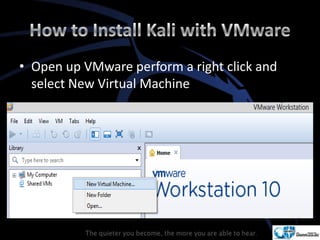
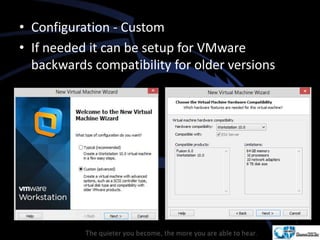
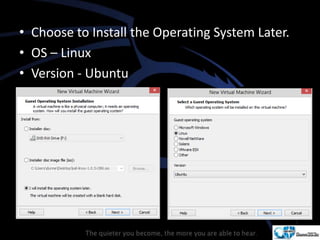
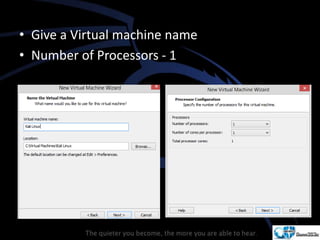
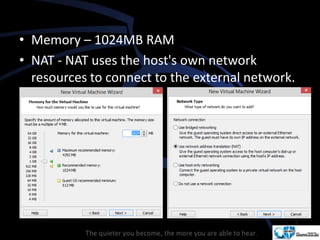
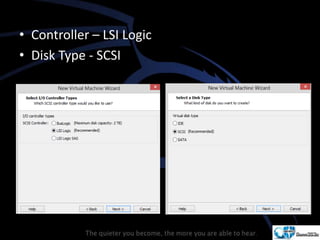
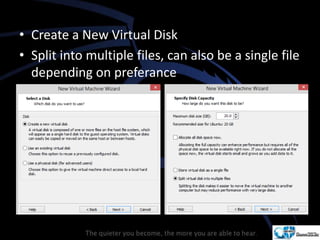
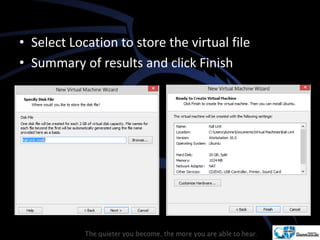
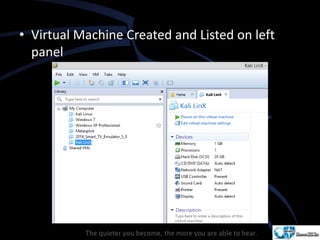
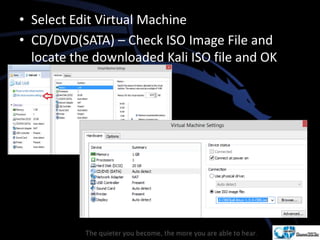
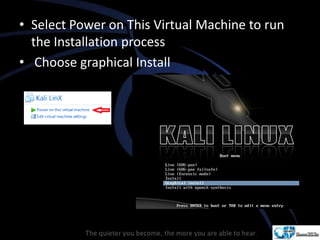
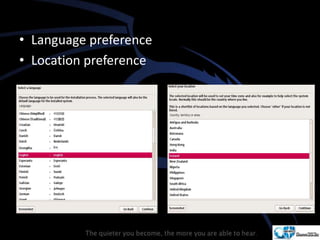
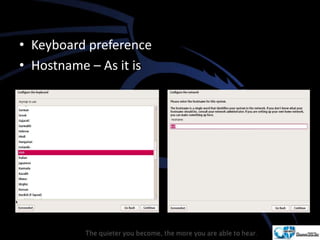
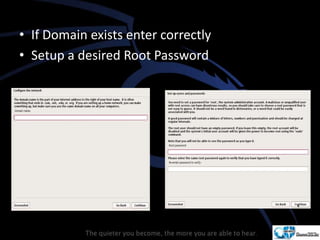
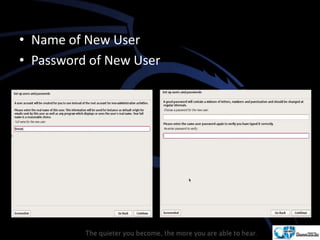
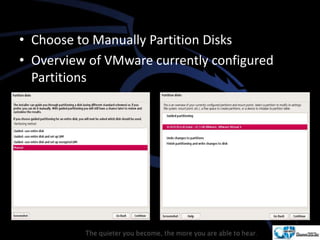
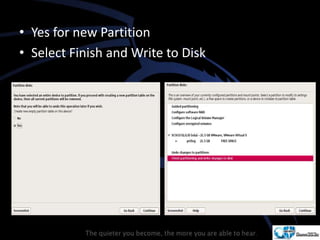
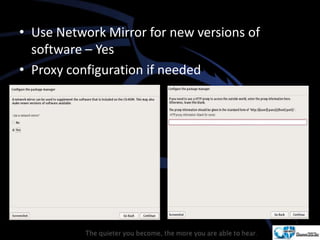
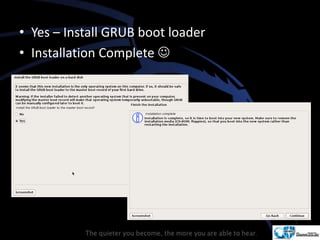
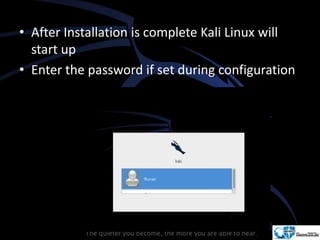
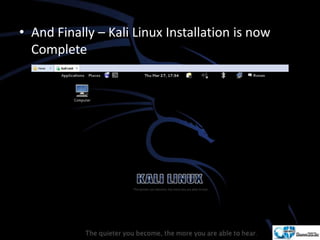
Kali Linux is a pentesting and security auditing Linux distribution preinstalled with various tools. It details the steps to configure and install Kali Linux on VMware, including creating a new virtual machine and setting up the operating system. The installation process involves setting user preferences, partitioning disks, and configuring network settings.