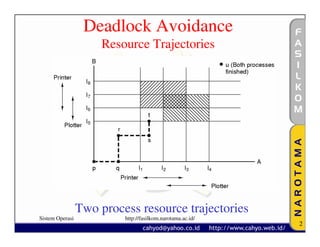
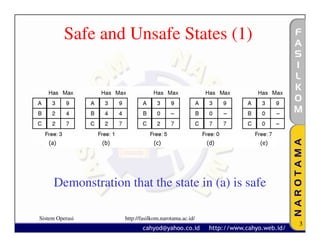
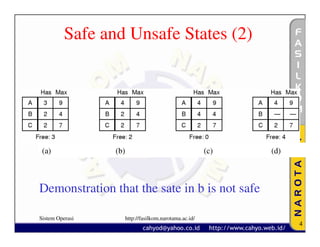
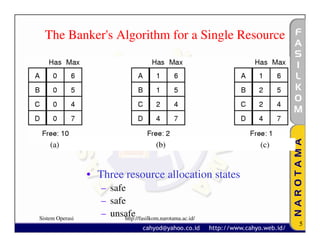
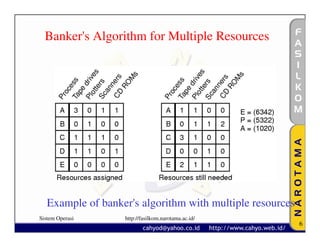
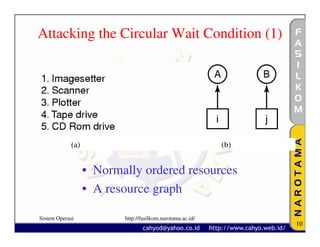
The document discusses various techniques for handling deadlocks, including deadlock avoidance, prevention, and other issues. It describes methods like deadlock avoidance using safe resource trajectories, the banker's algorithm for handling multiple resources, and preventing deadlocks by attacking the different conditions that can cause deadlocks, such as the mutual exclusion or circular wait conditions. It also addresses non-resource deadlocks, starvation issues, and two-phase locking approaches.