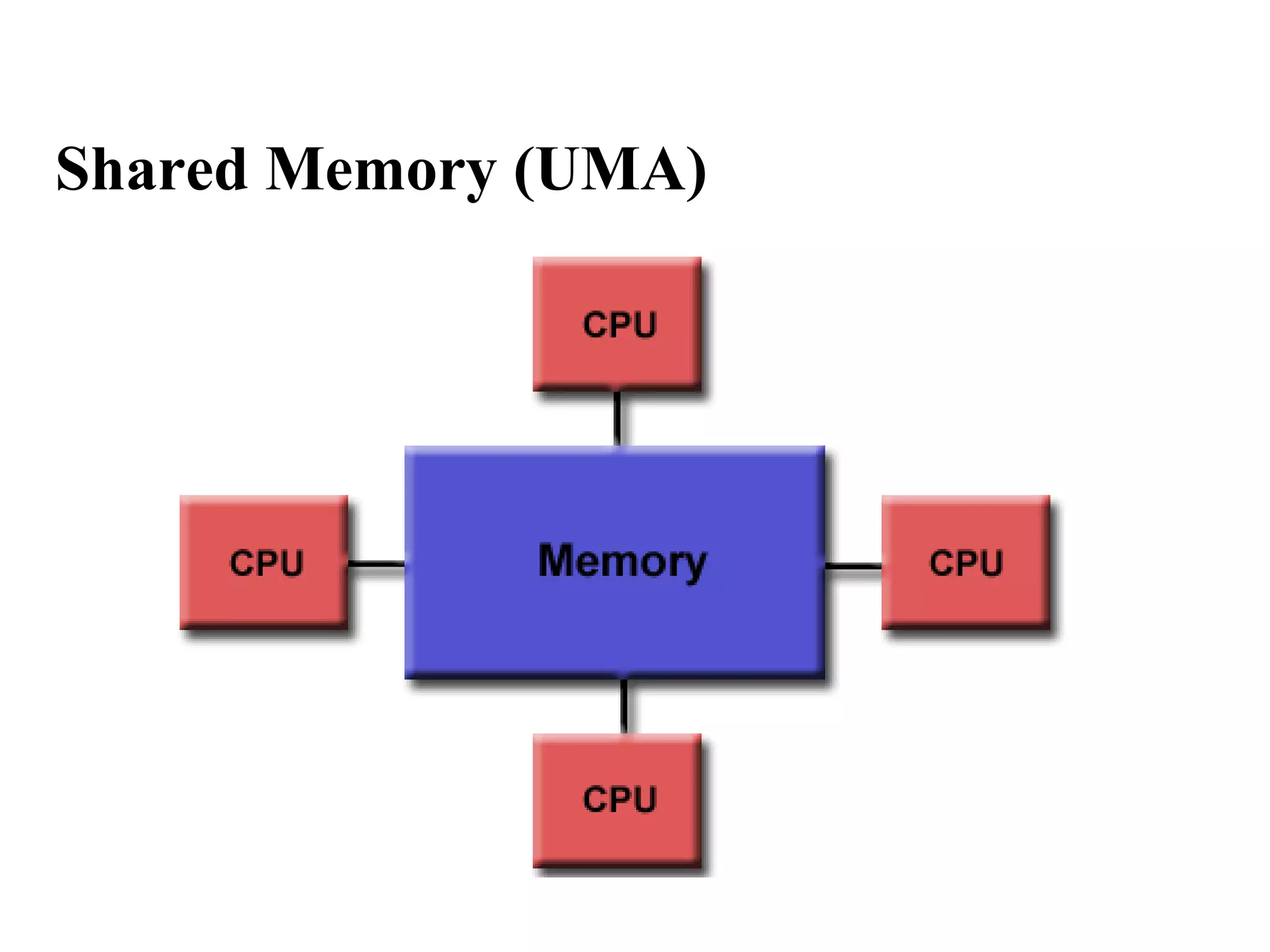
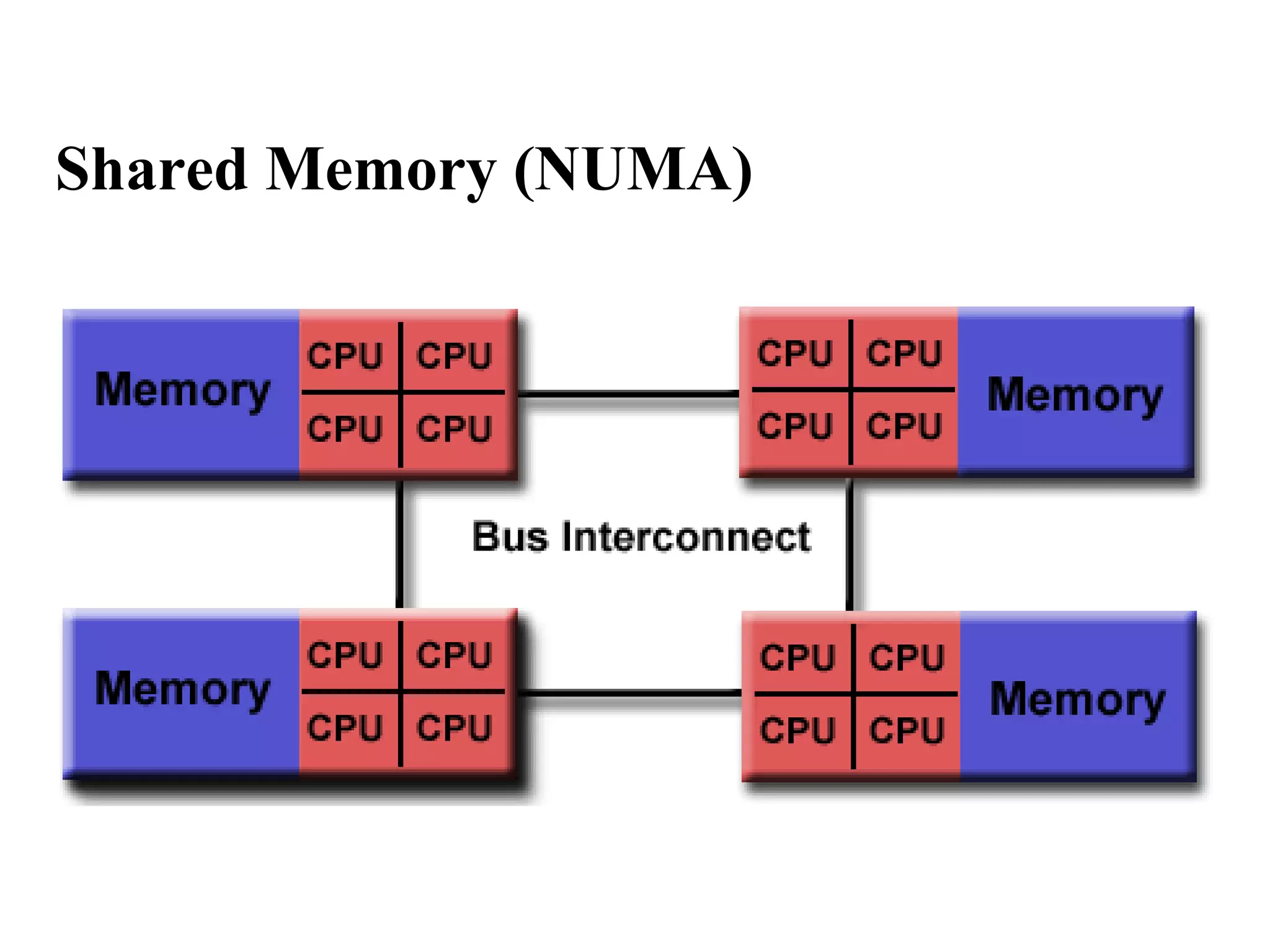
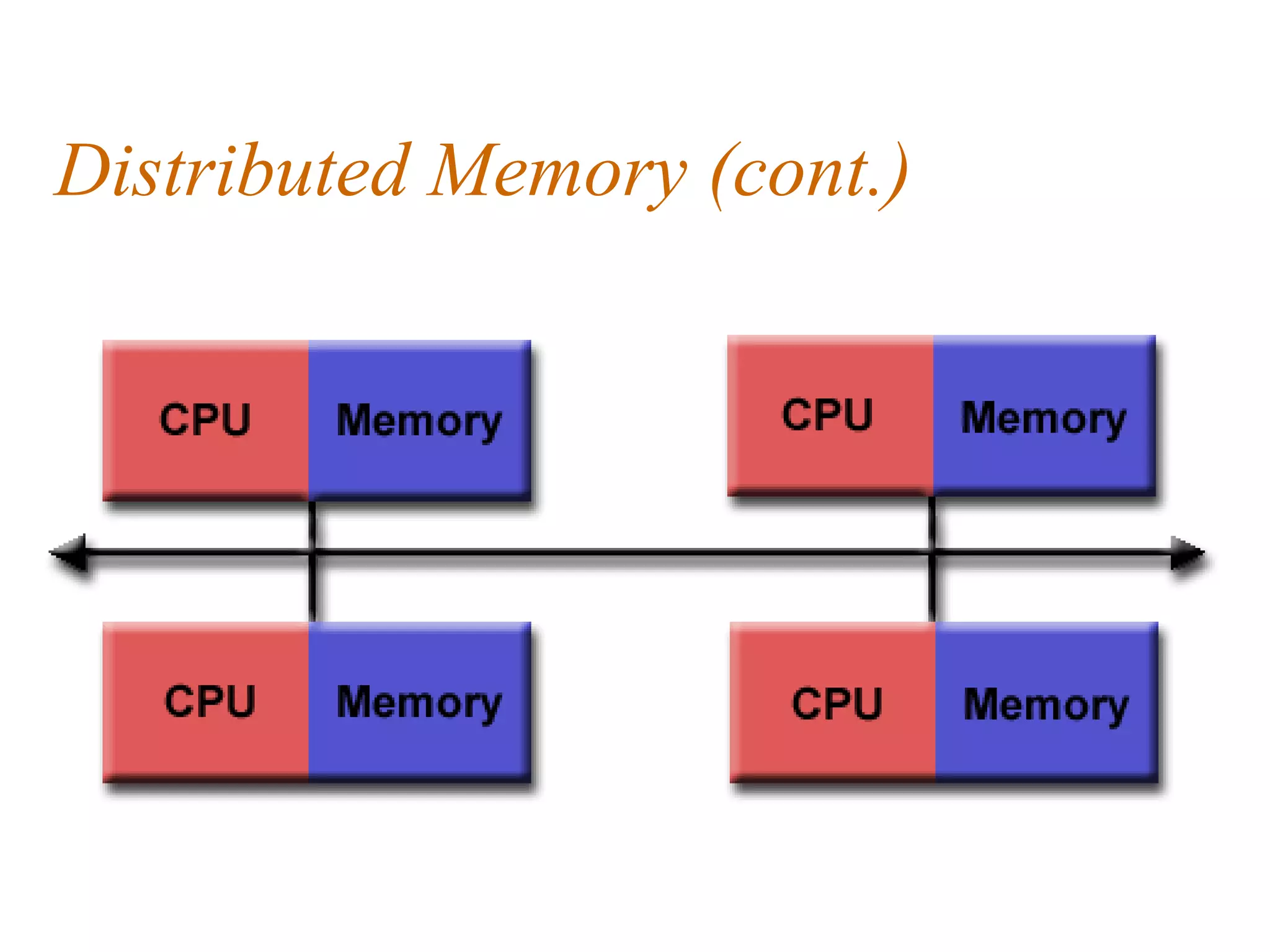
