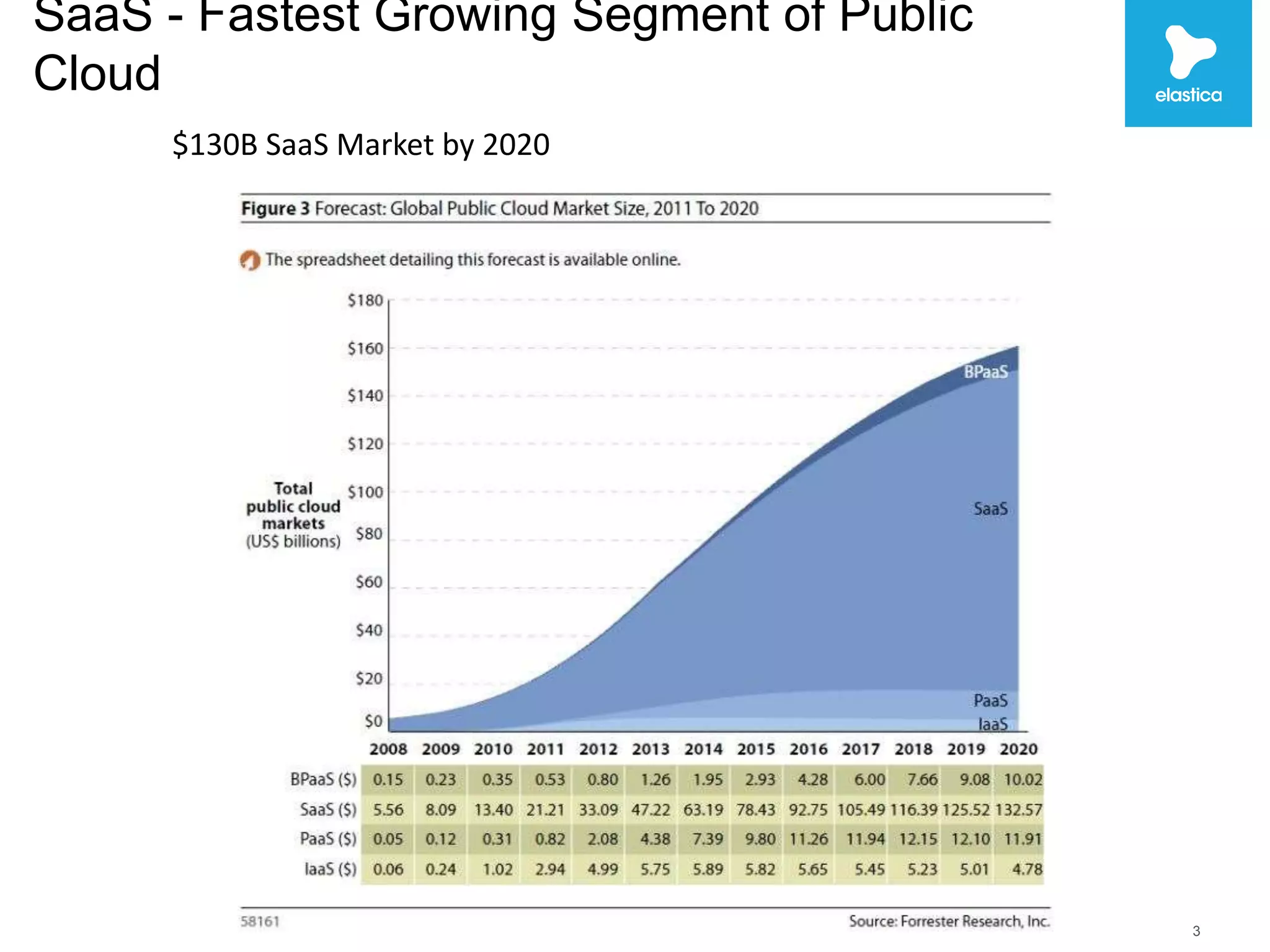
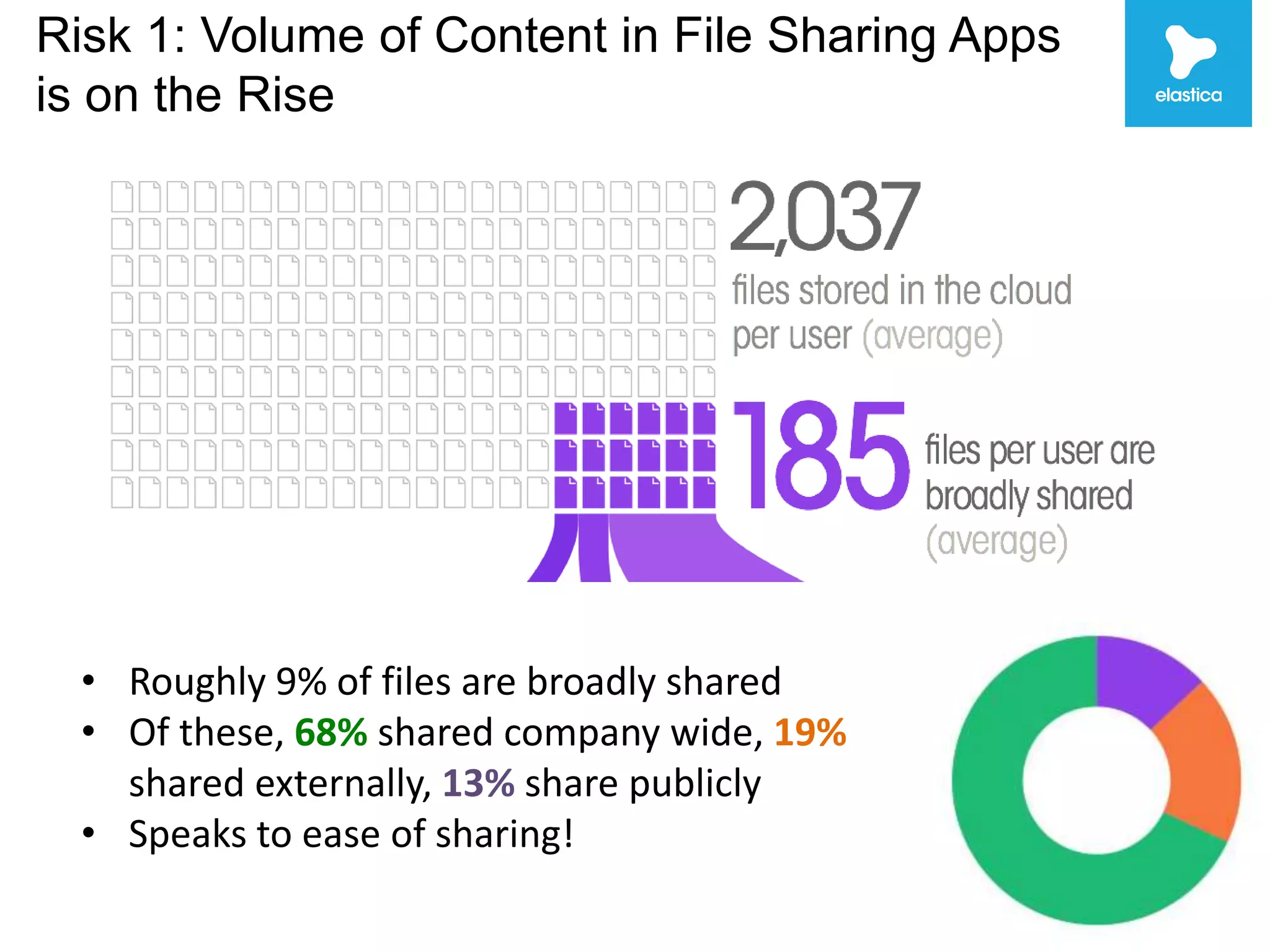
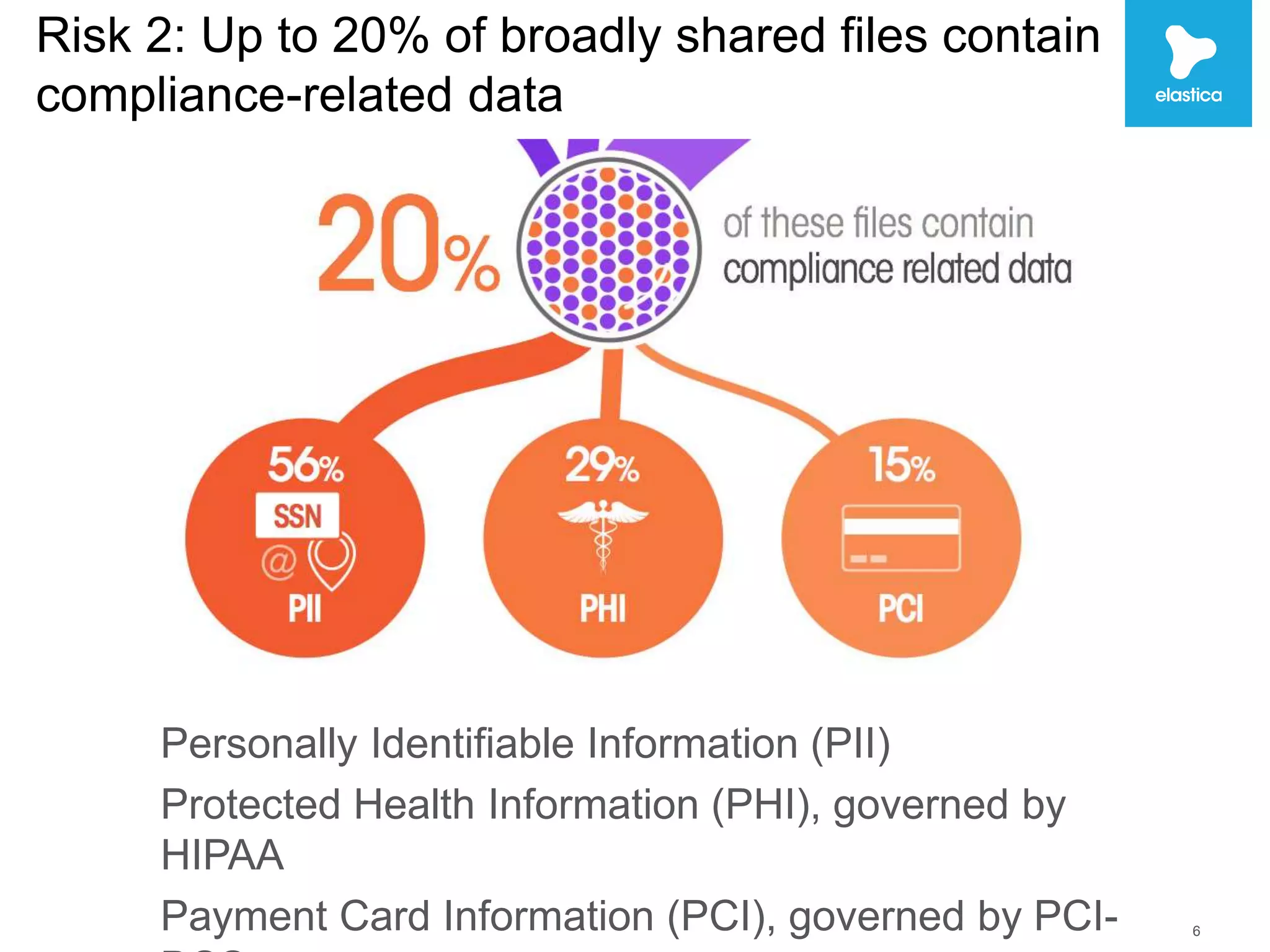
