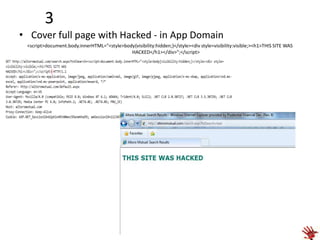
Website defacement involves changing the visual appearance of a website or webpage by exploiting a vulnerability. The document discusses testing website defacement by capturing requests using ZAP proxy and replacing content with malicious code to bypass client-side protections. It then provides examples of defacement techniques like redirecting to hacked images, adding hacked images, covering the page with hacked text, and changing the background. Finally, it recommends server-side input filtering, output escaping, and enforcing a character encoding to prevent defacement attacks.