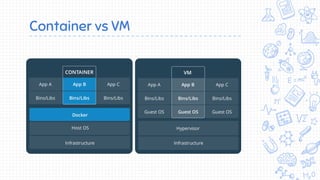
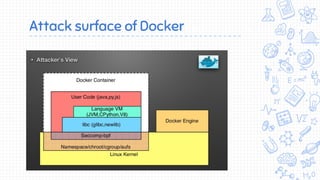
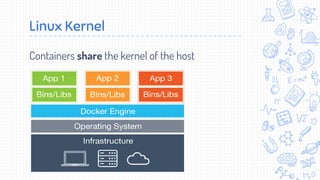
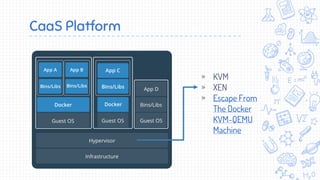
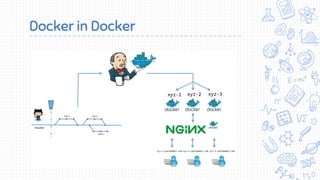
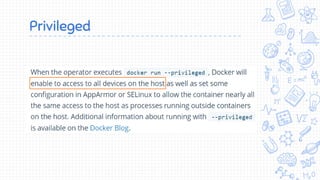
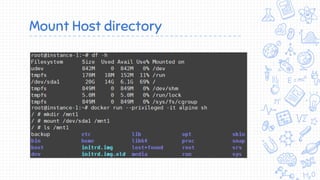
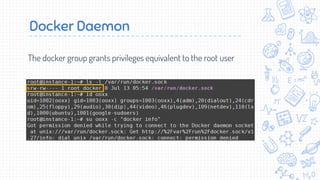
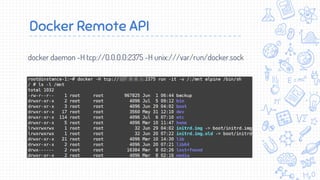
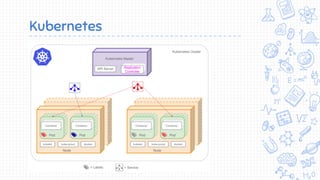
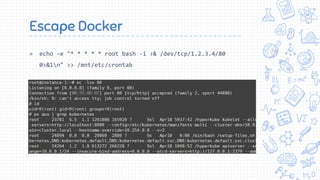
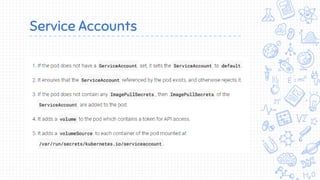
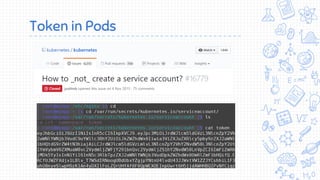
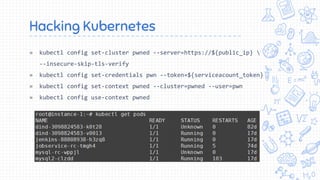
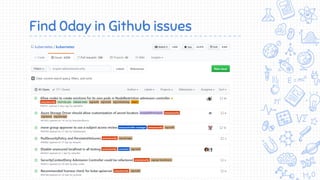
Docker is a popular container platform that provides namespaces, cgroups, capabilities and seccomp to isolate containers. However, it still faces security risks from vulnerabilities in container images, the Linux kernel it relies on, and misconfigurations of the Docker daemon or container management platforms like Kubernetes. Attackers can exploit these issues to escape containers, gain privileges on the host, or access container content without authorization. Careful auditing of Docker and container configurations is needed to prevent security breaches.