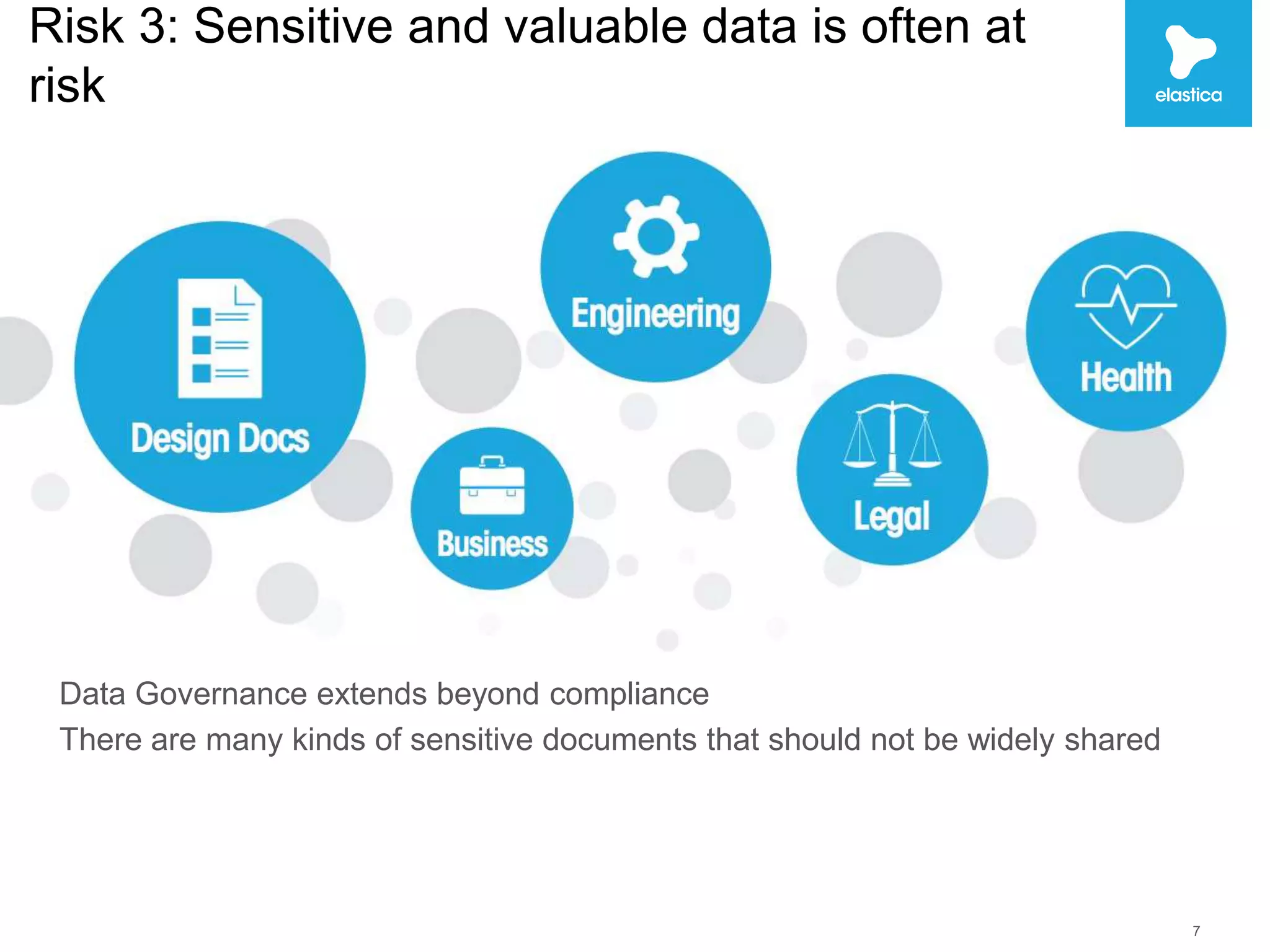
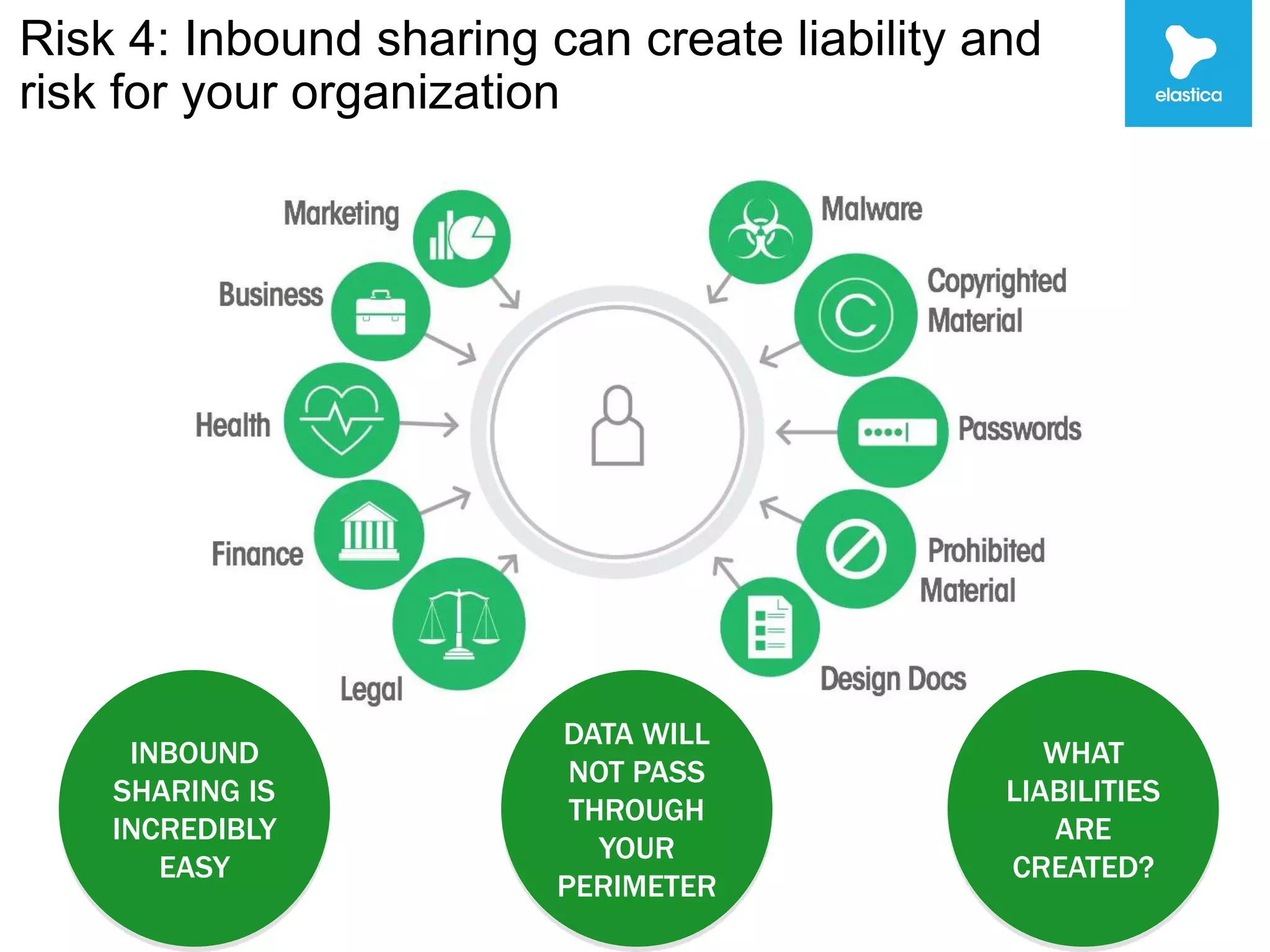
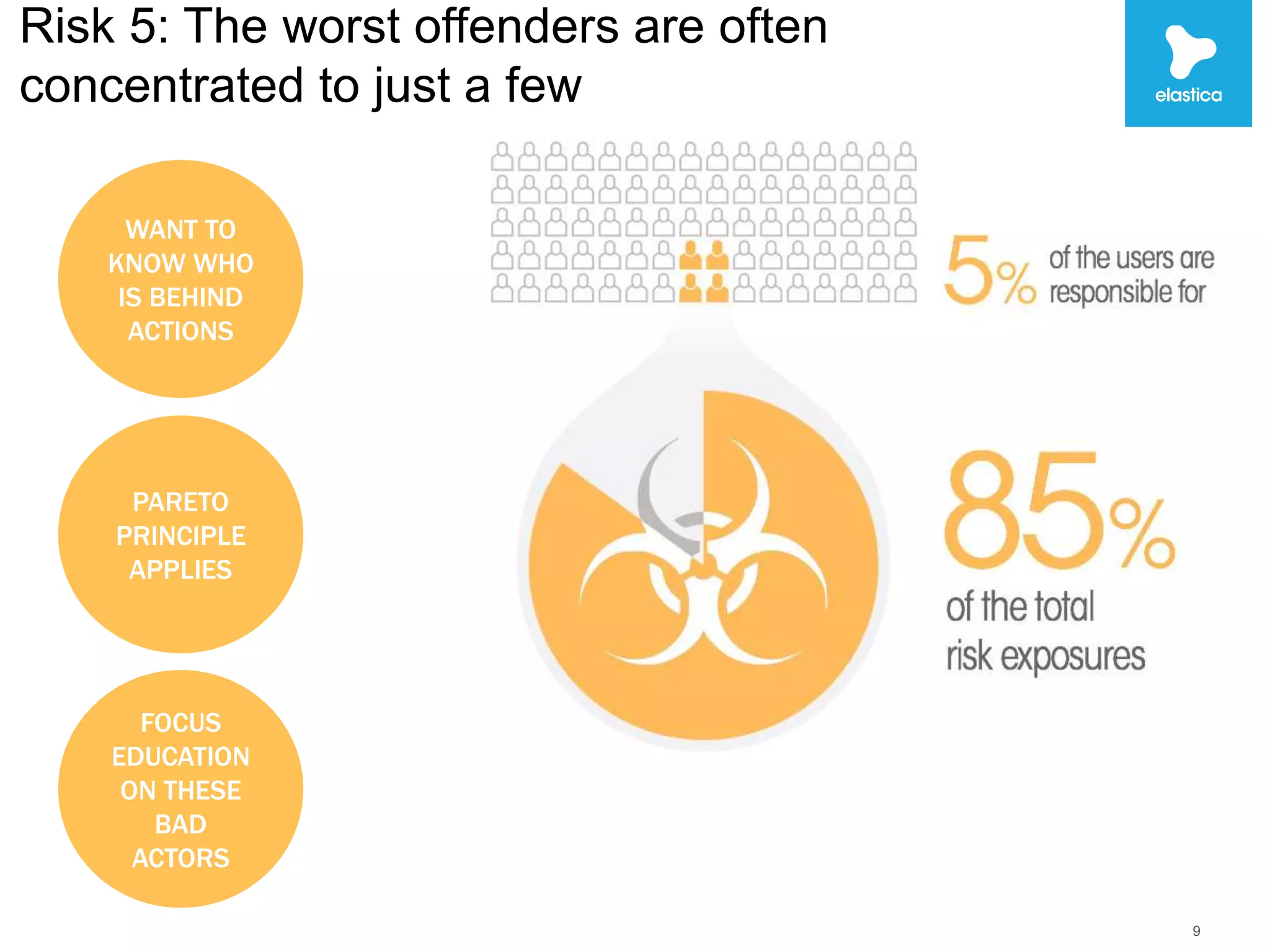
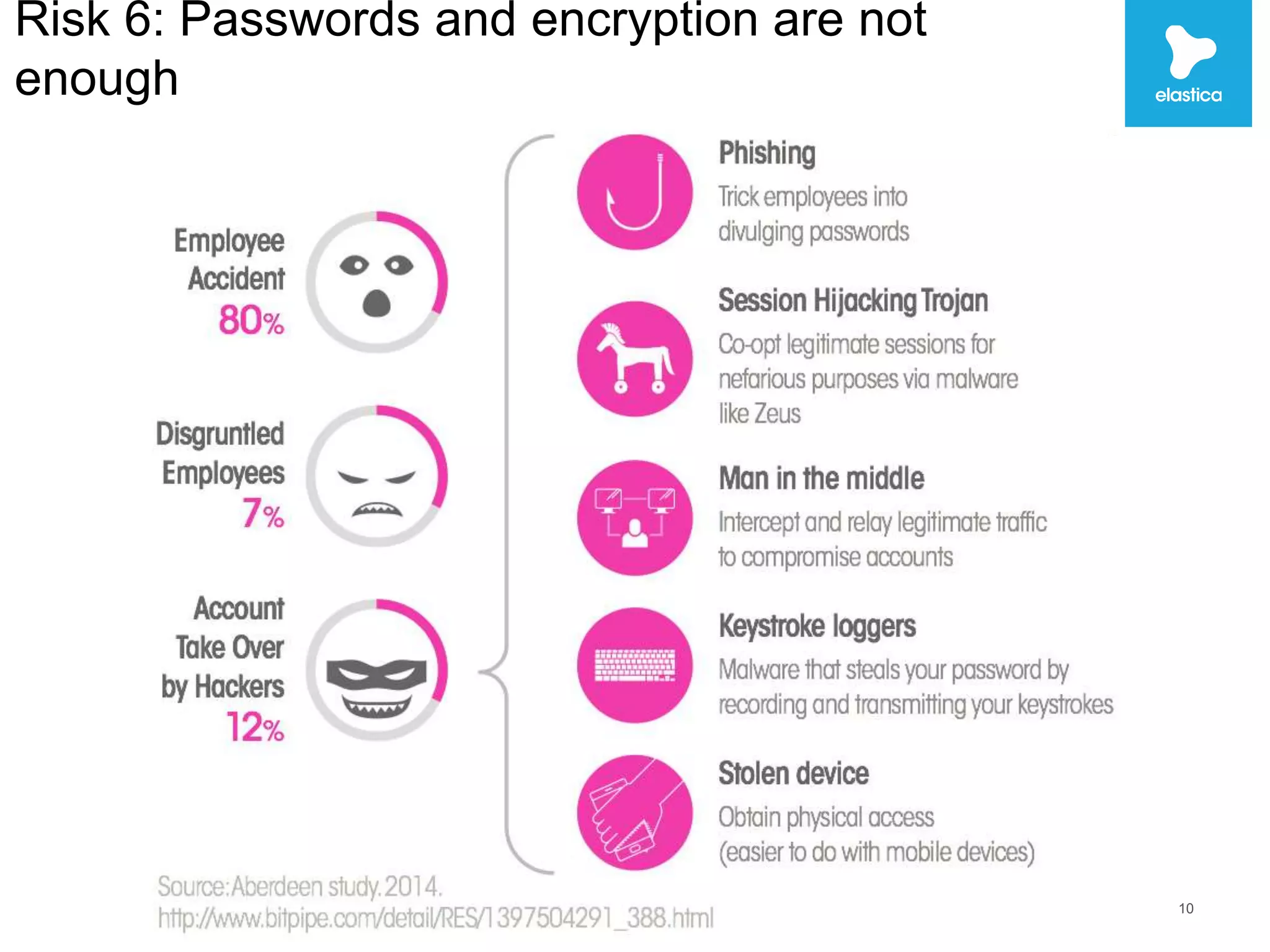
