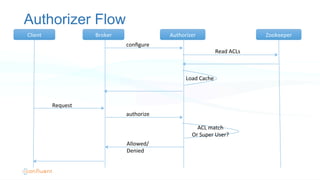
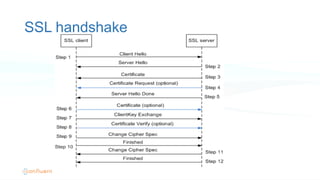
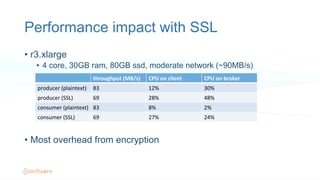
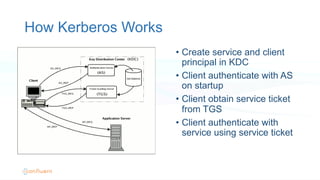
The document outlines the security architecture of Apache Kafka, detailing various authentication and authorization methods, including SSL and SASL for secure communications between clients and brokers. It explains the setup process for both SSL and Kerberos authentication, emphasizing the need for proper configuration to secure Kafka and Zookeeper. Future improvements and options for SASL are mentioned, along with guidance for migrating from non-secure to secure Kafka environments.
















![Kerberos principal name
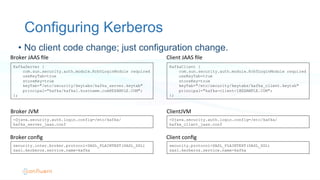
• Kerberos principal
• Primary[/Instance]@REALM
• kafka/kafka1.hostname.com@EXAMPLE.COM
• kafka-client-1@EXAMPLE.COM
• Primary extracted as the default principal name
• Can customize principal name through
sasl.kerberos.principal.to.local.rules](https://image.slidesharecdn.com/kafkasecuritykafkasummit20160426-160509215205/85/Securing-Kafka-21-320.jpg)