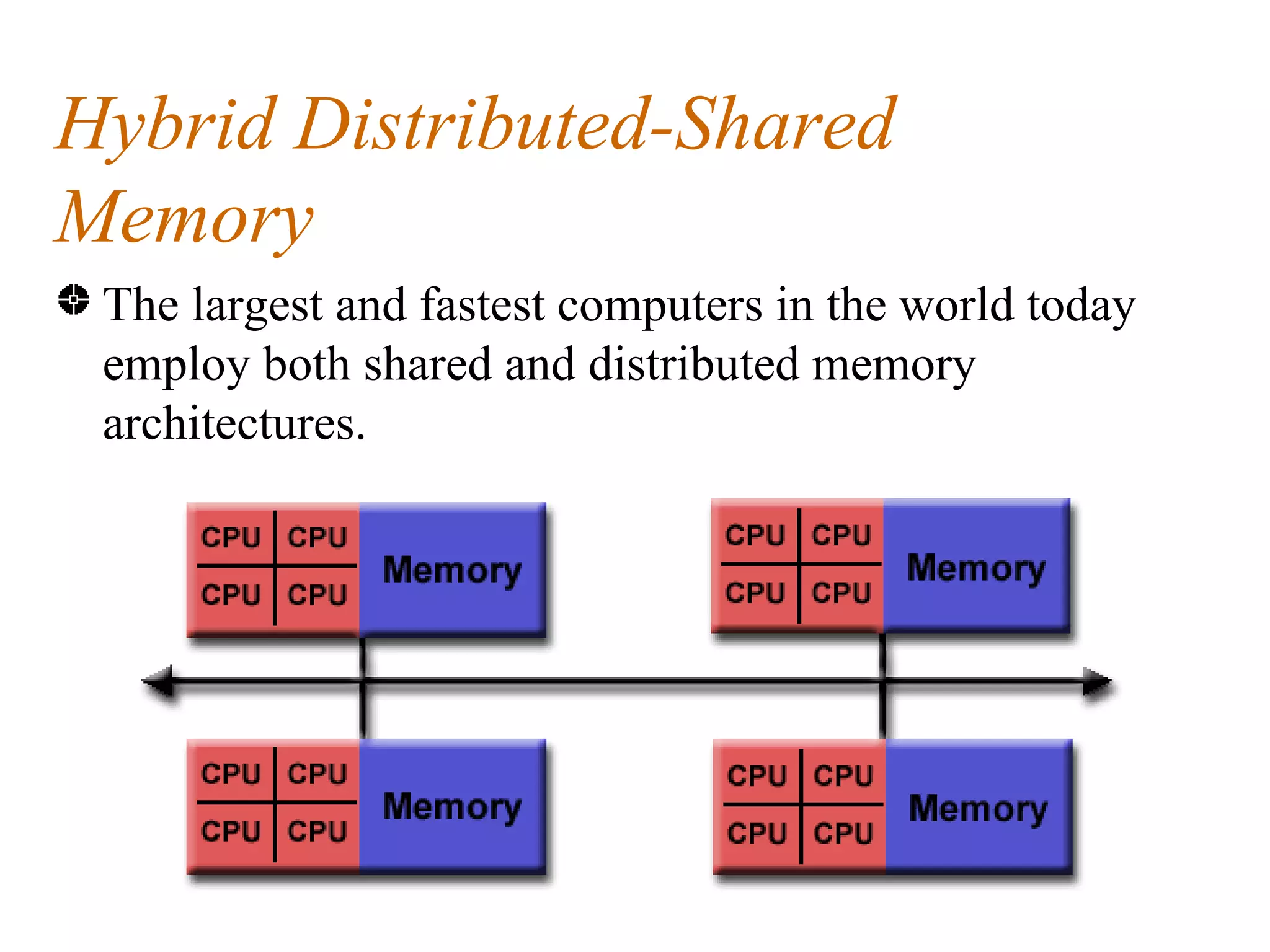
This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space and include uniform memory access (UMA) and non-uniform memory access (NUMA). Distributed memory architectures require a communication network since each processor has its own local memory without a global address space. Hybrid architectures combine shared and distributed memory by networking multiple shared memory multiprocessors.