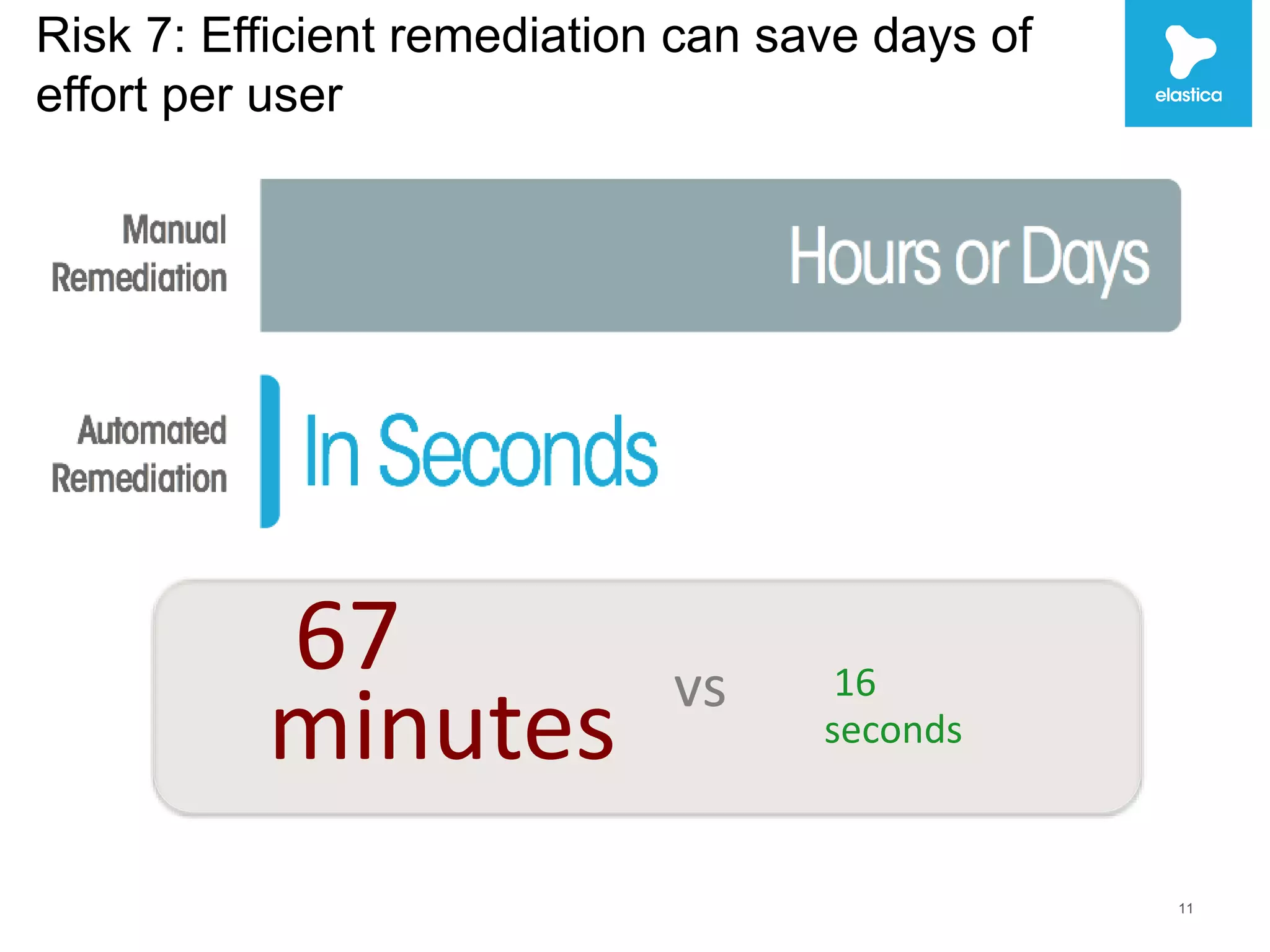
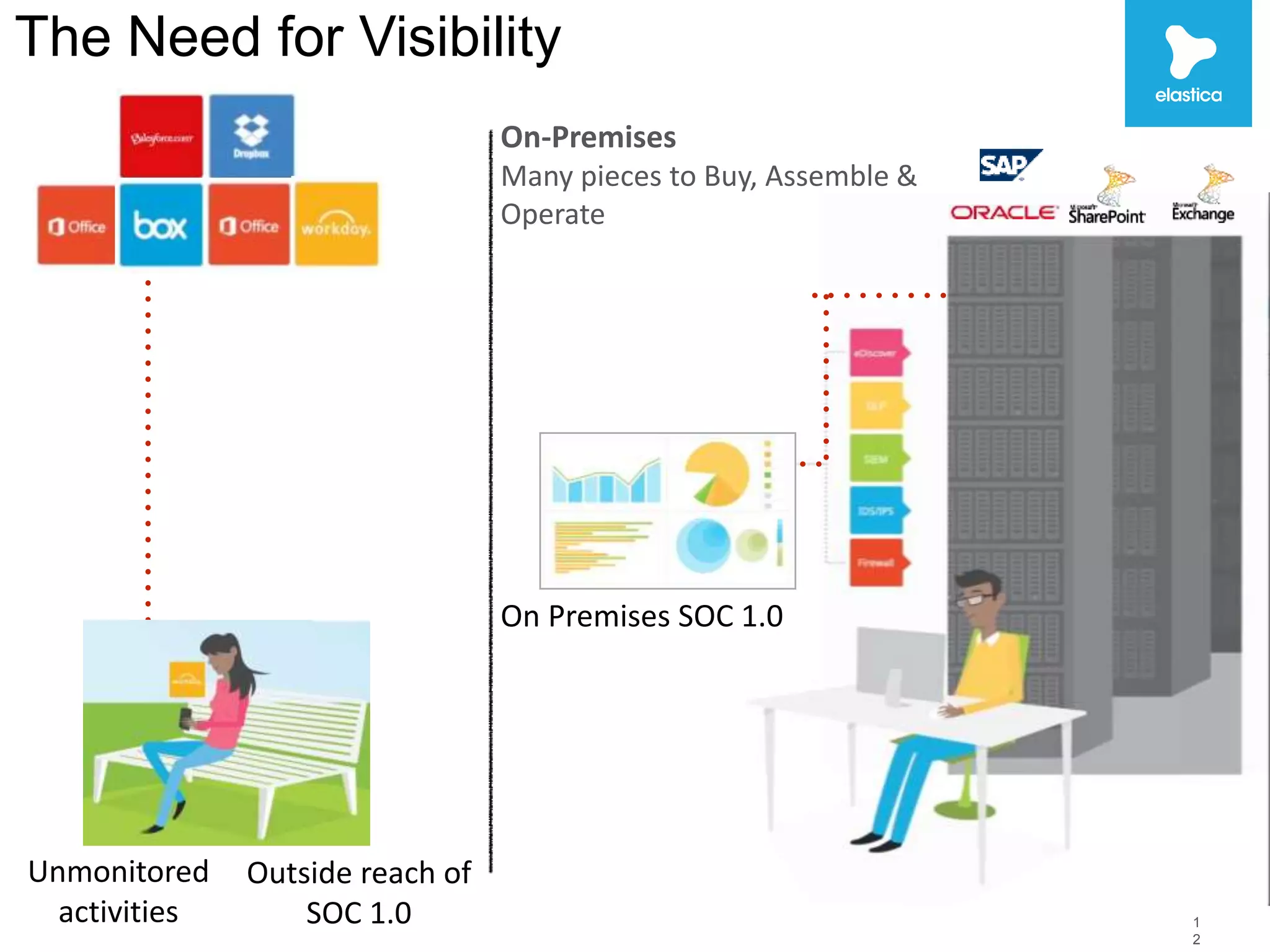
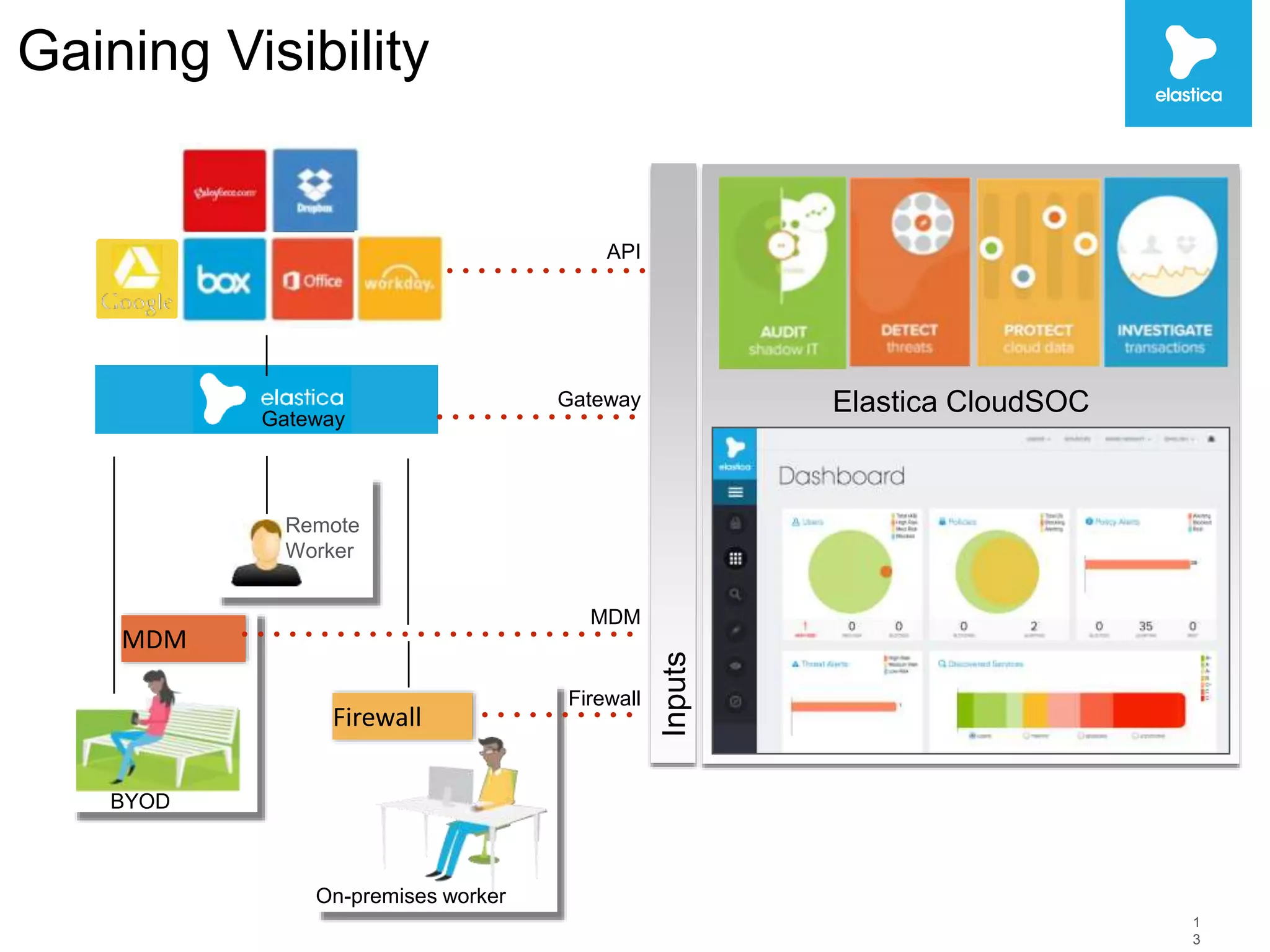
The document discusses the risks associated with shadow data, which refers to sensitive data stored on cloud services by employees without organization oversight. Through analyzing over 100 million files on cloud file sharing services, the author identified 7 main risks: 1) the volume of shared content is rising, 2) up to 20% of broadly shared files contain compliance-related data, 3) sensitive data is often at risk, 4) inbound sharing can create liability, 5) a small number of users are responsible for most risks, 6) passwords and encryption are not sufficient, and 7) efficient remediation can save significant time per user. The author argues this shadow data and lack of visibility present challenges for organizations.